The Windows Event Collector (WEC) acts as a log collector and forwarder tool for the Microsoft Windows platform. It collects the log messages of Windows-based hosts over HTTP or HTTPS (using TLS encryption and mutual authentication), and forwards them to a syslog-ng Premium Edition (syslog-ng PE) server. In Windows terminology, this tool allows you to define source-initiated push subscriptions, and have them forwarded to a syslog-ng PE server. For details on the limitations of WEC, see Limitations.
Unlike the syslog-ng Agent for Windows, the Windows Event Collector is a standalone tool that does not require installing additional software on the Windows-based host itself. This can be an advantage when your organization's policies restrict or do not allow the installation of third-party tools.
Another difference between the Windows Event Collector tool and syslog-ng Agent for Windows is that WEC forwards only Windows EventLog, while syslog-ng Agent forwards both Windows event logs as well as files from Windows hosts to the syslog-ng PE server.
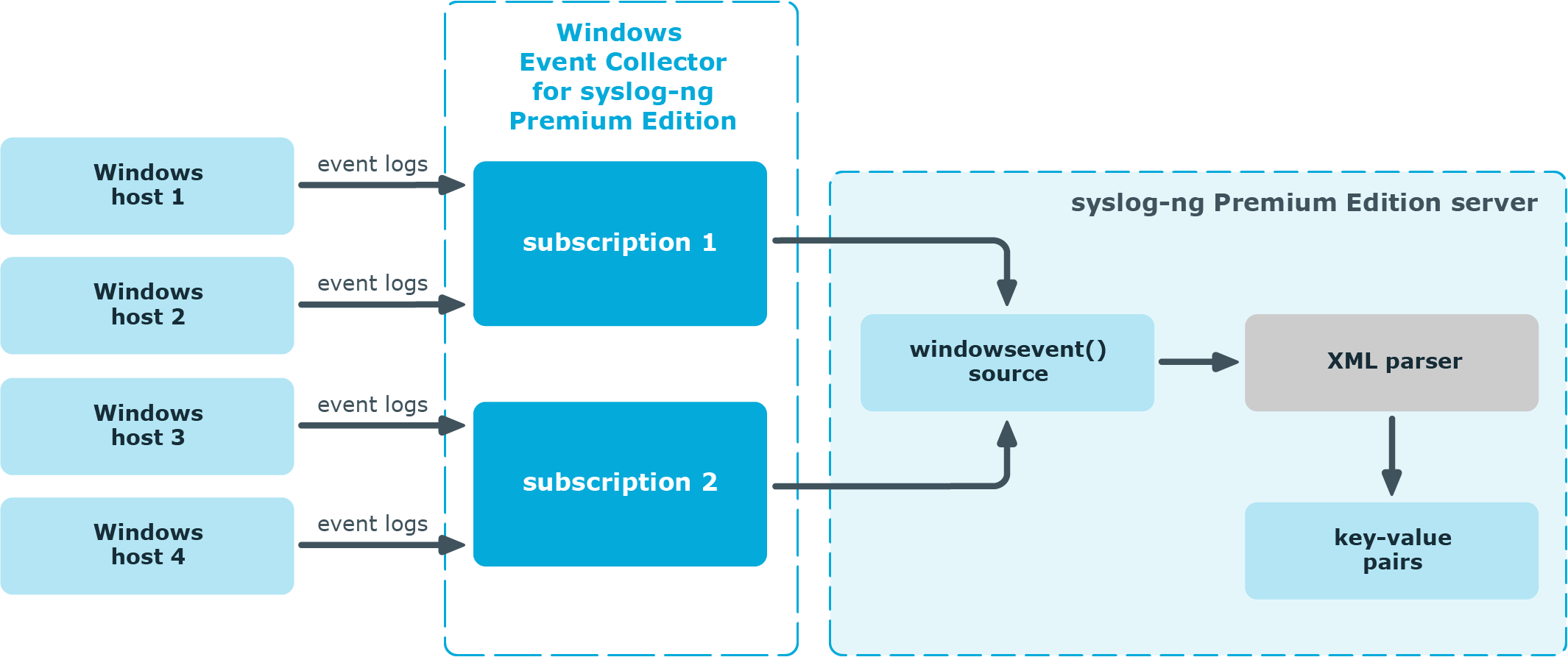
The Windows Event Collector sits between your Windows hosts and your syslog-ng Premium Edition server, accepting log messages from the remote Windows side with WinRM and feeding them to syslog-ng Premium Edition 7.0.
Figure 1: How Windows Event Collector works in syslog-ng PE 7.0
For more information on how you can configure Windows event logs to be forwarded to your syslog-ng Premium Edition server using the WEC tool, see Configuring Windows event logs to be forwarded to the syslog-ng Premium Edition server using WEC.
The Windows Event Collector application officially supports collecting events from the following Windows versions. Note that the following table is for general reference only, and is not always accurate about the supported platforms.
You can select which authentication option you want to use between Windows Event Forwarding (WEF) and Windows Event Collector (WEC) for event forwarding. The supported authentication options are the following:
-
Certificate-based
-
Kerberos
From syslog-ng PE version 7.0.26, for event forwarding between WEF and WEC, Kerberos authentication is also supported as a Preview Feature, besides certificate-based authentication.
|

|
CAUTION: This is a Preview Feature, which provides an insight to planned enhancements to functionality in the product. Consider this Preview Feature a work in progress, as it may not represent the final design and functionality.
This feature has completed QA release testing, but its full impact on production systems has not been determined yet, and potential future changes in functionality and the user interface may result in compatibility issues in your current settings.
One Identity recommends the following:
-
Consider the potential risks when using this functionality in a production environment.
-
Consider the Support Policy on Product Preview Features before using this functionality in a production environment.
-
Closely and regularly keep track of official One Identity announcements about potential changes in functionality and the user interface. If these potential changes affect your configuration, check the changes you have to make in your configuration, otherwise your syslog-ng PE application may not start after upgrade.
-
Always perform tests prior to upgrades in order to avoid the risks mentioned.
However, you are welcome to try this feature and if you have any feedback, contact One Identity.
Support Policy on Product Preview Features
The One Identity Support Team will:
-
Accept and review each service request opened regarding a Preview Feature.
-
Consider all service requests relating to a Preview Features as severity level 3.
-
Provide best effort support to resolve any issues relating to a Preview Feature.
-
Work with customers to log any product defects or enhancements relating to Preview Features.
-
Not accept requests for escalations regarding Preview Features.
-
Not provide after-hours support for Preview Features. |
NOTE: WEC cannot work in different authentication modes at once: you can either configure Kerberos authentication, or certificate-based authentication.
NOTE: Kerberos authentication does not work in a WEC cluster deployment.
Configuring Windows event logs to be forwarded to the syslog-ng Premium Edition server using WEC
This section describes, at a high level, how you can configure Windows event logs to be forwarded to your syslog-ng Premium Edition server using the Windows Event Collector (WEC) tool.
The configuration procedure differs slightly according to which authentication option (certificate-based or Kerberos) you want to use between Windows Event Forwarding (WEF) and WEC.
For more information on the configuration procedure:
NOTE: WEC cannot work in different authentication modes at once: you can either configure Kerberos authentication, or certificate-based authentication.
Configuration procedure if certificate-based authentication is used
-
Set up WEC as the server that collects and forwards event logs.
The following procedure provides details on how to set up and configure the WEC tool:
-
Install WEC.
For more information, see Installing the Windows Event Collector.
-
Generate SSL certificates for WEC.
For more information, see Generating SSL certificates for Windows Event Collector.
-
Configure WEC.
For more information, see Configuring Windows Event Collector.
-
Configure Windows event source computers.
For more information, see Configuring certificate-based authentication on event source computers.
-
WEC accepts incoming event log subscription requests from the Windows hosts.
-
WEC handshakes the event forwarding settings with the Windows hosts, for example, which events to forward.
-
WEC accepts the forwarded event logs, and writes the raw logs to a Unix datagram socket.
-
The syslog-ng PE application reads the Unix datagram socket using a source called windowsevent().
For details on how to configure your syslog-ng PE server, see Configuring syslog-ng PE.
-
The syslog-ng PE application parses the logs into key-value pairs using the XML parser.
For details on the XML parser, see XML parser in the Administration Guide.


