Unjoining Safeguard Authentication Services from Starling disables Starling Two-Factor Authentication in Safeguard Authentication Services.
To unjoin Safeguard Authentication Services from Starling
- From the Control Center, navigate to Preferences | Starling Two-Factor Authentication.
- In the Join to Starling and enable Two-Factor Authentication pane, click Starling Join Settings.
- On the Starling Two-Factor Authentication dialog, click Unjoin Starling.
A Starling Organization Admin account or Collaborator account can rejoin Safeguard Authentication Services at any time.
To disable Starling 2FA for a specific PAM service, edit the PAM configuration file (/etc/pam.conf or /etc/pam.d/<service>). Modify the auth pam_vas line for the desired service.
To disable Starling 2FA for a specific PAM service
-
As root, add the following line to the PAM configuration file, on the first auth pam_vas line for the service:
disable_starling
Defender provides strong authentication capabilities.
Why is strong authentication an important part of an Active Directory bridge solution?
When Safeguard Authentication Services integrates Unix with Active Directory, it provides centralized access control and password policy enforcement. However, there are situations where security policies dictate a stronger level of authentication. Safeguard Authentication Services addresses this need with optional strong authentication capabilities. Customers now can use the same solution for integrated Active Directory authentication and strong authentication. Organizations that have tight security requirements will no longer be forced to purchase and implement a third-party solution.
How is strong authentication used with an Active Directory bridge solution?
An organization may have many Unix systems deployed in a traditional, highly secure perimeter network environment. As they are integrated with Active Directory, they will require an Active Directory credential to authenticate. Now, an additional layer of authentication can be added for administrators accessing these systems, using either a hardware or software token.
If an organization has integrated hundreds or thousands of Unix systems with Active Directory, a system administrator can now use the same Active Directory credential to access all of them. An additional level of security can be easily added by requiring the system administrator to use one-time password (OTP) in additional to the Active Directory credential.
How do Safeguard Authentication Services’ strong authentication capabilities compare to other Active Directory bridge solutions?
Strong authentication combined with an Active Directory bridge is a unique and critical differentiator for One Identity. No other Active Directory bridge vendor offers strong authentication as an integrated part of its solution, and no strong authentication vendor offers Unix coverage and Active Directory integration.
Is there an additional charge for strong authentication with Safeguard Authentication Services 4.x?
There is no additional cost for strong authentication with Safeguard Authentication Services 4.x; it is a new feature available to new and upgrading customers.
Safeguard Authentication Services provides strong authentication for up to 25 users at no additional cost through included licenses and tokens for Safeguard Authentication Services Defender. These licenses will cover and secure 25 of an organization‘s Unix system administrators. Strong authentication support for additional end-users is available at an additional per-user cost.
How does strong authentication with Safeguard Authentication Services 4.x work?
Safeguard Authentication Services:
- Includes strong authentication modules and native packages for all supported platforms (100+).
- Remotely deploys and installs the strong authentication module.
- Provides hardware and software tokens for one-time passwords.
- Enables policy-based configuration of strong authentication through Active Directory Group Policy.
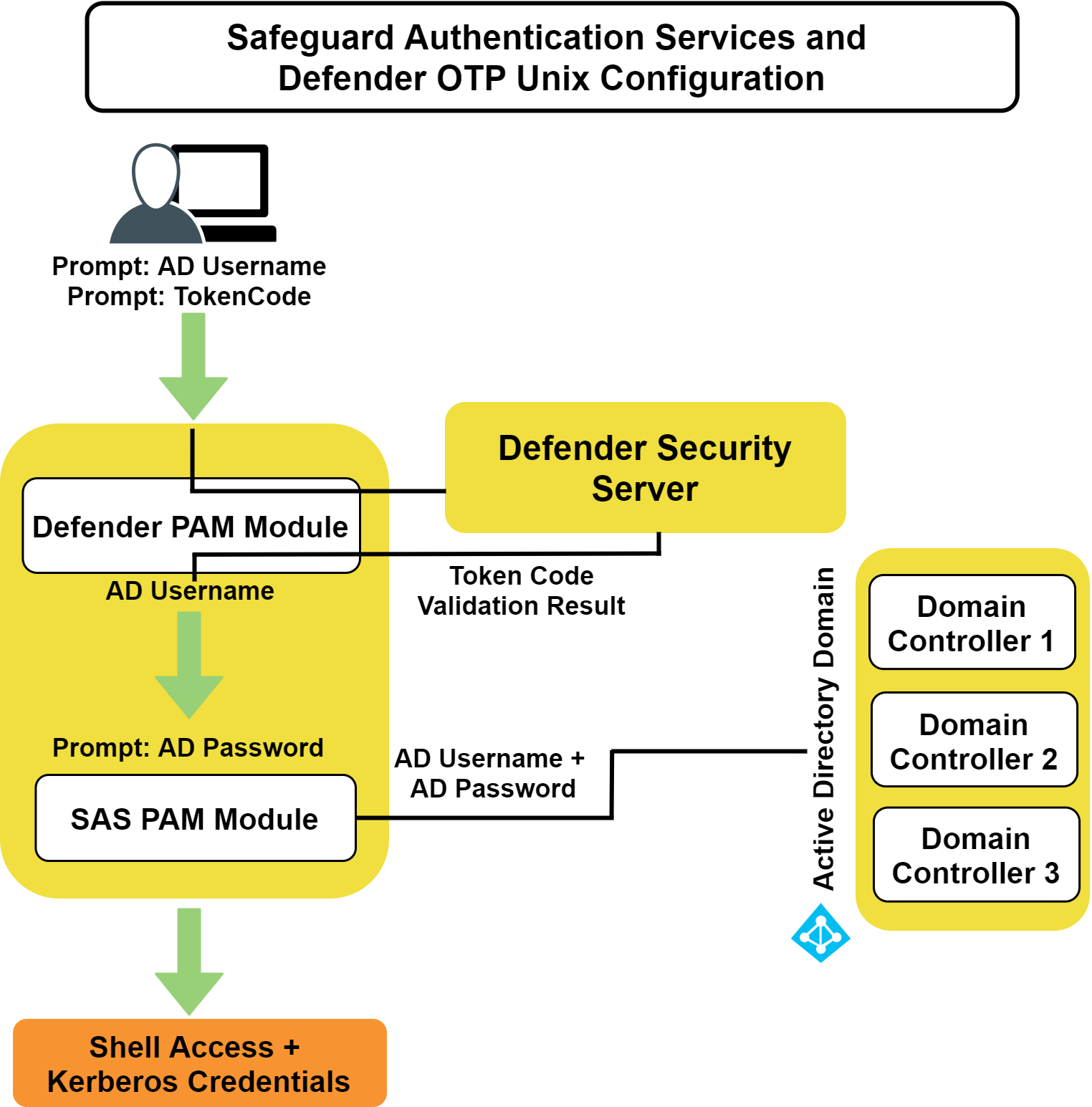
The following figure describes the flow of events that occur during a Unix or Linux login after both Safeguard Authentication Services Defender and Safeguard Authentication Services are configured according to this guide.
Figure 2: Defender Integration
Before you install Safeguard Authentication Services Defender on your host, ensure that you have:
- Installed a Defender security server in your Active Directory domain.
- Installed the Defender Microsoft Management Console (MMC) snap-in.
- Installed Safeguard Authentication Services on your Unix or Linux machine.

