Preventing inheritance of individual business roles by identities, devices, or workdesks
Company resource inheritance for single roles can be temporarily prevented. You can use this behavior, for example, to assign all required company resources to a role. Inheritance of company resources does not take place, however, unless inheritance is permitted for the role, for example, by running a defined approval process.
To prevent inheritance for business roles
-
In the Manager, in the Organizations category, select a business role.
-
Select the Change main data task.
-
Set one or more of the following options:
-
To prevent identities from inheriting, set the Identities do not inherit option.
-
To prevent devices from inheriting, set the Devices do not inherit option.
-
To prevent workdesks from inheriting, set the Workdesks do not inherit option.
- Save the changes.
Related topics
Preventing inheritance by individual identities, devices, or workdesks
Inheritance of company resources can be prevented for single identities, devices, or workdesks. For example, you can use this behavior after importing to correct the imported data first and then apply inheritance afterward.
To prevent an identity from inheriting
-
In the Manager, select the identity in the Identities category.
-
Select the Change main data task.
-
Set the No inheritance option.
The identity does not inherit company resources through roles.
NOTE: This option does not have any effect on direct assignments. Company resource direct assignments remain assigned.
- Save the changes.
To prevent an device from inheriting
-
In the Manager, select the device in the Devices & Workdesks > Devices category.
-
Select the Change main data task.
-
Set the No inheritance option.
The device does not inherit company resources through roles.
NOTE: This option does not have any effect on direct assignments. Company resource direct assignments remain assigned.
- Save the changes.
To prevent a workdesk from inheriting
-
In the Manager, select the workdesk in the Devices & Workdesks > Workdesks category.
-
Select the Change main data task.
-
Set the No inheritance option.
The workdesk does not inherit company resources through roles.
NOTE: This option does not have any effect on direct assignments. Company resource direct assignments remain assigned.
- Save the changes.
Related topics
Inheritance exclusion: Specifying conflicting roles
You can define conflicting roles to prevent identities, devices, or workdesks from being assigned to several roles at the same time and from obtaining mutually exclusive company resources through these roles. At the same time, specify which business roles are mutually exclusive. This means you may not assign these roles to one and the same identity (device, workdesk).
NOTE: Only roles, which are defined directly as conflicting roles cannot be assigned to the same identity (device, workdesk). Definitions made on parent or child roles do not affect the assignment.
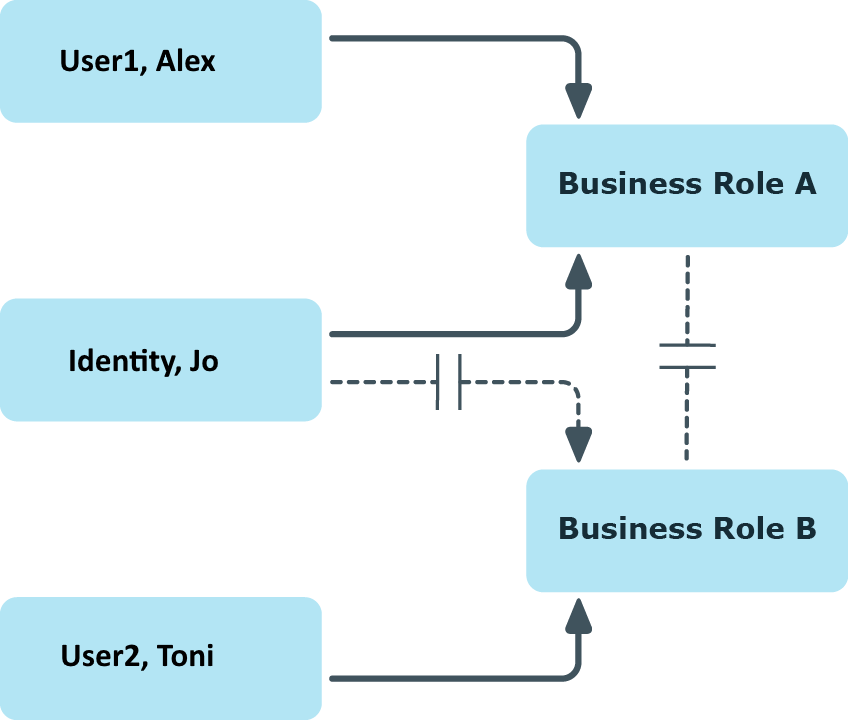
Example:
The business role B has been entered as conflicting role in business role Alex User1 and Jo Identity are members of business role A. Toni User2 is member of business role B. Jo Identity cannot be assigned to business role B. Apart from that, One Identity Manager also prevents Alex User1 from being assigned to business role B and Toni User2 to business role A.
Figure 12: Members in conflicting roles
To configure inheritance exclusion
Related topics
Restricting assignment of identities to multiple business roles
In certain circumstances you might want an identity to be assigned to only one business role such as, within a project structure.
To map this behavior, you can use the No multiple assignment of identities option. You can enable the option for role classes and role types.
-
If a role class has this option enabled, an identity can be assigned to only one business role of this role class. Assignment of the identity to other business roles belonging to this role class is not allowed.
-
If a role type has this option enabled, an identity can only be assigned one business role of this role type. Assignment of the identity to other business roles belonging to this role type is not allowed.
NOTE:
-
Only for direct assignments of identities to business roles are verified.
-
Use the Multiple role assignments despite IsPersonAssignOnce on OrgRoot and Multiple role assignments despite IsPersonAssignOnce on OrgType consistency checks to identify invalid assignments to business roles. These assignments can originate from dynamic roles or through purchase orders, for example. For more information about consistency checking, see the One Identity Manager Operational Guide.
-
If an identity has already been assigned to multiple business roles of a role class or role type, then the option cannot be set again for this role class or role type.
Related topics

