Connection logs
The connection logs contain all connection-related information of the past week, one file per day. A file contains all logs for all connections for a single day.
The logging level of One Identity Safeguard for Privileged Sessions (SPS) can be set separately for every protocol. To change the verbosity level of SPS, navigate to Traffic Controls > Protocol name > Global Options.
These logs are accessible at /var/log/zorp-<protocol-name>-<day>.
NOTE: The verbosity level ranges from 1 (no logging) to 10 (extremely detailed), with level 4 being the default normal level. To debug complex problems, you might have to increase the verbosity level to 7. Higher level is needed only in extreme cases.
|

|
Caution:
High verbosity levels generate very large amount of log messages and might result in a very high load on the machine.
For log levels 8-10, the logs contain highly sensitive data for all connections, as well as passwords and private keys in plain text format. |
The connection logs are used for
The connection logs contain the following
Core dump files
One Identity Safeguard for Privileged Sessions (SPS) automatically generates core dump files if an important software component (for example, Zorp) of the system crashes for some reason. These core dump files can be of great help to the One Identity Support Team to identify problems. When a core dump file is generated, the SPS administrator receives an alerting e-mail, and an SNMP trap is generated if alerting is properly configured (for details, see Configuring system monitoring on SPS and System logging, SNMP and e-mail alerts).
To list and download the generated core dump files, navigate to Basic Settings > Troubleshooting > Core files.
For details on core dump files, see: Gathering data about system problems.
The core dump files are used for
The core dump files contain the following
Maximizing the scope of auditing
In certain special scenarios, One Identity Safeguard for Privileged Sessions (SPS) may examine and audit network traffic with some limitations, depending on the configuration.
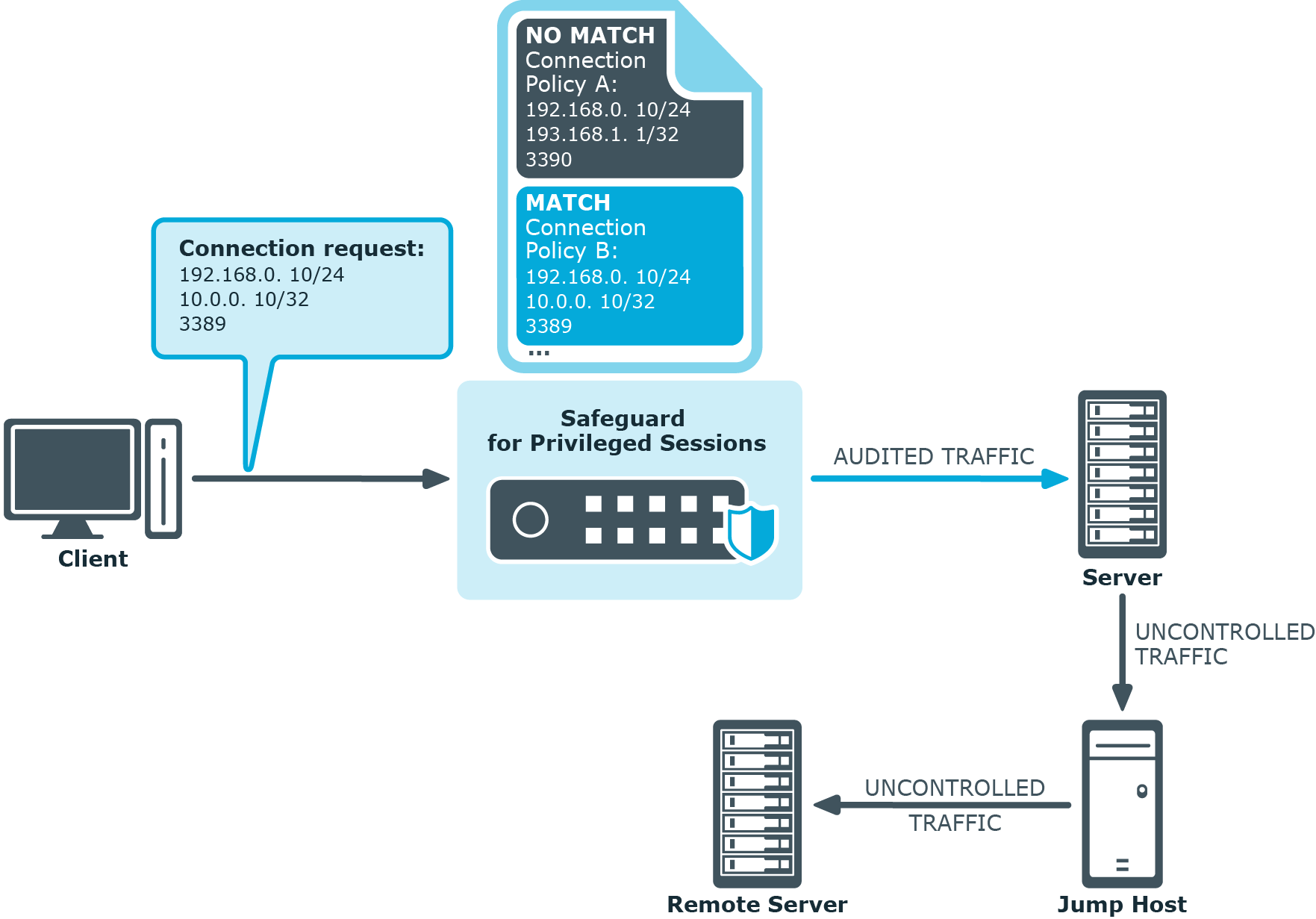
In the first scenario, your organization uses jump hosts to access remote servers or services. In this case, SPS ignores the connection between the target server and the remote server, as it does not go through SPS.
Figure 13: Connection to a remote server through a jump host
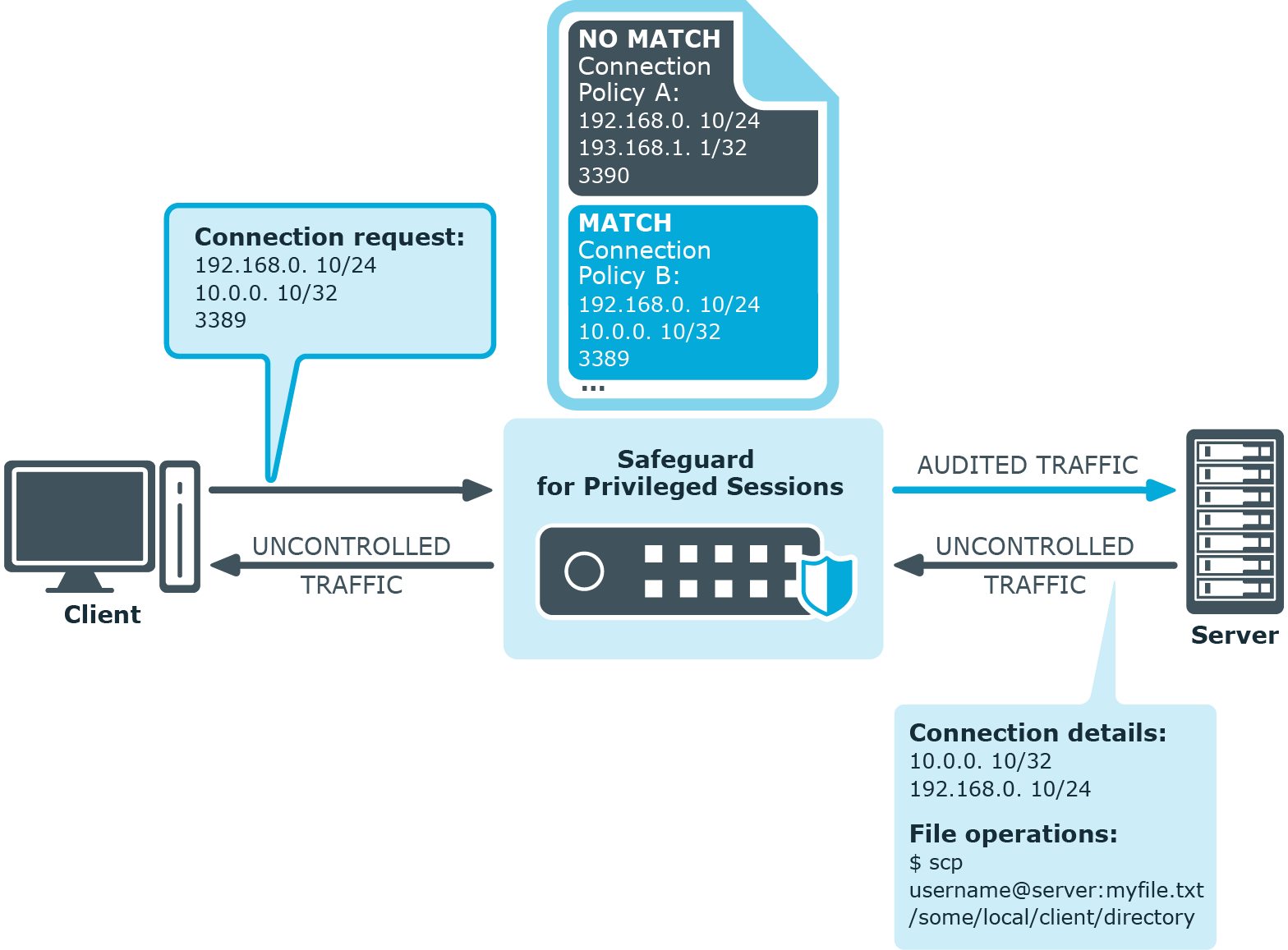
In the next scenario, a file operation is performed going from the target server to the client (for example, copying a file using SCP). In this case, the direction of the connection is switched, as compared to the initial client-to-server direction.
Figure 14: File operation in the "reverse" direction
In these scenarios, SPS may not:
-
Restrict channels allowed in the connection.
-
Audit file operations.
When you wish to search for the audit files of these connections, there will be no results returned on the Sessions page.
-
Allow authentication on the remote server if the user authenticates to the target server using a Credential Store.
If you want all connections in these scenarios to be audited, make sure that you add a connection policy for:
IPv6 in One Identity Safeguard for Privileged Sessions (SPS)
One Identity Safeguard for Privileged Sessions (SPS) supports IPv6 for monitoring connections only. You can define both IPv4 and IPv6 addresses for its logical network interfaces, and configure connections between IPv4 and IPv6 networks (for example, from a client with an IPv4 address to a target with an IPv6 address). You can also use IPv6 addresses with inband destination selection.
NOTE: IPv6 support in ICA connections is currently experimental only.
When configuring IPv6 addresses, SPS shortens the address to its canonical form (omitting leading zeroes, and replacing consecutive sections of zeroes with a double colon). Take the following address as an example:
2001:0db8:0000:0000:0000:ff00:0042:8329
SPS shortens the address to its canonical form:
[2001:db8::ff00:42:8329]
Additionally, where the IP address and the port is displayed together, IPv6 addresses are shown between brackets. For example, the same address with a port number of 443 is displayed as:
[2001:db8::ff00:42:8329]:443
You can search for both the initial (full) and the canonical form on the SPS Search page.
To provide the network range for IPv6 addresses, use network prefixes. Pay attention to the differences between IPv4 and IPv6 network ranges: for IPv4, you can limit the address range to a single address with a prefix of /32, but to achieve the same on an IPv6 network, you have to use set the prefix to /128.



