The key features of Active Roles are as follows:
-
Support for two operation modes: can be configured to operate in proxy mode or in direct access mode. In proxy mode, accesses Active Directory or Active Directory Lightweight Directory Services (AD LDS, formerly known as ADAM) through Active Roles used as a proxy service, while in direct access mode, directly accesses Active Directory or AD LDS.
-
Support for equivalent LDAP operations: can perform equivalent LDAP operations such as addRequest, modifyRequest, deleteRequest, and lookupRequest.
-
Support for Azure AD, AD, and AD LDS data management: enables SPML-conformant applications to read from and write to Azure AD, Active Directory (AD), and AD LDS.
-
Search Capability support: allows SPML-enabled applications to search for relevant directory objects based on various search criteria.
-
Password Capability support: allows SPML-enabled applications to perform basic password management tasks such as setting and expiring user passwords.
-
Suspend Capability support: allows SPML-enabled applications to effectively enable, disable and deprovision user accounts in Active Directory.
-
Flexible Configuration options: There is support for many different configuration options that enable the administrator to adjust the behavior and optimize the performance.
-
IIS Security Support: supports all IIS security configurations, including integrated Windows authentication, basic authentication, and basic authentication over Secure Sockets Layer (SSL).
-
Support for using Active Roles controls: In proxy mode, you can send Active Roles controls to the Active Roles Administration Service with an SPML request to perform an administrative operation. In your request, you can also define the Active Roles controls that the Administration Service must return in the SPML response.
can be used for a variety of purposes. Some common scenarios for using are as follows:
-
Non-Windows applications: The systems running non-Windows applications that need to communicate with Active Directory can do this through . For example, with , Unix applications can manage Unix-enabled user accounts in Active Directory. In proxy mode, allows existing SPML-compatible provisioning systems, such as SUN Java System Identity Manager and IBM Tivoli Directory Integrator to take advantage of the functionality of Active Roles.
-
Web services: The use of directories in Web services is growing rapidly. Additionally, XML is becoming the default language for use with Web services. fills the gap between XML documents and Active Directory services, enabling applications that must provide or use Web services to communicate with Active Directory.
-
Handheld and portable devices: Data-enabled cell phones or PDAs that need an access to directory data may not contain a client for the ADSI LDAP Provider but might be able to use the SPML communication protocol to access Active Directory over the Internet.
-
Firewall access: Certain firewalls cannot pass LDAP traffic because they cannot audit it, but these firewalls can pass XML. In such cases, applications can use to communicate with Active Directory across a firewall.
Active Roles operates based on the concepts defined in SPML v2. This section introduces and describes these key concepts and definitions as applied to .
A Client (Requesting Authority or Requestor) is any SPML-compliant application that sends well-formed SPML requests to the Active Roles and receives responses from it. Clients can include various business applications, such as human resources (HR) databases or Identity Management systems. There is no direct contact between a client and the target (Active Roles or an Active Directory server).
Active Roles (Provisioning Service Provider or PSP) is a Web service that uses the Simple Object Access Protocol (SOAP) over HTTP for communications. can directly access Active Directory data or communicate with Active Directory using the Active Roles proxy service. acts as an intermediary between a client and the target (Active Directory domain controller or Active Roles).
In proxy mode, Active Roles represents the Provisioning Service Target (or Target) that is available for provisioning actions through . The target has a unique identifier (targetID) that is maintained by and is used in a request or a response.
AD Objects (Provisioning Service Objects or PSO) represent directory objects that manages. A client can add, delete, modify, or look up a directory object. Each object has a unique identifier (PSO ID). In , an object DN is used as a PSO ID.
NOTE: The Requestor, Provisioning Service Provider, Provisioning Service Target, and Provisioning Service Objects are key notions described in the official SPML v2 specification.
For detailed information on the concepts defined in SPML v2, see Section 2 “Concepts” of the OASIS SPML v2 specification, available for download at http://www.oasis-open.org/specs/index.php#spmlv2.0.
With , applications can use SPML documents to look up, retrieve and update directory data in Active Directory, Azure AD, and AD LDS. converts XML elements and attributes into commands used to make changes to Active Directory and retrieve data from Active Directory. can also convert the response received from Active Roles or Active Directory to XML format. These conversions are based on and are in compliance with the OASIS SPML v2 - DSML v2 Profile specification.
runs as a Web application on a Web server running Microsoft Internet Information Services (IIS), and uses SOAP over HTTP to transmit and receive directory requests from client computers.
The environment includes the following components:
-
Clients that use SPML v2: These clients are applications that manage directory objects (for example, user accounts). A client issues SPML requests that describe operations to be performed on the directory object and send these requests to .
-
: Receives and processes client requests, and returns a response to the client.
-
Active Roles: In proxy mode, this is the endpoint for provisioning requests and the actual software that manages directory objects.
-
Active Directory, Azure AD, or AD LDS: In proxy mode, can access Active Directory or Azure AD domains and AD LDS instances that are registered with Active Roles as managed domains, Azure AD tenants, and managed AD LDS instances, respectively. In direct access mode, can access the domain controller or the AD LDS instance defined in the SPML.Config file. For more information, see “Configuring ” later in this document.
The following diagram illustrates the flow of requests and responses through the environment components:
Figure 149: Flow of requests and responses through the environment components
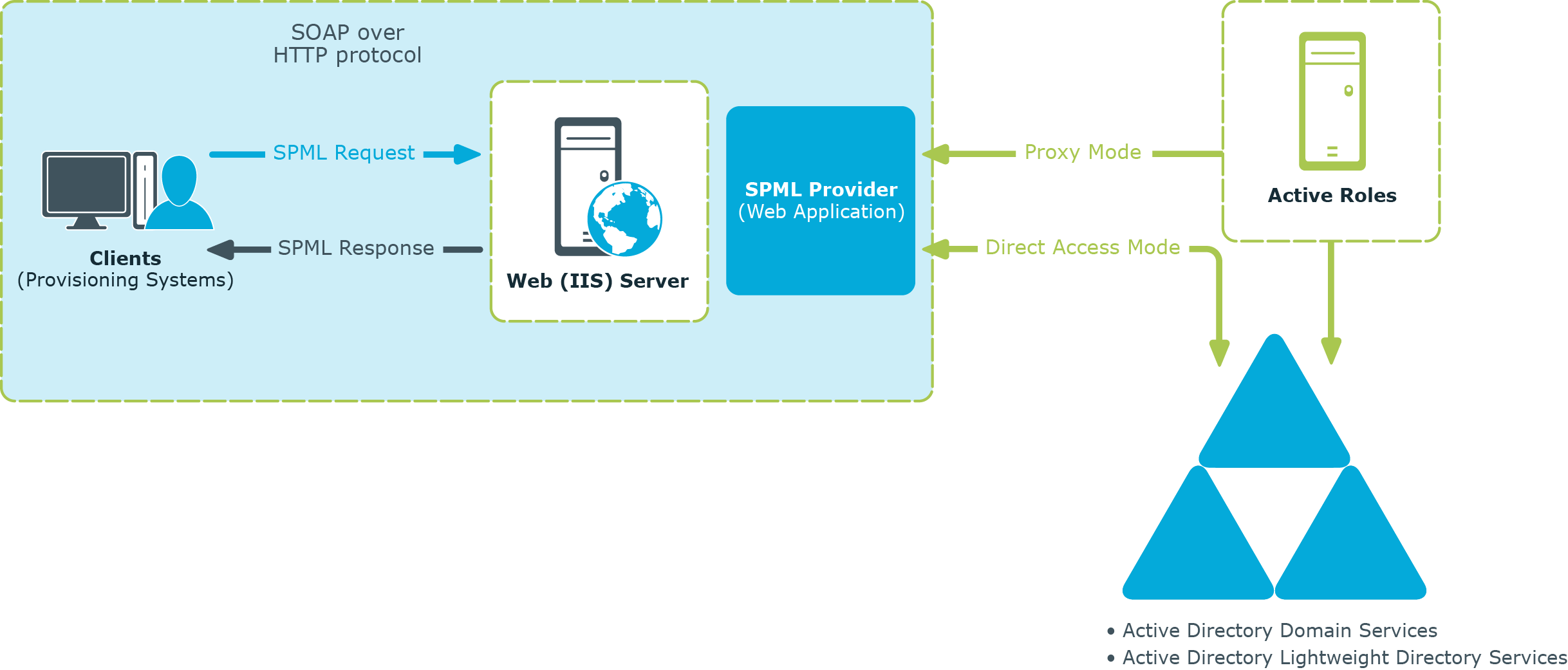
As shown in the diagram, the client/ communications are based on the simple request/response protocol.
In proxy mode, works in the following way:
-
A client issues a well-formed SPML request using the SOAP over HTTP protocol. This request goes to a server running IIS, where it is routed to .
-
examines the request for conformance to the SPML format.
-
If the request complies with the SPML format, the submits the request to Active Roles. Based on the client request, Active Roles retrieves or modifies data in Active Directory, Azure AD, or in AD LDS.
-
After performing the requested operation, Active Roles sends the result of the operation back to .
-
then processes this result data and sends the result of the performed operation back to the client in the form of an SPML response.
In direct access mode, works in the following way:
-
A client issues a well-formed SPML request using the SOAP over HTTP protocol. This request goes to a server running IIS, where it is routed to .
-
examines the request for conformance to the SPML format.
-
If the request conforms to the SPML format, retrieves or modifies the relevant data in Active Directory or in AD LDS (ADAM).
-
sends the result of the performed operation back to the client in the form of an SPML response.
If the client request does not conform to the SPML format, the client receives an SPML response that describes the encountered error.

