HTTP connections
A production environment proxy host should be able to handle up to 12,000 concurrent, persistent HTTP connections.
You may need to configure the host to support this number of connections, by default Microsoft Windows Server 2008 R2 will allow approximately 8,000 connections. To allow a greater number of connections use the netsh command to increase the dynamic ports range, please refer to http://en.wikipedia.org/wiki/Ephemeral_port for further information.
The following example will allow approximately 12,000 persistent HTTP connections. Run this command from a command prompt as an administrator, this setting takes immediate effect and does not require a reboot.
netsh int ipv4 set dynamicport tcp start=40000 num=25000
STS hosts
For a production environment, we recommend that each Security Token Service (STS) host has 8GB of physical memory and 8 processor cores. For example, two quad core processors giving a total of 8 cores spread over two processors.
CPU and memory usage varies between the different authentication methods. Our stress testing has shown a single STS host can support between 12,000 and 18,000 users authenticating over a 30 minute period. Our recommended maximum of 15,000 is an average of the two. No special configuration is required on the STS hosts to support this number of users.
Preventing direct access to applications protected by Cloud Access Manager
When you have added an application to Cloud Access Manager, you can make sure that users only access the application using Cloud Access Manager. This may be required if you are using Cloud Access Manager to enforce strong authentication for the application, or want to use Cloud Access Manager’s auditing features to monitor application usage. The procedure described below is only required for non-federated applications, that is, those not using SAML or WS-Federation.
|
|
NOTE: To prevent direct access to an application, we recommend that you use the firewall on the application’s host. For example, you need to update the HTTP/HTTPS firewall rules to only allow access from the internal IP addresses of the Cloud Access Manager proxy hosts. |
To configure the Windows Firewall to prevent direct access to the application
Perform the following steps on the application’s host.
|
|
NOTE: If the application is installed on multiple hosts, repeat these steps on each host running the application. |
- From the Start menu, open Windows Firewall with Advanced Security.
- Ensure the firewall is turned on.
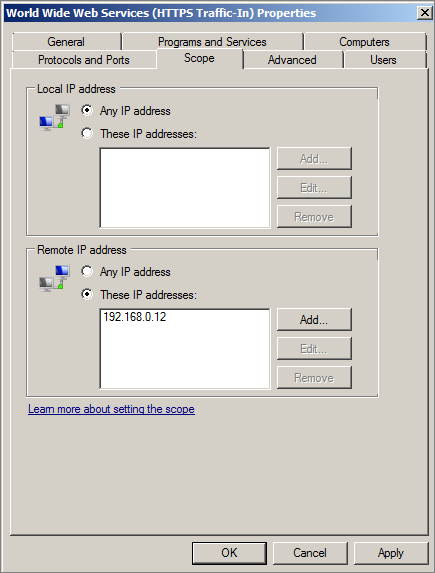
- Locate the Inbound Firewall rule for Secure HTTP (HTTPS) requests. For applications using Internet Information Services (IIS), this is called World Wide Web Services (HTTPS Traffic-In).
- Ensure the rule is enabled.
- Click Properties.
-
Select the Scope tab.
- In the Remote IP address section, select These IP addresses: and add the internal IP address of each proxy host.
- Repeat Step 3 through Step 7 for the HTTP firewall rule.
- Using a browser on another host, verify that you cannot directly access the application running on this host.
When you have updated the firewall configuration on each host running the application, verify that users can still access the application using Cloud Access Manager.
|
|
NOTE: If the host running the application contains multiple applications and you do not wish to prevent direct access to all of them, you can configure the Web Server to restrict access to the proxy hosts on a per application basis. Please refer to http://support.microsoft.com/kb/324066 for instructions on how to configure IIS to use the IP Address and Domain Restrictions feature. |