Security Analytics Engine Overview
Plugins
Conditions
Introduction
Conditions page
Condition types
Applications
Abnormal Browser
Abnormal Location
Abnormal Time
Associated w/ Malware
Dynamic Blacklist
Restricted Country
Approved Country
Whitelist
Adding and managing conditions
Introduction
Applications page
Adding and managing applications
Adding and managing risk policies
Application wizard
Auditing
Introduction
Auditing page
Filtering the audit events
Configuring the retention settings
Displaying details for an individual audit event
Adding and managing overrides on the Auditing page
Policy Overrides
Fallback Password
Security Settings
Glossary
About Dell
Security Settings
Introduction
From the Home page of the Security Analytics Engine Administration web site, click on the Security Settings link to open the Security wizard where you can configure the Security Analytics Engine Administration web site to accept Active Directory® or LDAP credentials depending upon your organization’s needs. This wizard is also used for enabling and configuring two factor identification using the Dell™ SMS service or a RADIUS server, and managing user and group roles.
Security wizard
The Security wizard is displayed when Security Settings is clicked on the Home page of the Security Analytics Engine Administration web site.
This wizard allows you to manage Active Directory® or LDAP security settings for the Security Analytics Engine Administration web site. The wizard is also used for enabling and configuring two factor identification using the Dell SMS service or a RADIUS server, and managing administrator and help desk roles.
Adding new authentication providers
The following procedures explain how to add an authentication provider using Active Directory® or LDAP as the directory service provider, enable two factor authentication and manage roles.
|
1 |
From the Home page, click on the Security Settings link to open the Security wizard. |
|
3 |
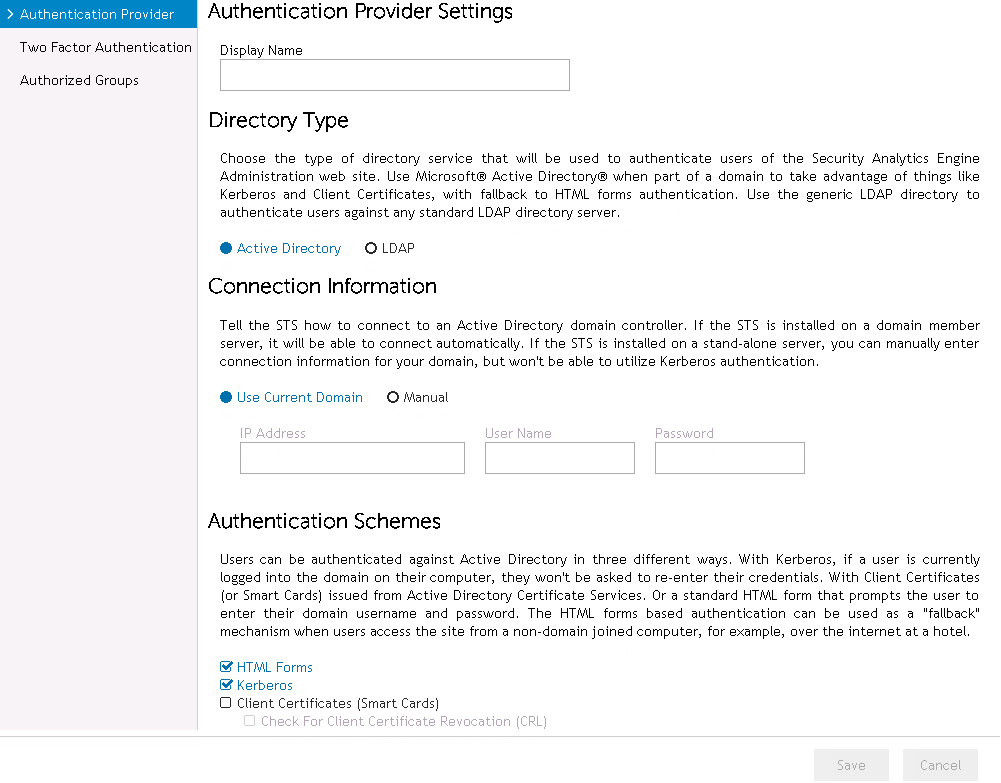
Active Directory is selected by default as the directory service provider type. The page’s remaining sections and fields are determined by this selection. |
If you select Manual, enter the following information:
|
• |
IP Address - Enter the IP address (or host name) of the server to which the Security Analytics Engine will connect. |
|
• |
User Name - Enter the name of an account from the Active Directory domain with read access. |
|
• |
Password - Enter the password for the account. |
|
• |
HTML Forms - Selected by default, this is the standard login page of the Security Analytics Engine in which a user manually enters their domain username and password to be authenticated. |
|
NOTE: When users are already logged into their Windows® machines this may seem a redundant step which defeats the purpose of single sign-on. However, it is recommended that this option remain selected because the HTML Forms authentication can be used as a fallback mechanism when users access the site from a non-domain joined computer (e.g., over the internet at a hotel). |
|
• |
Kerberos - This scheme is intended to automatically authenticate users via Kerberos when the user is currently logged into and has access to the domain. |
|
NOTE: This option is NOT available when Manual is selected on the Connection Information pane or when the Security Analytics Engine is installed on a non-domain joined server. |
|
• |
Client Certificates (Smart Cards) - Select this scheme to only allow authentication to users that possess an X509 certificate or Smart Card containing a certificate that has been associated to their domain account using Microsoft® Active Directory Certificate Services. When this scheme is enabled the user’s web browser may prompt them to choose a certificate from their local machine or Smart Card. If the certificate is valid, the user is authenticated without having to enter their credentials. |
|
Because this revocation check requires an additional network call for each authentication attempt, an additional option, Check For Client Certificate Revocation (CRL), can be enabled or disabled. |
|
6 |
After selecting the authentication scheme(s), click Two Factor Authentication in the left pane. |
|
• |
|
• |
Dell SMS - Selecting this option enables additional authentication through the Dell SMS Service. You must purchase this service from Dell in order to use it for two factor authentication. |
|
• |
|
8 |
If Dell SMS is selected, enter the following information: |
|
• |
Dell SMS Service Access Key - Enter the access key code provided by Dell. |
|
• |
Mobile Phone Number Attribute - Enter the name of the attribute in the directory service provider containing a user’s mobile phone number. |
|
9 |
If RADIUS is selected, enter the following information: |
|
• |
Server - Enter the RADIUS server’s host name or IP address. |
|
• |
Port - Enter the port number for the RADIUS server. |
|
• |
Shared Secret - Enter the RADIUS server’s shared secret string. |
|
• |
Username Attribute - Enter the attribute name from your primary directory service provider that represents the unique username mapping between the two directory stores. |
|
• |
Pre-authenticate For Challenge/Response - Select this check box if you know your RADIUS server is configured for Challenge/Response authentication. If configured, a user may have to answer several questions correctly before being able to log in. |
|
• |
In the Search for text field associated with the Groups section, enter the name or partial name of a group. Leaving this field blank will return all groups. |
|
• |
Click Search to open the Authorize Administration Groups dialog and display the results of your search. |
|
• |
Once all changes have been made, click Accept to save and return to the Authorized Groups page. |
|
• |
In the Search for text field associated with the Individual Accounts section, enter the name or partial name of an account. Leaving this field blank will return all accounts. |
|
• |
Click Search to open the Authorize Administration Accounts dialog and display the results of your search. |
|
• |
Once all changes have been made, click Accept to save and return to the Authorized Groups page. |
|
• |
In the Search for text field associated with the Groups section, enter the name or partial name of a group. Leaving this field blank will return all groups. |
|
• |
Click Search to open the Authorize Help Desk Groups dialog and display the results of your search. |
|
• |
Once all changes have been made, click Accept to save and return to the Authorized Groups page. |
|
• |
In the Search for text field associated with the Individual Accounts section, enter the name or partial name of an account. Leaving this field blank will return all accounts. |
|
• |
Click Search to open the Authorize Help Desk Accounts dialog and display the results of your search. |
|
• |
Once all changes have been made, click Accept to save and return to the Authorized Groups page. |
|
13 |
Once you have finished adding groups and individual accounts, click Save to save all changes made in the wizard. Once the changes have been saved, a bar appears beneath the breadcrumb trail indicating whether or not the changes were successfully saved. Use the browser buttons or breadcrumb trail to exit the wizard. |
|
1 |
From the Home page, click on the Security Settings link to open the Security wizard. |
|
3 |
Select LDAP as the directory service provider type. The page’s remaining sections and fields are determined by this selection. |
|
4 |
In the Hostname/IP Address field, enter the IP address or host name of the LDAP server(s). The value should be of the form ‘hostname:port’. |
|
5 |
By selecting the Is Secure check box, you have the option of using LDAPS for secure communication to the LDAP server using SSL. To use this feature, the LDAP server must have a properly installed SSL certificate with a host name or DNS name matching the value entered in the Hostname/IP Address field. |
|
6 |
In the DN of User to Bind With and Password fields, enter the full distinguished name (DN) of an account that can be used to bind and perform read-only searches against the LDAP server and the account’s password. |
|
7 |
In the Search Base field, enter the distinguished name of the location (or container) within your directory from which all user and group objects are accessible. |
|
• |
Object Class of Users - Enter the Object Class in your LDAP schema that represents a User object. |
|
• |
Object Class of Groups - Enter the Object Class in your LDAP schema that represents a Group object. |
|
• |
User’s Unique ID Attribute - (Optional) Enter an attribute that can be used to uniquely identify a user account. |
|
• |
Group’s Unique ID Attribute - (Optional) Enter an attribute that can be used to uniquely identify a group. |
|
• |
User’s Login Name Attribute - Enter the attribute that contains the value a user types on the Security Analytics Engine Login page when entering their credentials. |
|
• |
Group’s Name Attribute - Enter the attribute name that corresponds to a group’s display name. |
|
• |
User’s Email Attribute - (Optional) Enter an attribute name from which an authenticated user’s email address can be found. |
|
• |
Group’s Members Attribute - Enter the name of a multi-valued attribute that contains a list of the group’s members. |
|
• |
User’s First Name Attribute - Enter the user’s First Name attribute. |
|
• |
User’s Last Name Attribute - Enter the user’s Last Name attribute. |
|
9 |
After entering the attribute values, click Two Factor Authentication in the left pane. |
|
• |
|
• |
Dell SMS - Selecting this option enables additional authentication through the Dell SMS Service. You must purchase this service from Dell in order to use it for two factor authentication. |
|
• |
|
11 |
If Dell SMS is selected, enter the following information: |
|
• |
Dell SMS Service Access Key - Enter the access key code provided by Dell. |
|
• |
Mobile Phone Number Attribute - Enter the name of the attribute in the directory service provider containing a user’s mobile phone number. |
|
12 |
If RADIUS is selected, enter the following information: |
|
• |
Server - Enter the RADIUS server’s host name or IP address. |
|
• |
Port - Enter the port number for the RADIUS server. |
|
• |
Shared Secret - Enter the RADIUS server’s shared secret string. |
|
• |
Username Attribute - Enter the attribute name from your primary directory service provider that represents the unique username mapping between the two directory stores. |
|
• |
Pre-authenticate For Challenge/Response - Select this check box if you know your RADIUS server is configured for Challenge/Response authentication. If configured, a user may have to answer several questions correctly before being able to log in. |
|
• |
In the Search for text field associated with the Groups section, enter the name or partial name of a group. Leaving this field blank will return all groups. |
|
• |
Click Search to open the Authorize Administration Groups dialog and display the results of your search. |
|
• |
Once all changes have been made, click Accept to save and return to the Authorized Groups page. |
|
• |
In the Search for text field associated with the Individual Accounts section, enter the name or partial name of an account. Leaving this field blank will return all accounts. |
|
• |
Click Search to open the Authorize Administration Accounts dialog and display the results of your search. |
|
• |
Once all changes have been made, click Accept to save and return to the Authorized Groups page. |
|
• |
In the Search for text field associated with the Groups section, enter the name or partial name of a group. Leaving this field blank will return all groups. |
|
• |
Click Search to open the Authorize Help Desk Groups dialog and display the results of your search. |
|
• |
Once all changes have been made, click Accept to save and return to the Authorized Groups page. |
|
• |
In the Search for text field associated with the Individual Accounts section, enter the name or partial name of an account. Leaving this field blank will return all accounts. |
|
• |
Click Search to open the Authorize Help Desk Accounts dialog and display the results of your search. |
|
• |
Once all changes have been made, click Accept to save and return to the Authorized Groups page. |
|
16 |
Once you have finished adding groups and individual accounts, click Save to save all changes made in the wizard. |