Dell™ One Identity Cloud Access Manager 8.1.2 - How to Configure Single Sign-On for Native Android Applications
This guide describes how to deploy Single Sign-On (SSO) for native Android™ applications using the OpenID® Connect http://openid.net/connect/ protocol, and includes the following information:
|
• |
Overview
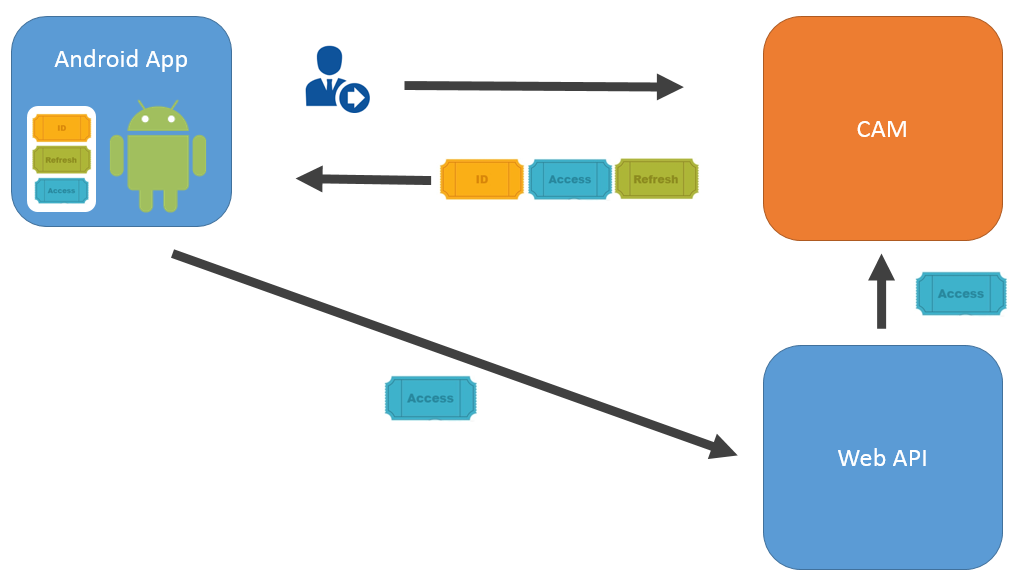
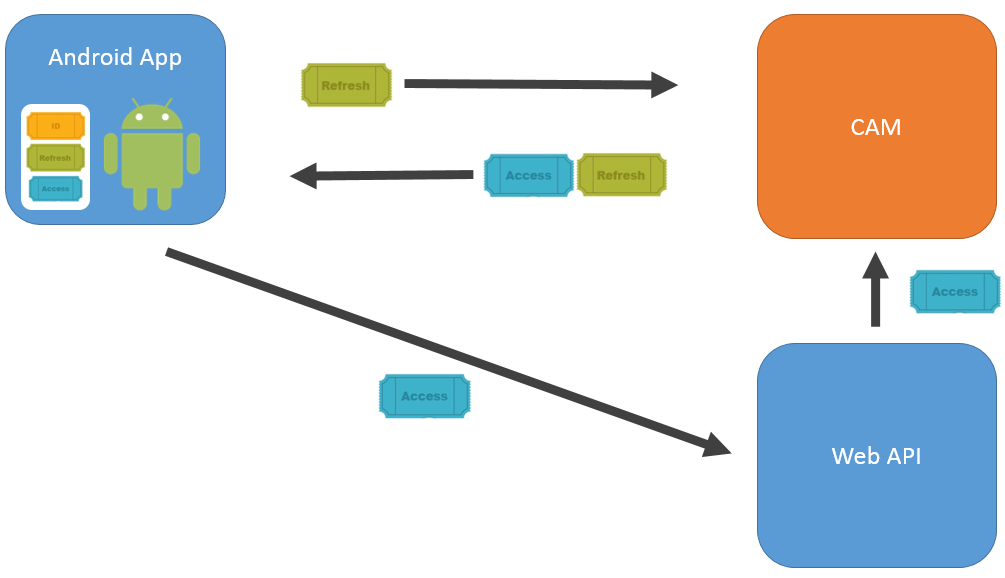
Using the OpenID® Connect protocol, the Android™ application authenticates the user against Dell™ One Identity Cloud Access Manager and retrieves a set of three security tokens, as shown in Figure 1. The security tokens are known as the ID Token, Refresh Token and Access Token.
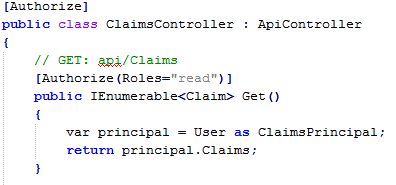
Application walkthrough
This sample application consists of two components:
The sample Android™ application contains a package called openidconnect which can be used in a standard Android™ project to authenticate users, using the OpenID® Connect Code Flow.
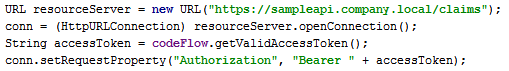
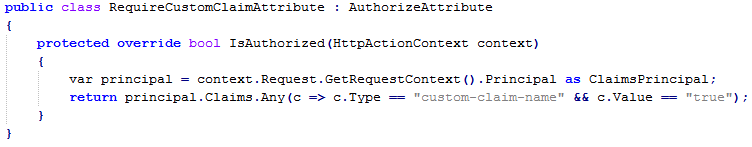
The sample Web API contains a .NET Open Web Interface (OWIN) middleware called CAMBearerTokenAuthentication which can be used in a standard .NET Web API project to authenticate the Android™ application, using the Access Tokens obtained from Dell™ One Identity Cloud Access Manager.
|
1 |
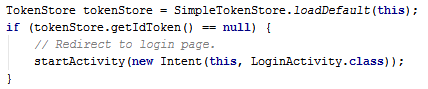
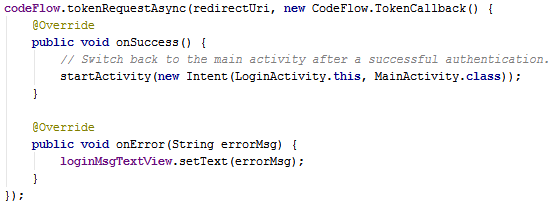
When the application starts it checks for an existing ID Token stored from a previous authentication. If an ID Token does not exist, the application sends an authentication request, using the system browser, to start the OpenID® Connect Authorization Code Flow. If an ID Token exists, the application skips to step 4. |
Cloud Access Manager configuration
|
1 |
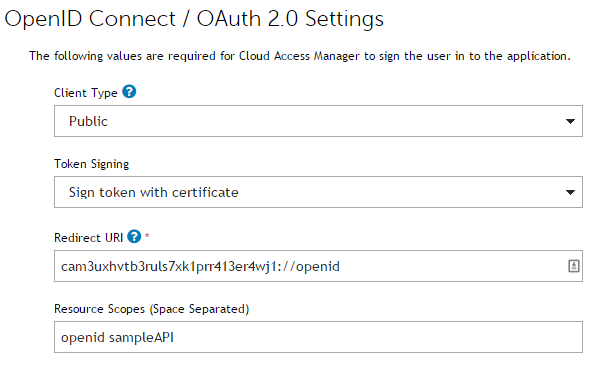
Make sure that the settings on the OpenID Connect / OAuth 2.0 Settings page are as shown below: |
|
2 |
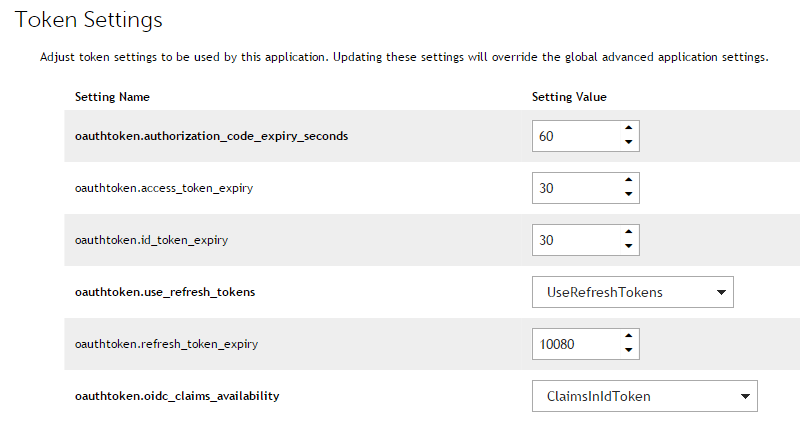
Make sure that the settings on the Token Settings page are as shown below: |
|
3 |
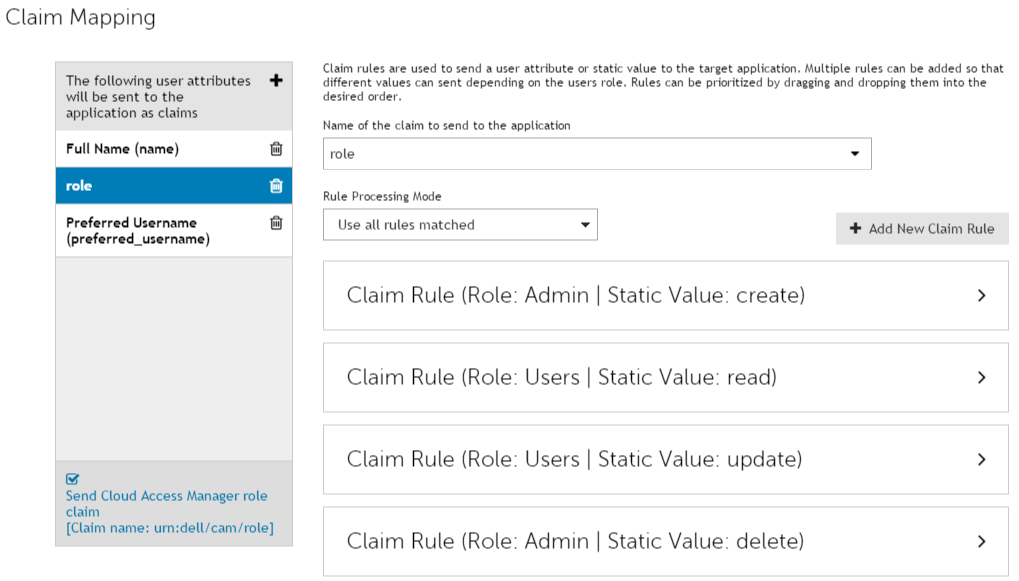
Make sure that the settings on the Claim Mapping page are as shown below: |