Dell™ One Identity Cloud Access Manager as an Identity Provider (IDP)
|
1 |
In NetWeaver administration on the Configuration|Security|Authentication and Single Sign-On|SAML 2.0 page, click the Trusted Providers link. Click Add, and choose by uploading metadata file. |
|
2 |
In the Select Metadata step, choose the CloudAccessManagerMetadata.xml document downloaded in step 11 of Cloud Access Manager configuration (Identity Provider Role) and click Next. |
|
3 |
In the Metadata Verification step, choose the certificate (PEM file) downloaded in step 11 of Cloud Access Manager configuration (Identity Provider Role) and click Next. |
|
4 |
|
5 |
In the Signature and Encryption step, change the Single Sign-On Authorization Request Sign parameter to Never and click Next. |
|
6 |
|
7 |
|
8 |
|
9 |
|
10 |
Click Enable. |
Enabling SSO to SAP NetWeaver® applications
|
1 |
|
2 |
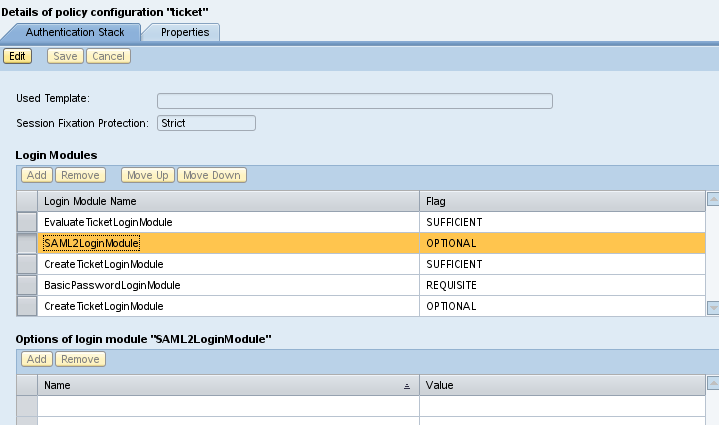
On the Authentication tab, highlight the ticket policy configuration. On the Authentication Stack tab, click Edit. |
|
3 |
Under Login Modules, click Add. Choose SAML2LoginModule from the dropdown list. Click Add again, and choose CreateTicketloginModule from the list. |
|
4 |
Change the order and the flag status of the five login modules to match the following, then click Save. This will use federation, and fall back to forms if federation fails. |
Legal notices
|
CAUTION: A CAUTION icon indicates potential damage to hardware or loss of data if instructions are not followed. | |
|
WARNING: A WARNING icon indicates a potential for property damage, personal injury, or death. | |