How SPS and RADIUS work together in detail
Figure 2: How SPS and RADIUS server work together
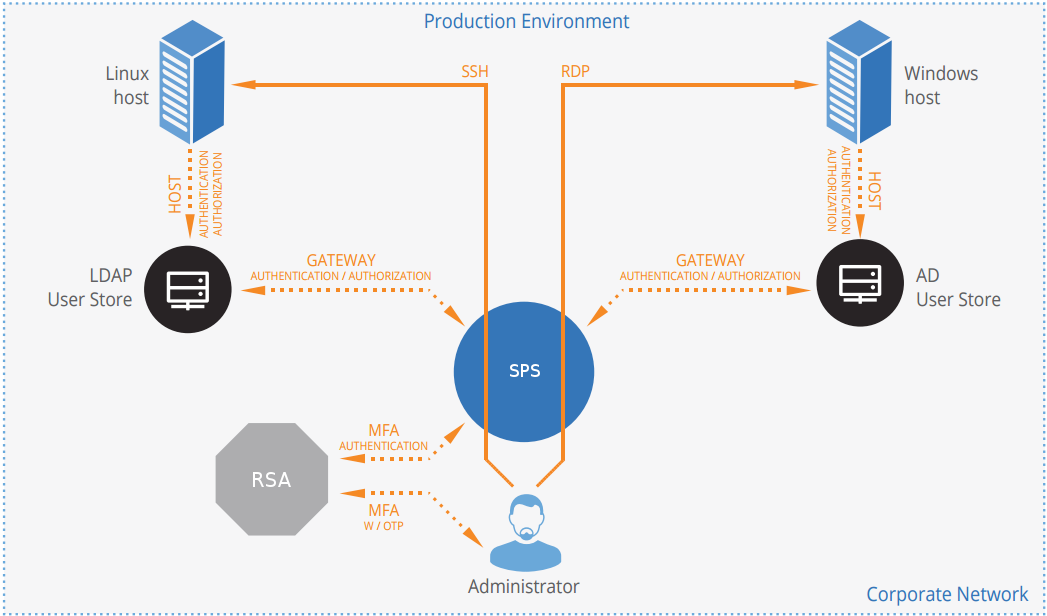
-
A user attempts to log in to a protected server.
-
Gateway authentication on SPS
SPS receives the connection request and authenticates the user. SPS can authenticate the user to a number of external user directories, (for example, LDAP, Microsoft Active Directory, or RADIUS). This authentication is the first factor.
-
Check if the user is exempt from multi-factor authentication
You can configure SPS using whitelists and blacklists to selectively require multi-factor authentication for your users, (for example, to create break-glass access for specific users).
-
If multi-factor authentication is not required, the user can start working, while SPS records the user's activities. The procedure ends here.
-
If multi-factor authentication is required, SPS continues the procedure with the next step.
For details on creating exemption lists, see [WHITELIST].
-
-
Determining the RADIUS username
If the gateway usernames are different from the RADIUS usernames, you must configure the SPS RADIUS plugin to map the gateway usernames to the RADIUS usernames. The mapping can be as simple as appending a domain name to the gateway username, or you can query an LDAP or Microsoft Active Directory server. For details, see [USERMAPPING].
-
Authentication using a RADIUS server
If gateway authentication is successful, SPS connects to the RADIUS server. Then SPS requests the second authentication factor from the user and sends it to the RADIUS server for verification.
-
If multi-factor authentication is successful, the user can start working, while SPS records the user's activities. (Optionally, SPS can retrieve credentials from a local or external Credential Store or password vault, and perform authentication on the server with credentials that are not known to the user.)
Alternatively, the RADIUS server can request Access-Challenge response. The challenge is displayed to the user and they have to respond to the challenge. After a successful response, the user can start working. In RSA SecurID, this process is used for next token mode. This means that if the password is entered incorrectly several times, two subsequent RSA SecurID tokens have to be entered for a successful authentication.
-
If the user opens a new session within a short period, they can do so without having to perform multi-factor authentication again. After this configurable grace period expires, the user must perform multi-factor authentication to open the next session. For details, see [authentication_cache].
