The provisioning sequence
The following visual shows how object changes are provisioned and how the pending changes associated with it are processed. The sequence does not depend on whether the Cloud System Management and the Universal Cloud Interface modules are installed in the same or in separate databases.
Figure 2: Provisioning sequence for pending changes
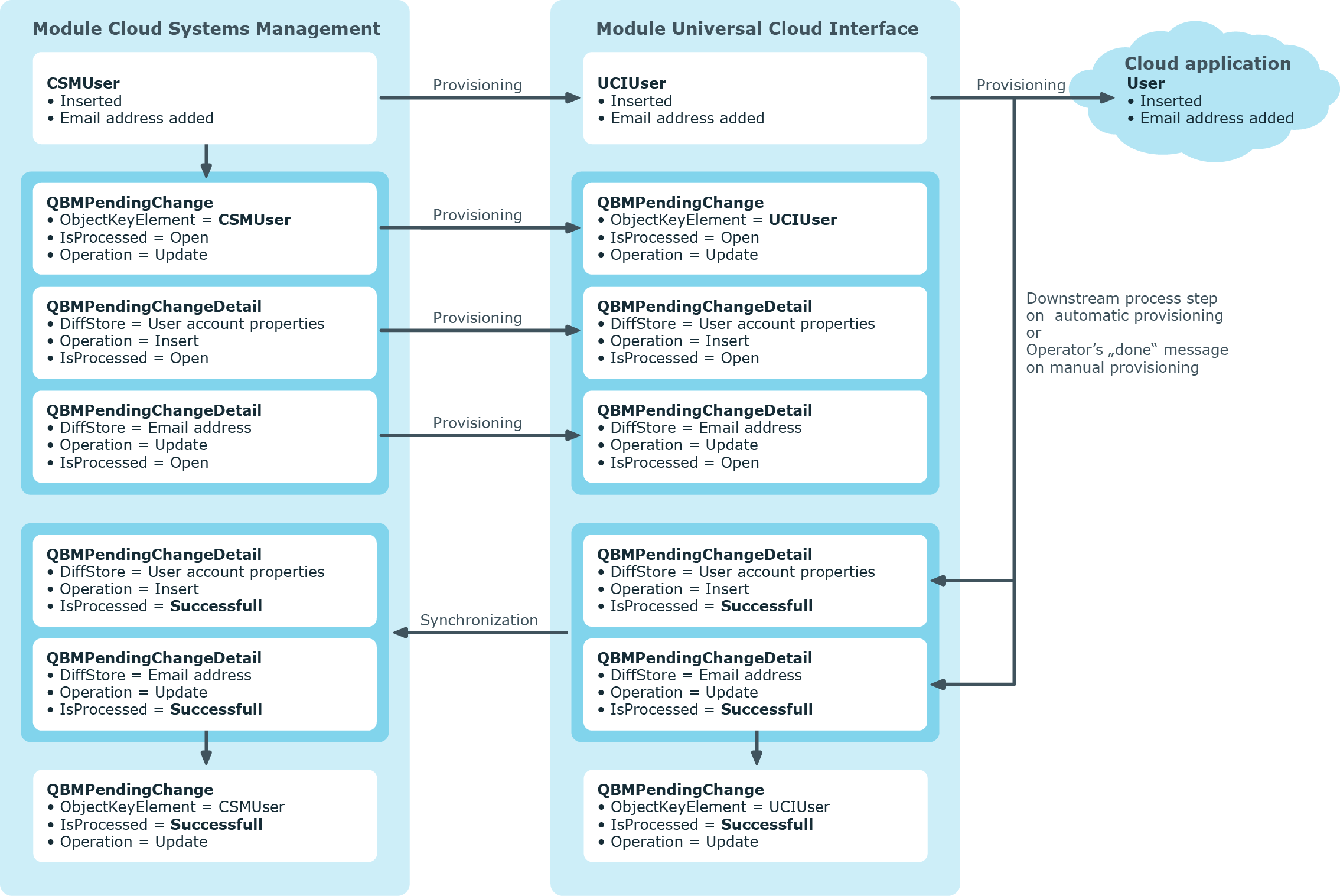
By default, the Cloud Systems Management module is synchronized hourly with the Universal Cloud Interface. This ensures that the processing state for pending changes is declared promptly in the Cloud Systems Management Module.
Related topics
Displaying pending changes
You can view pending changes in the Manager. Here, manual, and automatic provisioning processes are shown.
To display pending changes
Table 10: Meaning of the icons in the toolbar
|

|
Show selected object. |
|

|
Reload the data. |
Related topics
Retention time for pending changes
Pending changes are saved for a fixed period. After this period has expired, the entries are deleted by the DBQueue Processor from the QBMPendingChange and QBMPendingChangeDetail tables. The retention period depends on the status of provisioning processes and can be configured in the configuration parameter.
To configure the retention period for pending changes
-
To change the retention period for successful provisioning processes, in the Designer, edit the value of the QBM | PendingChange | LifeTimeSuccess configuration parameter. Enter a retention period in days. The default is 2 days.
-
To change the retention period for failed provisioning processes, in the Designer, edit the value of the QBM | PendingChange | LifeTimeError configuration parameter and enter the retention period in days. The default is 30 days.
-
To change the retention period for pending provisioning processes, in the Designer, edit the value of the QBM | PendingChange | LifeTimeRunning configuration parameter and enter the retention period in days. The default is 60 days.
Related topics
Managing cloud user accounts and identities
The main feature of One Identity Manager is to map identities together with the main data and permissions available to them in different target systems. To achieve this, information about user accounts and permissions can be read from the target system into the One Identity Manager database and linked to identities. This provides an overview of the permissions for each identity in all of the connected target systems. One Identity Manager offers the option of managing user accounts and their permissions. You can provision modifications in the target systems. Identities are supplied with the necessary permissions in the connected target systems according to their function in the company. Regular synchronization keeps data consistent between target systems and the One Identity Manager database.
Because requirements vary between companies, One Identity Manager offers different methods for supplying user accounts to identities. One Identity Manager supports the following methods for linking identities and their user accounts:
-
Identities can automatically obtain their account definitions using user account resources.
If an identity does not yet have a user account in a target system, a new user account is created. This is done by assigning account definitions to an identity using the integrated inheritance mechanisms and subsequent process handling.
When you manage account definitions through user accounts, you can specify the way user accounts behave when identities are enabled or deleted.
-
When user accounts are inserted, they can be automatically assigned to an existing identity or a new identity can be created if necessary. In the process, the identity main data is created on the basis of existing user account main data. This mechanism can be implemented if a new user account is created manually or by synchronization. However, this is not the One Identity Manager default method. You must define criteria for finding identities for automatic identity assignment.
-
Identities and user accounts can be entered manually and assigned to each other.
For more information about basic handling and administration of identities and user accounts, see the One Identity Manager Target System Base Module Administration Guide.
Related topics



