Entry type: Mask
Entry type: Mask
When you select Mask under Entry type in the Add Entry window, the Entry properties area looks like the following figure.
Figure 52: Add Entry: Mask
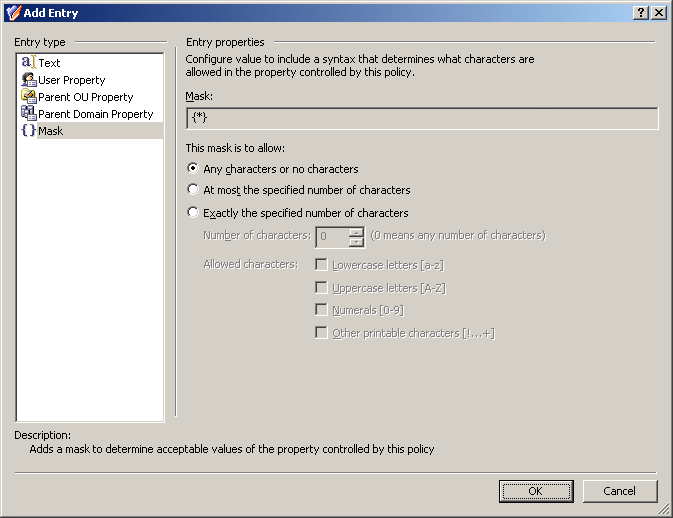
With this entry type, you can define which characters (letters, numerals) are acceptable in the entry you add to the value of the controlled property.
If you want to allow the entry to include any series of characters, click Any characters or no characters.
If you want to specify a maximum number of allowed characters the entry may include, click At most the specified number of characters. In the Number of characters box, specify the number of allowed characters. The entry may include any number of characters not exceeding the specified number. Under Allowed characters, select check boxes to specify the allowed characters.
If you want to specify an exact number of allowed characters that the entry must include, click Exactly the specified number of characters. In the Number of characters box, specify the number of allowed characters. The entry must include exactly the specified number of characters. Under Allowed characters, select check boxes to specify the allowed characters.
When you are done configuring an entry, click OK to close the Add Entry window. The entry is added to the Configure Value dialog box.
Steps for configuring a Property Generation and Validation policy
To configure a Property Generation and Validation policy via the Active Roles MMC console, perform the following procedure.
To configure a Property Generation and Validation policy
-
Navigate to Configuration > Policies > Administration.
-
To open the New Provisioning Policy Object Wizard dialog, right-click in the middle pane to open the context menu, and then select New > Provisioning Policy.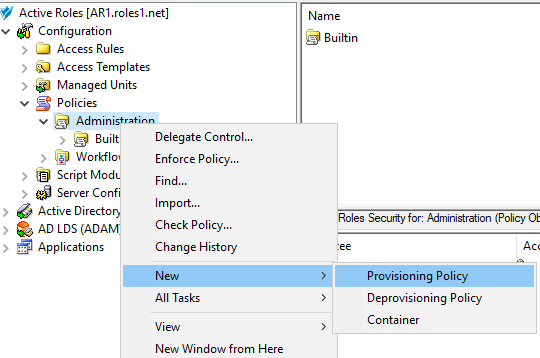
-
On the Name and Description page, provide a unique Name for the new policy object. Optionally, also provide a Description. To continue, click Next.
-
On the Policy to Configure page, select Property Generation and Validation, and then click Next.
-
On the Controlled Property page, click Select to open the Select Object Type and Property dialog.
-
To select the object type and its object property you want the policy to control, use the settings of the Select Object Type and Property dialog:
-
Use the Object type drop-down menu to select the object type whose property you want to provision.
-
Use either the Look for Property search box to manually search for the object property you want to provision, or browse it in the Object Property list.
TIP: If you do not see the object type you need, expand the list by selecting Show all possible object types.
NOTE: Policy Object settings specific to Azure cloud-only objects (such as cloud-only Azure users, guest users, or contacts) are available only if your Active Roles deployment is licensed for managing cloud-only Azure objects. Contact One Identity support for more information.
Also, Policy Objects specific to Azure cloud-only objects will work correctly only if an Azure tenant is already configured in the AD of the organization, and Active Roles is already set as a consented Azure application for that Azure tenant. For more information on these settings, see Configuring a new Azure tenant and consenting Active Roles as an Azure application.
-
Once you selected the object and property, click OK to continue.
-
On the Configure Policy Rule page, specify the condition(s) you want to configure for the policy by selecting them in the Select conditions to configure policy rule list. The selected conditions then appear in the Edit policy rule text box.
-
(Optional) If the selected condition supports editing, then click the underlined part of the condition to open the Add Value dialog and edit its settings.
To specify additional configuration for the condition, enter a variable into the Value field, then click OK to close the Add Value dialog.
Alternatively, click Configure Value, then click Add, and configure an entry manually in the Add Entry dialog. For more information on manual configuration, see Steps for configuring entries. To close the Add Value dialog, click OK.
-
(Optional) If multiple conditions are selected, switch between the AND and OR logic of the condition relations by clicking and or or.
-
After selecting and configuring the condition(s), click Next.
-
(Optional) On the Policy Description page, modify the default description of the policy generated by the wizard. To do so, select Modify this policy description to make the description editable. Modify the description, then click Next.
-
On the Enforce Policy page, specify the objects to which the configured Policy Object will be applied. Click Add, and then use the Select Objects dialog to locate and select the objects.
TIP: When provisioning cloud-only Azure users or guest users, you can either select the respective object category (such as the Azure user or Azure guest user node) in this step, or the Azure tenant that contains the Azure objects.
- Click Next and then Finish to complete creating the Policy Object.
Steps for configuring entries
Use the following step-by-step instructions to configure an entry in the Add Entry dialog box. The same instructions apply when you are making changes to an existing entry.
To configure a Text entry
- Under Entry type, click Text.
Use a Text entry to add a text string to the value you are configuring.
- In Text value, type the text string you want the value to include.
- Click OK.
To configure an <Object> Property entry
- Under Entry type, click <Object> Property.
Use an <Object> Property entry when configuring a value to include a certain property (or a part of a property) of the object that is under the control of the policy. In these instructions, <Object> stands for the type of object, such as User, Group, or Computer.
- Click Select, click the property to include in the value, and then click OK.
- If you want the entry to include the entire value of the property, click All characters of the property value. Otherwise, click The first, and specify the number of characters to include in the entry.
- If you selected The first, then, optionally, select If value is shorter, add filling characters at the end of value, and type a character in Filling character.
This character will fill the missing characters in the value of the property if the value is shorter than specified in the box next to The first.
- Click OK.
To configure a Parent OU Property entry
- Under Entry type, click Parent OU Property.
Use a Parent OU Property entry when configuring a value to include a certain property (or a part of a property) of an organizational unit (OU) in the hierarchy of containers above the object being managed by the policy.
- Click Select, click the property to include in the value, and then click OK.
- If you want the entry to include the entire value of the property, click All characters of the property value. Otherwise, click The first, and specify the number of characters to include in the entry.
- If you selected The first, then, optionally, select If value is shorter, add filling characters at the end of value, and type a character in Filling character.
This character will fill the missing characters in the value of the property if the value is shorter than specified in the box next to The first.
- Choose one of these options:
- To use the property of the OU in which the object resides, click Immediate parent OU of the object being managed by this policy.
- To use the property of a parent OU of a different level, click More distant parent OU and then, in Level, specify the level of the OU.
Lower level means greater distance from the managed object in the hierarchy of containers above that object. OU level 1 is an immediate child OU of the domain.
- Click OK.
To configure a Parent Domain Property entry
- Under Entry type, click Parent Domain Property.
Use a Parent Domain Property entry when configuring a value to include a certain property (or a part of a property) of the domain of the object being managed by the policy.
- Click Select, click the property to include in the value, and then click OK.
- If you want the entry to include the entire value of the property, click All characters of the property value. Otherwise, click The first, and specify the number of characters to include in the entry.
- If you selected The first, then, optionally, select If value is shorter, add filling characters at the end of value, and type a character in Filling character.
This character will fill the missing characters in the value of the property if the value is shorter than specified in the box next to The first.
- Click OK.
To configure a Mask entry
- Under Entry type, click Mask.
Use a Mask entry when configuring a value to include a syntax that determines how many and what characters are allowed in the property controlled by the policy.
- Select one of these options:
- Any characters or no characters to allow the entry to include any series of characters.
- At most the specified number of characters to specify a maximum number of allowed characters the entry may include.
- Exactly the specified number of characters to specify an exact number of allowed characters that the entry must include.
- If you selected the second option or the third option in Step 2, do the following:
- In Number of characters, specify the how many characters are allowed in this entry.
If you selected the second option, the entry may include any number of characters not exceeding the number specified.
If you selected the third option, the entry must include exactly the specified number of characters.
- Under Allowed characters, select check boxes to specify what characters are allowed in this entry.
- Click OK.
To configure a Date and Time entry
- Under Entry type, click Date and Time.
Use a Date and Time entry when configuring a value to include the date and time of the operation performed by the policy (for example, the date and time when the user was deprovisioned).
- In the list under Date and time format, click the date or time format you want.
- Click OK.
To configure an Initiator ID entry
- Under Entry type, click Initiator ID.
Use an Initiator ID entry when configuring a value to include the ID of the Initiator, that is, the user who initiated the operation performed by the policy (for example, the ID of the user who initiated the deprovisioning operation). You can build the Initiator ID based on a combination of properties of the Initiator.
- Select one of these options:
- User logon name (pre-Windows 2000) of the Initiator, in the form Domain\Name to set the Initiator ID to the pre-Windows 2000 user logon name of the Initiator.
- User logon name of Initiator to set the Initiator ID to the user logon name of the Initiator.
- Initiator ID built using a custom rule to compose the Initiator ID of other properties specific to the Initiator.
- If you selected the third option in Step 2, click Configure, and use the Configure Value dialog box to set up the value to be used as the Initiator ID: Click Add and specify the entries for the value as appropriate.
You can configure entries of these categories: Text (any text string), Initiator Property (a certain property of the Initiator user object), Parent OU Property (a certain property of an organizational unit that holds the Initiator user object), Parent Domain Property (a certain property of the domain of the Initiator user object). To configure entries, use the instructions that are given earlier in this topic.
- Click OK.
To configure a Uniqueness Number entry
- Under Entry type, click Uniqueness Number.
Use a Uniqueness Number entry when configuring a value to include a number the policy will increment in the event of a naming conflict. For example, in a policy that generates a user logon name or email alias, you can add an entry of this category to the generation rule in order to ensure the uniqueness of the name or alias generated by the policy.
- Click one of these options:
- Add always. The value includes this entry regardless of whether or not the policy encounters a naming conflict when applying the generation rule
- Add if the property value is in use. The policy adds this entry to the value in the event of a naming conflict; otherwise the value does not include this entry.
- Specify how you want the entry to be formatted:
- To have the entry formatted as a variable-length string of digits, clear the Fixed-length number, with leading zeroes check box. In most cases, this will result in a single-digit entry.
- To have the entry formatted as a fixed-length string of digits, select the Fixed-length number, with leading zeroes check box, and then specify the number of digits you want the string to include. This will result in an entry prefixed with the appropriate number of zeroes, such as 001, 002, 003.
- Click OK.
|

|
NOTE:
|
Scenario 1: Using mask to control phone number format
This scenario describes how to configure a policy that forces the user phone number to conform to the format (###) ###-##-##.
To implement this scenario, you must perform the following actions:
- Create and configure a Policy Object that defines the appropriate policy.
- Apply the Policy Object to a domain, OU, or Managed Unit.
As a result, when creating or modifying a user object in the container you selected in Step 2, Active Roles checks whether the phone number conforms to the stated format. If not, the policy disallows the creation or modification of the user object.
The following two sections elaborate on the steps to implement this scenario.



