- The client machine must have the Offline Password Reset utility installed along with the SPE (Secure Password Extension).
- The user must have Internet access from another machine or Internet-capable Smartphone to access the public-facing corporate Password Manager Self Service site
- The Forgot My Password workflow (or similar) must have the Allow Users to reset passwords offline option enabled on the Change Password In Active Directory action.
- Cached logon attempts must be configured
- The Password Manager administrative template must be configured to turn on Offline Reset functionality
Requirements
To enable the offline password reset functionality
- Install the offline password reset component on target users’ computers via group policy. Use the Password Manager files (OfflinePasswordReset_64.msi and OfflinePasswordReset_x86.msi) located in the \Password Manager\Setup folder on the installation CD.
Secure Password Extension (SPE) must be installed on target users’ computers as well.
- Set the required number of cached user logon attempts. This is necessary because the offline password reset functionality will be available only for users who have previously logged in on their computers. You can use Microsoft knowledge base article http://support.microsoft.com/kb/172931 to change the number of cached logon attempts. It is recommended to use the default value (10).
Figure 3: Setting Logon Count via GPO
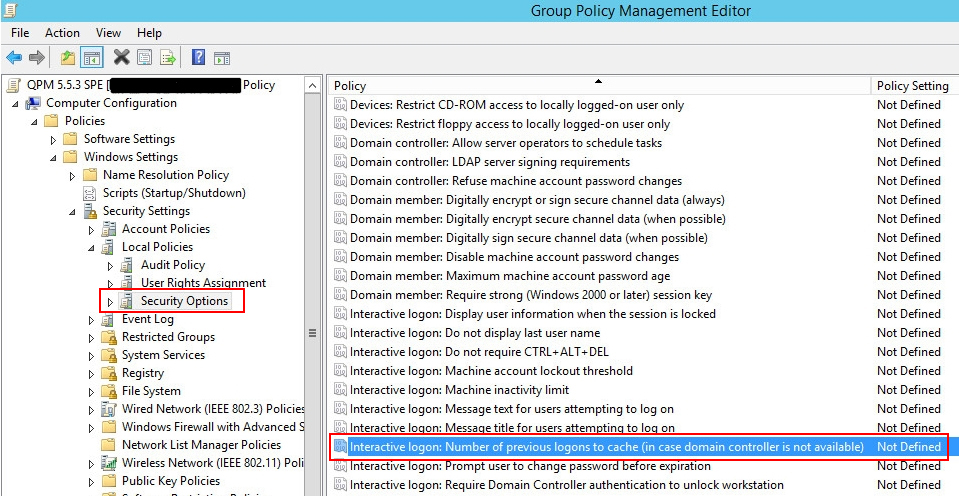
Figure 4:
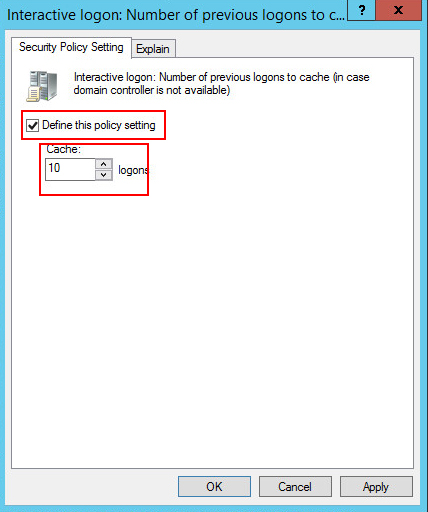
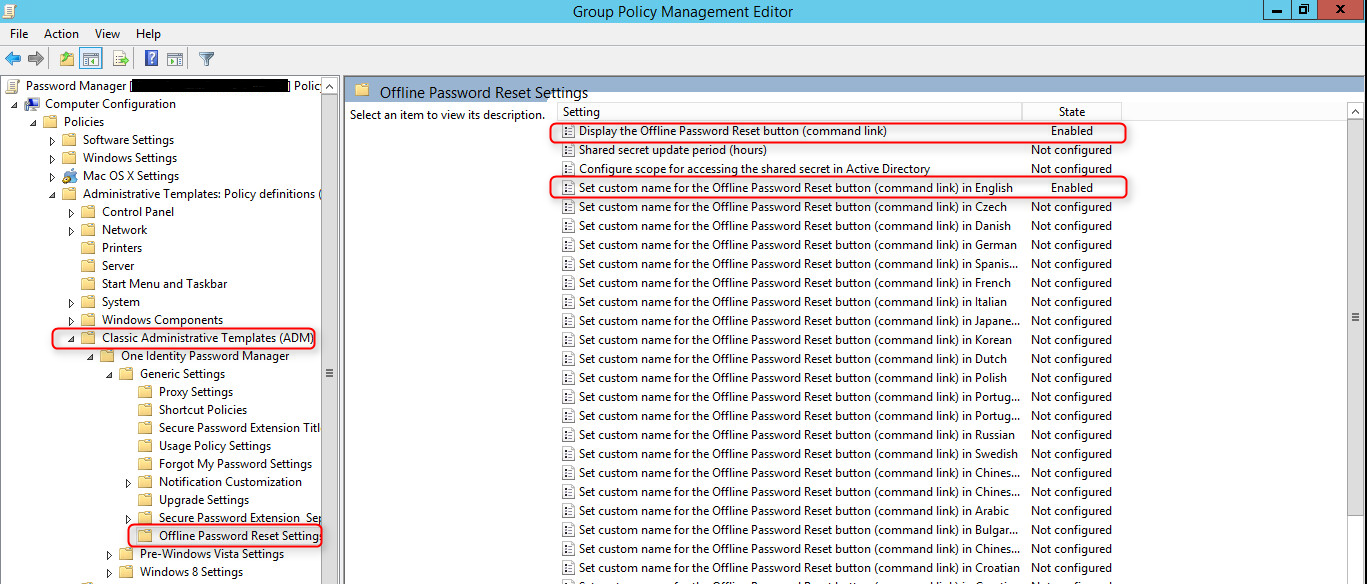
- Use the administrative template prm_gina.admx to turn on the offline password reset functionality. The administrative template file is located in the \Password Manager\Setup\Administrative Template\ folder of the installation CD. In the template, enable the following settings:
Figure 5:
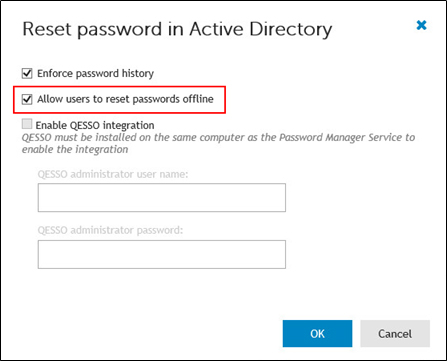
- Use the Reset password in Active Directory activity in a required workflow and select the Allow users to reset passwords offline option.
Figure 6:
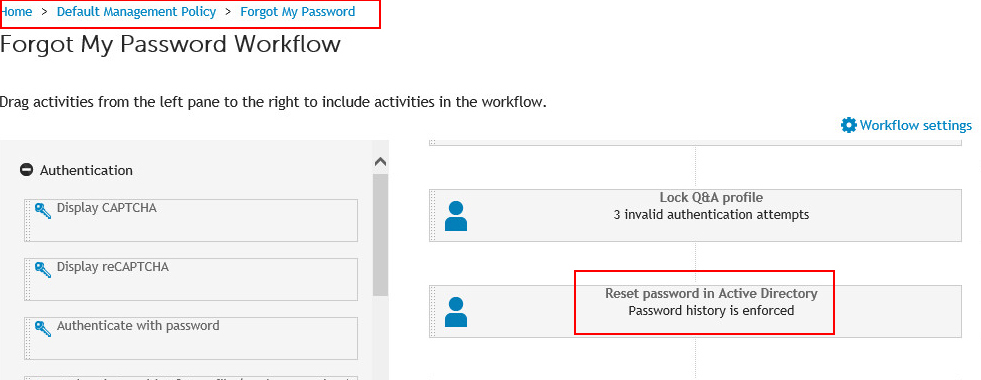
Figure 7:
- Save the workflow.
To provide authentication during the offline password reset procedure, a shared secret is used. The shared secret is stored locally on the user’s computer and its copy is published in Active Directory in the computer’s account during the first logon if the computer is connected to the domain. By default, only domain administrators and the computer account have access to the shared secret. You can specify other users and groups who will have the permission to read the shared secret from the domain. To do this, use the Configure scope for accessing the shared secret in Active Directory setting in the administrative template.
Password Policy Manager
Overview
In addition to providing the ability to manage user passwords, Password Manager also provides the ability to configure Password Policies similar to native Password Policies and Windows Fine-Grained Password Policies found in Active Directory. Password Manager Password policies can provide restrictions such as password length, dictionary lookup and history.
The Password Policies are stored in Group Policy Objects (GPOs) and are applied by linking the GPO to a target container defined in Active Directory, such as an Organizational Unit or group.
Password Policy Manager (PPM) is an optional and independently deployed component of Password Manager. The Password Policy Manager component is necessary to enforce password policies configured in Password Manager in instances when users change their passwords using tools other than Password Manager. To enforce password policies which you define with Password Manager, you must deploy Password Policy Manager on all Domain Controllers (DCs) in a managed domain.
How it Works
When a user changes a password in Password Manager, the new password is checked right away, and if it complies with password policies configured in Password Manager, the new password is accepted.
When a user changes a password outside of Password Manager, such as pressing CTRL+ALT+DELETE, the new password will not be checked immediately by Password Manager. The password's compliance with password policy rules will be checked on a Domain Controller. This is why Password Policy Manager must be installed on all Domain Controllers in a managed domain. If Password Policy Manager is not installed, in this case when the user changes password not in Password Manager, password policies configured in Password Manager will be ignored.
Password Policy Manager extends the default password policy settings and allows configuring policy scopes for each policy, so that only specified Organizational Units and groups are affected by the policy.
Password policy settings are stored as Group Policy Objects. Password Policy Manager creates new GPOs, and it does not change any existing GPOs.
Depending on whether a Domain Controller is running an x86 or x64 version of Microsoft Windows Server operating system, the appropriate version of Password Policy Manager must be installed.

