This section describes how you can modify the network configuration of IPMI from the console of One Identity Safeguard for Privileged Sessions (SPS).
Prerequisites
SPS is accessible using the IPMI only if the IPMI is physically connected to the network. For details on connecting the IPMI, see "Installing the SPS hardware" in the Installation Guide.
|
|
Caution:
IPMI searches for available network interfaces during boot. Make sure that IPMI is connected to the network through the dedicated Ethernet interface before SPS is powered on. |
|
|
Caution: SECURITY HAZARD!
The IPMI, like all out-of-band management interfaces, has known vulnerabilities that One Identity cannot fix or have an effect on. To avoid security hazards, One Identity recommends that you only connect the IPMI to well-protected, separated management networks with restricted accessibility. Failing to do so may result in an unauthorized access to all data stored on the SPS appliance. Data on the appliance can be unencrypted or encrypted, and can include sensitive information, for example, passwords, decryption keys, private keys, and so on. For more information, see Best Practices for managing servers with IPMI features enabled in Datacenters. |
NOTE: The administrator of SPS must be authorized and able to access the IPMI for support and troubleshooting purposes in case vendor support is needed.
The following ports are used by the IPMI:
-
Port 22 (TCP): SSH (configurable)
-
Port 80 (TCP): Web (configurable)
-
Port 161 (UDP, TCP): SNMP (configurable)
-
Port 443 (TCP): Web SSL (configurable)
-
Port 623 (UDP): Virtual Media (configurable)
-
Port 5900 (TCP): IKVM Server (configurable)
-
Port 5985 (TCP): Wsman (configurable)
The SSH encrypted connection (port 22) works with the following properties:
|
Supported: |
Safeguard Sessions Appliance 3000 |
Safeguard Sessions Appliance 3500 |
|---|---|---|
|
Ciphers |
aes128-ctr, aes256-ctr |
3des-cbc, aes128-ctr, aes128-cbc, aes256-ctr, aes256-cbc |
|
KEX algorithm |
curve25519-sha256, ecdh-sha2-nistp256, curve25519-sha256@libssh.org, ecdh-sha2-nistp384, diffie-hellman-group1-sha1, ecdh-sha2-nistp521, diffie-hellman-group14-sha1 |
curve25519-sha256, ecdh-sha2-nistp256, curve25519-sha256@libssh.org, ecdh-sha2-nistp384, diffie-hellman-group1-sha1, ecdh-sha2-nistp521, diffie-hellman-group14-sha1 |
|
MACs |
hmac-sha1, hmac-sha2-256, hmac-sha1-96, hmac-sha2-512 |
hmac-md5, hmac-sha2-256, hmac-sha1, hmac-sha2-512, hmac-sha1-96 |
|
HostKey algorithms |
ssh-rsa, ssh-dss |
ssh-rsa, ssh-dss |
|
Compression |
enabled | enabled |
SSL-encrypted connections work with the following properties:
|
Supported: |
Safeguard Sessions Appliance 3000 |
Safeguard Sessions Appliance 3500 |
|---|---|---|
|
TLSv1.2 |
enabled |
enabled |
|
TLS Fallback SCSV |
supported |
supported |
|
Heartbleed |
not vulnerable |
not vulnerable |
|
Server Ciphers |
Preferred TLSv1.2 256 bits ECDHE-RSA-AES256-GCM-SHA384 Curve P-256 DHE 256 Accepted TLSv1.2 256 bits ECDHE-RSA-AES256-SHA384 Curve P-256 DHE 256 Accepted TLSv1.2 256 bits DHE-RSA-AES256-GCM-SHA384 DHE 2048 bits Accepted TLSv1.2 256 bits DHE-RSA-AES256-SHA256 DHE 2048 bits Accepted TLSv1.2 256 bits AES256-GCM-SHA384 Accepted TLSv1.2 256 bits AES256-SHA256 Accepted TLSv1.2 128 bits ECDHE-RSA-AES128-GCM-SHA256 Curve P-256 DHE 256 Accepted TLSv1.2 128 bits ECDHE-RSA-AES128-SHA256 Curve P-256 DHE 256 Accepted TLSv1.2 128 bits DHE-RSA-AES128-GCM-SHA256 DHE 2048 bits Accepted TLSv1.2 128 bits DHE-RSA-AES128-SHA256 DHE 2048 bits Accepted TLSv1.2 128 bits AES128-GCM-SHA256 Accepted TLSv1.2 128 bits AES128-SHA256 |
Preferred TLSv1.2 256 bits ECDHE-RSA-AES256-GCM-SHA384 Curve P-256 DHE 256 Accepted TLSv1.2 256 bits ECDHE-RSA-AES256-SHA384 Curve P-256 DHE 256 Accepted TLSv1.2 256 bits DHE-RSA-AES256-GCM-SHA384 DHE 2048 bits Accepted TLSv1.2 256 bits DHE-RSA-AES256-SHA256 DHE 2048 bits Accepted TLSv1.2 256 bits AES256-GCM-SHA384 Accepted TLSv1.2 256 bits AES256-SHA256 Accepted TLSv1.2 128 bits ECDHE-RSA-AES128-GCM-SHA256 Curve P-256 DHE 256 Accepted TLSv1.2 128 bits ECDHE-RSA-AES128-SHA256 Curve P-256 DHE 256 Accepted TLSv1.2 128 bits DHE-RSA-AES128-GCM-SHA256 DHE 2048 bits Accepted TLSv1.2 128 bits DHE-RSA-AES128-SHA256 DHE 2048 bits Accepted TLSv1.2 128 bits AES128-GCM-SHA256 Accepted TLSv1.2 128 bits AES128-SHA256 |
|
Server Key Exchange Groups |
TLSv1.2 128 bits secp256r1 (NIST P-256) |
TLSv1.2 128 bits secp256r1 (NIST P-256) |
|
Server Signature Algorithms |
TLSv1.2 Server accepts all signature algorithms. |
TLSv1.2 Server accepts all signature algorithms. |
To modify the network configuration of IPMI from the console of SPS
-
Use the local console (or SSH) to log in to SPS as root.
-
Choose Shells > Boot shell.
-
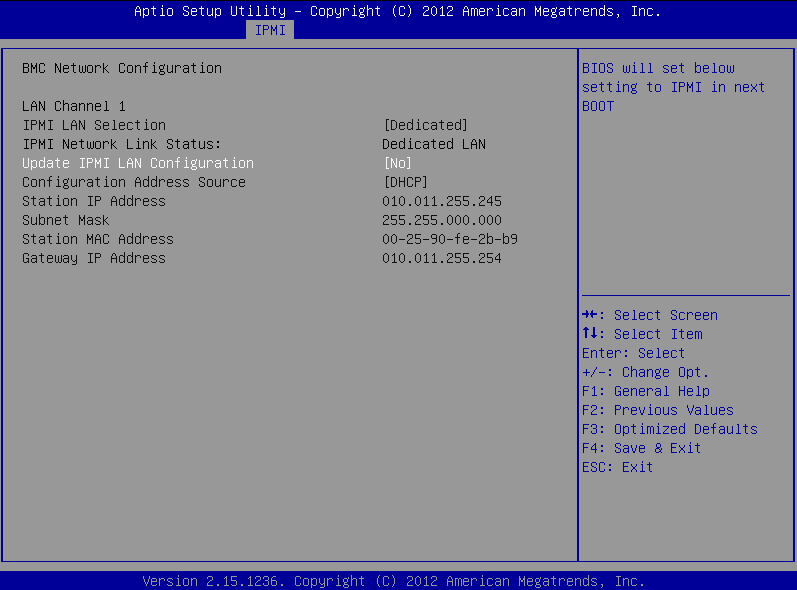
Check the network configuration of the interface:
# ipmitool lan print
This guide assumes that channel 1 is used for LAN. If your setup differs, adjust the following commands accordingly.
-
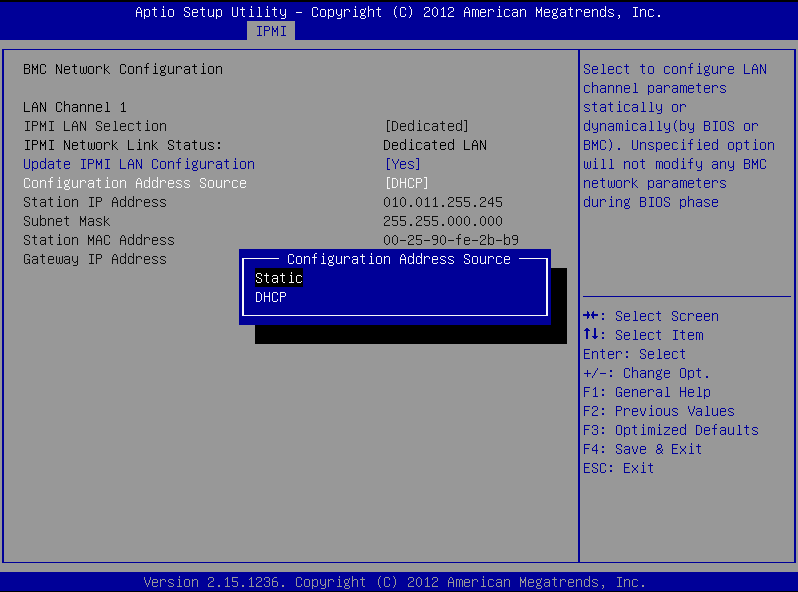
Configure the interface. You can use DHCP or configure a static IP address manually.
Use an IPv4 address.
-
To use DHCP, enter the following command:
# ipmitool lan set 1 ipsrc dhcp
-
To use static IP, enter the following command:
# ipmitool lan set 1 ipsrc static
Set the IP address:
# ipmitool lan set 1 ipaddr <IPMI-IP>
Set the netmask:
# ipmitool lan set 1 netmask <IPMI-netmask>
Set the IP address of the default gateway:
# ipmitool lan set 1 defgw ipaddr <gateway-IP>
-
-
Verify the network configuration of IPMI:
# ipmitool lan print 1
Use a browser to connect to the reported network address.
-
Change the default password:
-
Log in to the IPMI web interface using the default login credentials (username: ADMIN, password: ADMIN or changeme, depending on your hardware).
NOTE: The login credentials are case sensitive.
-
Navigate to Configure > Users.
-
Select ADMIN, and choose Modify User.
-
Change the password, and save the changes with Modify.
-


 .
.