You can control keystroke (I/O) logging behavior using the following policy variables.
Table 21: Keystroke logging policy variables
| iolog |
string |
The name of the file in which input, output, and error output is logged. This must be a full pathname starting with a / (slash). To avoid overwriting existing I/O log files, set the iolog variable with a mktemp function call. |
| iolog_encrypt |
boolean |
Enables encryption of I/O logs: To enable encryption, set: iolog_encrypt = true;
Log files are encrypted with AES; view them with pmreplay. |
| iolog_errmax |
integer |
Limits the amount of text logged for stderr for each command. |
| iolog_opmax |
integer |
Limits the amount of text logged for stdout for each command. For example, if iolog_opmax is set to 500 and you enter: cat filename1
it only logs the first 500 bytes of output produced by this command. |
| log_passwords |
boolean |
Specifies whether passwords are logged to the keystroke log. The default setting logs passwords. See log_passwords for details. |
| logstderr |
boolean |
Specifies if error output is logged; default is "true". |
| logstdin |
boolean |
Specifies whether input is logged; default is "true". |
|
logstdout |
boolean |
Specifies whether output is logged; default is "true". |
All boolean values default to "true".
Example
iolog=mktemp(”/opt/quest/qpm4u/logs/”+”user”+”_”+basename(command)
+”_XXXXXX”);
iolog_encrypt = true;
iolog_opmax = 500;
iolog_errmax = 200;
logstderr = false;
logstdin = true;
logstdout = true;
log_passwords = false;
For details about the keystroke logging variables, refer to Global output variables.
Privilege Manager for Unix can configure central logging for I/O and event logs using the iologhost and eventloghost policy variables.
pmmasterd uses port number 12345 by default to communicate with the log server.
A host that is configured as a centralized log server must have the client's keyword added to the pm.settings file to specify which policy servers may forward their I/O and event log information to this log server.
Figure 9: Configuring central logging for I/O and event Logs
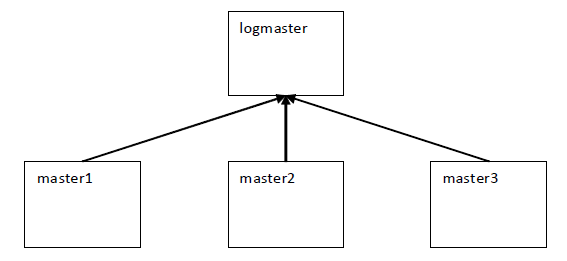
In this example, master1, master2, master3, and logmaster are all Privilege Manager for Unix policy servers (pmmasterd).
logmaster is configured as the centralized log host for I/O and event logs for master1, master2 and master3. To send I/O and event log information to logmaster, the policy must include the following statements:
iologhost = "logmaster";
eventloghost = "logmaster";
If for any reason (such as a system outage) the logs cannot be forwarded to the central logging host (logmaster in the above example), log files are stored locally on the authenticating policy server (master1, master2, or master3 in the above example). The location of the log files is specified by the tmplogdir policy variable, which defaults to var/opt/quest/qpm4u/iolog/queue.
The pm.settings file for logmaster must include the clients keyword. For example:
clients master1 master2 master3
Related Topics
PM settings variables
tmplogdir
An effective strategy for controlling the size of the log file in Privilege Manager for Unix is to limit the amount of information sent to the logs. Instead of logging keystrokes for every command, you might construct a policy that only captures keystrokes for sensitive commands.
You can use policy variables to limit the information sent to the log files.
Table 22: Size-controlling logging variables
| iolog_encrypt |
boolean |
Enables I/O logs encryption; default is "true".
Log files are encrypted with AES; view them with pmreplay. |
| iolog_errmax |
integer |
Limits the amount of text logged for stderr for each command. |
| iolog_opmax |
integer |
Limits the amount of text logged for stdout for each command. For example, if iolog_opmax is set to 500 and you enter the following command: cat filename1 it only logs the first 500 bytes of output produced by this command. |
| logomit |
list |
Specifies the names of variables to omit when logging to an event log (no default). Use this to reduce the amount of disk space used by event logs. |
| logstderr |
boolean |
Specifies if error output is logged; default is "true". |
| logstdin |
boolean |
Specifies whether input is logged; default is "true". |
|
logstdout |
boolean |
Specifies whether output is logged; default is "true". |
If you are running Privilege Manager for Unix, you can view events using Management Console for Unix, which provides an intuitive web-based console for managing UNIX hosts.
Refer to the One Identity Management Console for Unix Administration Guide for details about using the mangement console.

