Problem:
A network trace reveals if a Kerberos TGS request for the CIFS service ticket was sent to a domain controller. If a Mac machine never attempts to get a CIFS service ticket for SSO, it is usually a problem where the machine is not able to connect the host name you are contacting with a Kerberos realm. When this happens Finder, or any other mounting application, assumes that the host is not a part of any Kerberos domain for which you have credentials and prompts you for a user name and password.
This can easily happen if your DNS domain name is not the same as your Kerberos realm (often referred to as a disjoint DNS name space). It might also happen if you were trying to connect to the server using a short-name or some other alias.
Workaround:
Add a domain to realm mapping for your DNS domain, short-name, or alias under the [domain_realm] section of the /Library/Preferences/edu.mit.kerberos file.
Safeguard Authentication Services automatically adds a mapping similar to the following at join time:
[domain_realm]
.example.com = EXAMPLE.COM
This maps any DNS names ending in .example.com to the KRB5 realm EXAMPLE.COM. You must always specify the destination domain realm in upper case. When attempting to connect to the share, you must specify the source exactly as the DNS name is specified.
If you are connecting to a share using an alias that does not have a domain suffix, you can explicitly map that name to a KRB5 realm using a domain realm:
[domain_realm]
shortname = EXAMPLE.COM
When you Unix-enable an Active Directory user with Safeguard Authentication Services, the default configuration for that user is that he or she will use a local home directory. The home directory path is populated with a Unix path (/home/<username>).
On macOS systems, /home is replaced with /Users, aligning with the macOS standard location for local home directories. Safeguard Authentication Services supports the automatic mounting of network shares (SMB or AFP) using Active Directory credentials, but you must specify a server path. You can store this server path in the directory on each user as a UNC path, or as a per machine setting.
You can configure your home folder strategy globally for the entire domain using Group Policy extensions for Unix, or you can configure it on a per machine basis at the time you join your macOS machine to the domain.
To configure automatic home folder mounting at join time
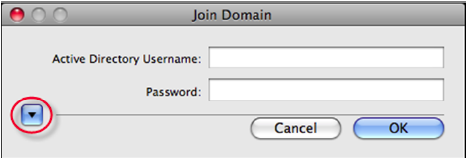
- When you are prompted for your administrative username and password, click the disclosure triangle.

The Join Domain dialog displays.
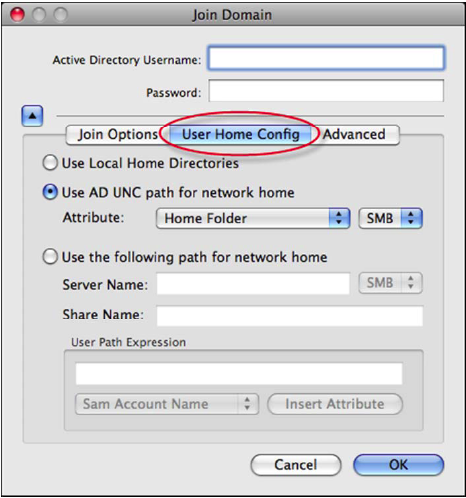
- Select the User Home Config tab to expose all of the home folder mounting options.
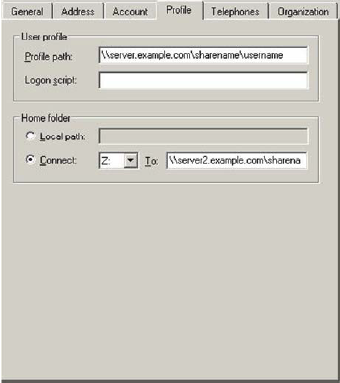
You can configure Safeguard Authentication Services to mount a share that is specified as a UNC format path and stored on a user. The two most commonly used paths are found on the users Profile tab in ADUC.
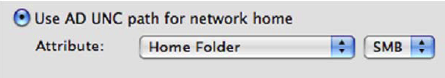
Use Safeguard Authentication Services to mount either the Home Folder or Profile Path on a macOS agent at log in by selecting Use AD UNC path for network home from the User Home Config properties.
To mount the Windows Home Folder or Profile Path
- From the Join Domain dialog, click the disclosure triangle to expand the dialog.
- Select the User Home Config tab to display the home folder mounting options.
- Select the Use AD UNC path for network home option.
-
Select the appropriate UNC format path from the Attribute drop-downs.