To access protected website
- Using any supported browser, access the protected website. On the Login page, enter your user name and click Sign in.
- In the example below, users are required to authenticate themselves by entering their passcode. The authentication type depends on how the Defender policy has been configured. For example, if Defender is configured to use a token policy, the Enter Synchronous Response prompt will be displayed.
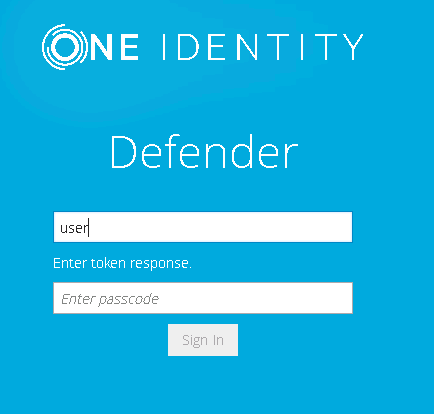
- If users have entered a valid response, they will be authenticated and permitted to access the website.