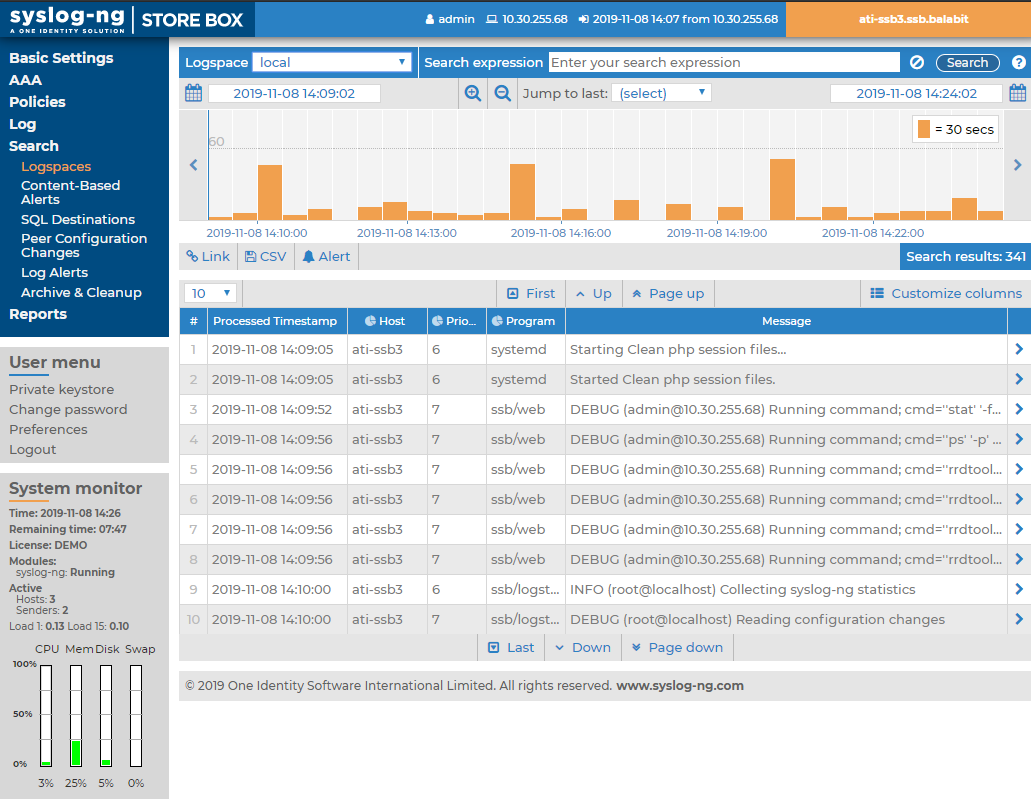
The structure of the web interface
The web interface consists of the following main sections:
Main menu: Each menu item displays its options in the main workspace on one or more tabs. Click a menu item to display the list of available tabs.
Figure 33: Structure of the web interface
User menu: Provides possibilities to change your syslog-ng Store Box (SSB) password, to log out, and disable confirmation dialogs and tooltips using the Preferences option.
Figure 34: User menu

User info: Provides information about the user currently logged in:
Figure 35: User info
System monitor: Displays accessibility and system health information about SSB, including the following:
Figure 36: System monitor
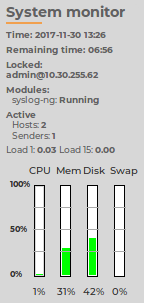
-
Time: System date and time.
-
Remaining time: The time remaining before the session to the web interface times out.
NOTE: To change timeout settings, navigate to Basic Settings > Management > Web interface and RPC API settings > Session timeout and enter the timeout value in minutes.
-
Locked: Indicates that the interface is locked by another administrator (for details, see Multiple web users and locking).
-
Modules: The status of syslog-ng running on SSB (ideally it is RUNNING).
-
License: License information if the license is not valid, or an evaluation version license has expired.
-
Raid status: The status of the RAID devices, if synchronization between the disks is in progress.
-
Active:
-
Hosts: the number of clients (log source hosts) where the log messages originate from (for example computers)
-
Senders: the number of senders where the log messages directly come from (for example, relays)
Example: Number of hosts and senders
For example: if 300 clients all send log messages directly to SSB the Hosts and Senders are both 300.
If the 300 clients send the messages to 3 relays (assuming that the relays do not send messages themselves) and only the relays communicate directly with SSB then Hosts is 300, while Senders is 3 (the 3 relays).
If the relays also send messages, then Hosts is 303, while Senders is 3 (the 3 relays).
-
HA: The HA status and the ID of the active node if two SSB units are running in a High Availability cluster. If there are redundant Heartbeat interfaces configured, their status is displayed as well. If the nodes of the cluster are synchronizing data between each other, the progress and the time remaining from the synchronization process is also displayed.
-
Average system load during the
-
CPU, memory, hard disk, and swap use. Hover the mouse above the graphical bars to receive a more details in a tooltip, or navigate to Basic Settings > Dashboard for detailed reports.
NOTE: If you have installed SSB from Azure, the swap column is not available, because in this case, swap memory is not used.
The System monitor displays current information about the state of SSB. To display a history of these parameters, go to Basic Settings > Dashboard. For details, see Status history and statistics.
Elements of the main workspace
The main workspace displays the configuration settings related to the selected main menu item.
Figure 37: Main workspace
-
 Each page includes one or more blue action buttons. The most common action button is the
Each page includes one or more blue action buttons. The most common action button is the  , which saves and activates the changes of the page.
, which saves and activates the changes of the page.
-
 /
/ Show/Hide Details: Displays or hides additional configuration settings and options.
Show/Hide Details: Displays or hides additional configuration settings and options.
-
 Create entry: Create a new row or entry (for example, an IP address or a policy).
Create entry: Create a new row or entry (for example, an IP address or a policy).
-
 Delete entry: Delete a row or an entry (for example, an IP address or a policy).
Delete entry: Delete a row or an entry (for example, an IP address or a policy).
-
 ,
,  Open/collapse lists: Open or close a list of options (for example, the list of available reports).
Open/collapse lists: Open or close a list of options (for example, the list of available reports).
-
 Modify entries or upload files: Edit an entry (for example, a host key, a list, and so on), or upload a file (for example a private key). These actions open a popup window where the actual modification can be performed.
Modify entries or upload files: Edit an entry (for example, a host key, a list, and so on), or upload a file (for example a private key). These actions open a popup window where the actual modification can be performed.
-
 (Move up),
(Move up),  (Move down): Positions an item in a list, modifying the order of items. The order of items in a list (for example, the order of log paths) is important. For example, when syslog-ng Store Box (SSB) evaluates log paths, it looks at the log paths in descending order.
(Move down): Positions an item in a list, modifying the order of items. The order of items in a list (for example, the order of log paths) is important. For example, when syslog-ng Store Box (SSB) evaluates log paths, it looks at the log paths in descending order.
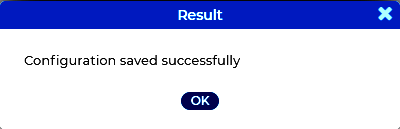
Message window: Displays the error messages and responses of SSB to the user's actions in a popup window, for example Configuration saved successfully. All messages are included in the system log. For detailed system logs (including message history), see the Troubleshooting tab of the Basic menu. To make the window appear only for failed actions, navigate to User menu > Preferences and enable the Autoclose successful commit messages option.
Figure 38: Message window
Multiple web users and locking
Multiple administrators can access the syslog-ng Store Box (SSB) web interface simultaneously, but only one of them can modify the configuration. This means that the configuration of SSB is automatically locked when the first administrator who can modify the configuration accesses a configuration page (for example, the Basic Settings, AAA, or Logs menu). The username and IP address of the administrator locking the configuration is displayed in the System Monitor field. Other administrators must wait until the locking administrator logs out, navigates to a page that is not concerned with modifying the configuration (for example, the Search page), or the session of the administrator times out. However, it is possible to access the Search and Reporting menus, or browse the configuration with only View rights (for details, see Managing user rights and usergroups).
NOTE: If an administrator logs in to SSB using the local console or a remote SSH connection, access via the web interface is completely blocked. Inactive local and SSH connections time out just like web connections. For details, see Accessing the SSB console.
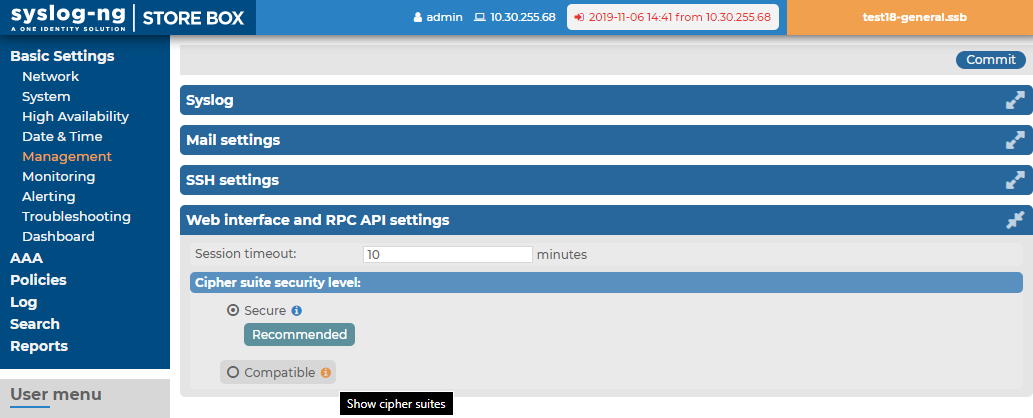
Web interface and RPC API settings
syslog-ng Store Box (SSB) prevents brute force attacks when logging in. If you repeatedly try logging in to SSB using incorrect login details within a short period of time (10 times within 60 seconds), the source IP gets blocked on UI destination port 443 for 5 minutes. Your browser displays an Unable to connect page.
By default, SSB terminates the web session of a user after ten minutes of inactivity. To change this timeout value, adjust the Basic Settings > Management > Web interface and RPC API settings > Session timeout option.
In addition to controlling the web session timeout value, you can also specify the cipher suites to be permitted in the HTTPS connection.
The Basic Settings > Management > Web interface and RPC API settings > Cipher suite option allows you to choose the strength of the allowed cipher suites using one of the following options:
-
Compatible: It is a large set of cipher suites determined by the following cipher string:
ALL:!aNULL:!eNULL
The Compatible setting may allow permitting (and hence not safe) cipher suites for the Transport Layer Security (TLS) negotiations.
-
Secure: A smaller and more strict set of cipher suites where vulnerable cryptographic algorithms are eliminated. This cipher suite set is determined by the following cipher string:
HIGH:!COMPLEMENTOFDEFAULT:!aNULL:!eNULL:!DHE-RSA-AES128-SHA:!DHE-RSA-AES256-SHA:!ECDHE-RSA-AES128-SHA:!ECDHE-RSA-AES256-SHA:!AES128-SHA:!AES256-SHA
Figure 39: Basic Settings > Management > Web interface and RPC API settings — Set session timeout and Cipher suite


username
IP address of the user's computer
date and IP address of the user's last login




 Each page includes one or more blue action buttons. The most common action button is the
Each page includes one or more blue action buttons. The most common action button is the  /
/ Show/Hide Details: Displays or hides additional configuration settings and options.
Show/Hide Details: Displays or hides additional configuration settings and options. Create entry: Create a new row or entry (for example, an IP address or a policy).
Create entry: Create a new row or entry (for example, an IP address or a policy). Delete entry: Delete a row or an entry (for example, an IP address or a policy).
Delete entry: Delete a row or an entry (for example, an IP address or a policy). ,
,  Open/collapse lists: Open or close a list of options (for example, the list of available reports).
Open/collapse lists: Open or close a list of options (for example, the list of available reports). Modify entries or upload files: Edit an entry (for example, a host key, a list, and so on), or upload a file (for example a private key). These actions open a popup window where the actual modification can be performed.
Modify entries or upload files: Edit an entry (for example, a host key, a list, and so on), or upload a file (for example a private key). These actions open a popup window where the actual modification can be performed. (Move up),
(Move up),  (Move down): Positions an item in a list, modifying the order of items. The order of items in a list (for example, the order of log paths) is important. For example, when syslog-ng Store Box (SSB) evaluates log paths, it looks at the log paths in descending order.
(Move down): Positions an item in a list, modifying the order of items. The order of items in a list (for example, the order of log paths) is important. For example, when syslog-ng Store Box (SSB) evaluates log paths, it looks at the log paths in descending order.
