Overview
One Identity Defender AD FS Adapter integrates with Microsoft Active Directory Federation Services (AD FS) to add Two-Factor authentication to services using browser-based federated logins. Defender AD FS Adapter supports relying parties that use Microsoft WS-Federation protocol, such as Office 365, and SAML 2.0 federated logons for cloud apps such as Google Apps, and salesforce.com. Defender AD FS Adapter supports Windows Server 2012 R2, Windows Server 2016, and Windows Server 2019.
Prerequisites
Before installing Defender AD FS Adapter in the system, verify the following:
- Microsoft .NET Framework 4.5.2 or later is installed
- Defender Client SDK 5.9.3 or later is installed
- AD FS role is installed and the AD FS service is running
- PowerShell 4.0 or later is installed
- The federated logins to the relying parties are configured and working
Connectivity Requirements
After verifying and setting up the prerequisites, connecting to Defender through Defender AD FS Adapter requires the following parameters:
- IP address or DNS name of Defender Security Server (DSS)
- Port number (Default value is 1812)
- Timeout (Default value is 15 seconds)
- Shared Secret (The shared secret must be same as the shared secret configured in Defender Access Node.)
- User ID Attribute (The User ID Attribute must be same as the User ID Attribute configured in Defender Access Node. The default value is the sAM Account Name.)
Deployment Overview
Defender AD FS Adapter adds Multi-Factor Authentication (MFA) that provides a Two-Factor authentication prompt to web-based logins through AD FS server or Web Application Proxy. After completing the primary AD FS server authentication (using standard means such as Windows Integrated or Forms-Based), you must complete Defender authentication challenge before getting redirected to the relying party. If the deployment is in an AD FS farm, install Defender AD FS Adapter on all AD FS servers in the farm.
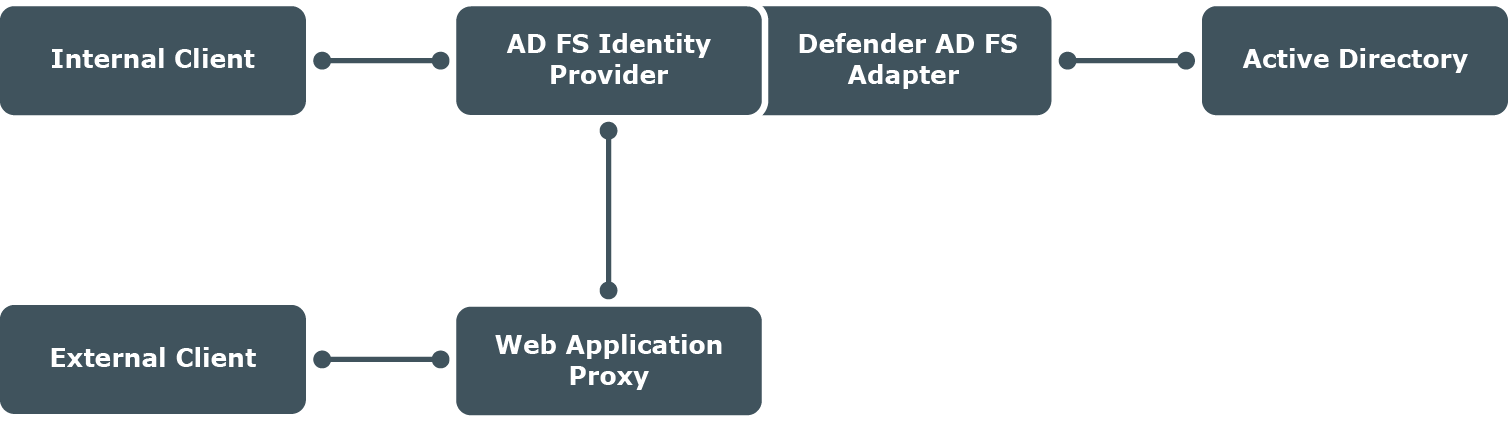
After the installation of Defender AD FS Adapter on the AD FS servers in the farm, while configuring the Multi-Factor Authentication policies, select the MFA location (Internal access or External access or both as per the requirement). If you require Two-Factor authentication for External access locations, a Web Application Proxy is required and you do not have to install Defender AD FS Adapter on the Web Application Proxy server.
- セルフ・サービス・ツール
- ナレッジベース
- 通知および警告
- 製品別サポート
- ソフトウェアのダウンロード
- 技術文書
- ユーザーフォーラム
- ビデオチュートリアル
- RSSフィード
