If you install a realm (several Password Manager instances sharing the same configuration), changes in the configuration of one instance are automatically propagated to other instances. To propagate the data, Password Manager replicates the data from the shared.storage file and the LocalizationStorage folder to Active Directory.
Before being written to Active Directory, the data is split into several segments and archived.
To distribute the configuration data from one instance to another, Password Manager uses a scheduled task and the PMReplication container in a managed domain to which the data is copied. The PMReplication container is a container that is automatically created in the Users container of the managed domain. To this container, containers for each Password Manager realm are added. Names of these containers correspond to the realm affinity ID. Each realm container has the containers for every instance belonging to this realm. Names of instance containers correspond to the instance ID.
In the instance container, several user accounts are created. The number of user accounts is one more than the number of data segments. For example, if there are 20 data segments, then the instance container has 21 user accounts. Note that the created user accounts are disabled.
The same attribute that you specify for storing users’ Q&A profiles is used to store the configuration data segments. The first user account stores the data replica ID, all other accounts store the data segments.
Replication mechanism analyses all data segments from all instances, selects data with the latest changes, and propagates it.
|

|
Caution: It is not recommended to edit Password Manager settings simultaneously on multiple instances belonging to one realm. Simultaneous modification of settings on multiple Password Manager instances may cause data loss. |
Note that the domain management account must have the permission to create user accounts and containers in the Users container for configuration data to be replicated. For more information on configuring the domain management account, see Configuring Permissions for Access Account.
By default, the data to be replicated is divided into segments by segment size (100 KB). Data can also be divided into segments according to a specified segment number.
You can also change the name of the storage container (by default, PMReplication) and the location for storing this container (by default, the Users container of a managed domain), and the names of user accounts used to store data segments.
You can change replication settings by modifying the QPM.Service.Host.exe.config file located in the <Password Manager installation folder>\Service folder.
|

|
Caution: Editing the configuration file may cause serious problems. It is recommended to back up the file before modifying it. Edit the QPM.Service.Host.exe.config file at your own risk. |
Changing replication settings
-
On the computer where Password Manager is installed, open the QPM.Service.Host.exe.config file located in the <Password Manager installation folder>\Service folder with a text editor.
-
In the replication node, specify the following:
-
To divide the configuration data into segments by a segment size, set the packetLimitMode to LimitSize (packetLimitMode="LimitSize").
-
To divide the configuration data into segments by a number of segments, set the packetLimitMode to LimitCount (packetLimitMode="LimitCount").
-
If you set the packetLimitMode to LimitSize, specify the maximum segment size in bytes in the maxPacketSize parameter. For example, maxPacketSize="100000". Set the maxPacketsCount parameter to zero (maxPacketsCount="0").
-
If you set the packetLimitMode to LimitCount, specify the maximum number of segments to be created in the maxPacketsCount parameter. For example, maxPacketCount="10". Note, that this value must be greater than 1. Set the maxPacketsSize parameter to zero (maxPacketsSize="0").
-
In the storageManager node, specify the following:
-
To change the name of the storage container, in the storageContainerReplicationPath element specify the required name. The default value is CN=PMReplication.
-
To change the container for storing replication data, in the storageContainerPath element specify the required container. The default value is CN=Users.
-
To change the names of user accounts used to store data segments, in the storageContainerPartName element specify the required name. The default value is strg.
-
Save the QPM.Service.Host.exe.config file.
-
Restart the Password Manager Service in the Services console. Type services.msc at a command prompt, select Password Manager Service in the console, and click Restart.
-
Repeat steps 1-4 on each instance belonging to a Password Manager realm.
One of the authentication options offered by Password Manager is a phone-based authentication. It enables you to require users to enter a verification code on the Self-Service or Helpdesk site. The verification code can be sent as an SMS (text message) or automated call. The phone-based authentication service is by provided by TeleSign.
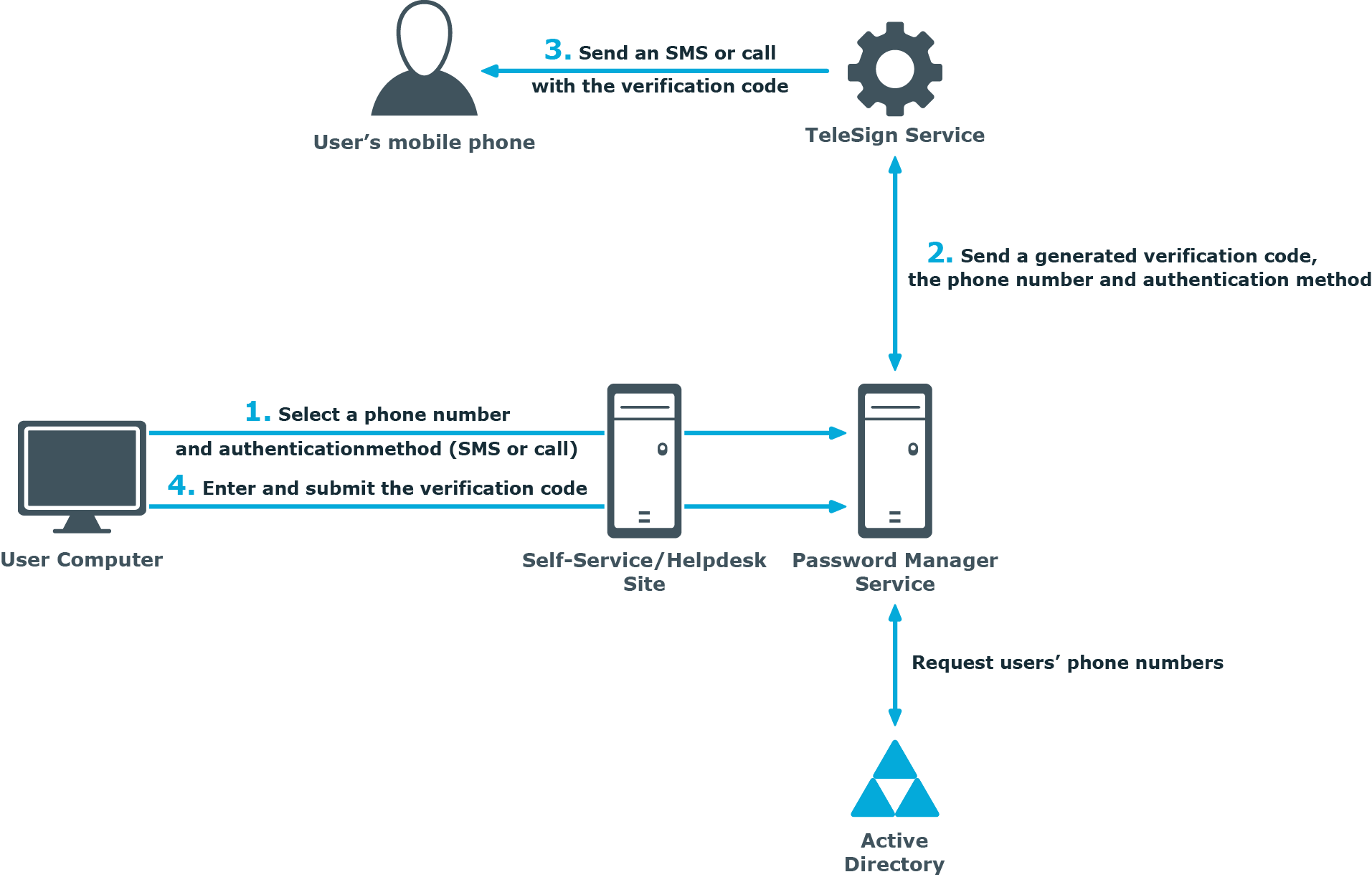
When starting a workflow containing phone-based authentication, Password Manager checks whether the phone-based authentication service is enabled in the provided license. The workflow is executed only if this service is enabled in the license.
-
On the Self-Service or Helpdesk site, a user selects their preferred phone number and verification method (SMS or automated call). This data is sent to Password Manager Service. Password Manager Service gets the phone numbers from the Active Directory attributes specified in the workflow settings.
-
Password Manager Service generates a verification code and transfers the code, selected phone number, and verification method to TeleSign Service. HTTPS is used to send the data. The generated verification code is stored until the workflow is ended. Only one code is stored at a time.
-
TeleSign Service sends an automated call or SMS to the user’s mobile phone with the verification code. The language of the automated call depends on the user interface language of the Self-Service or Helpdesk site.
-
The user enters the verification code on the Self-Service site, then the code is sent to Password Manager Service.
-
Password Manager Service checks the verification code, if it is correct, the user is granted access to further steps on the Self-Service site.


