When configuring your own, customized message sources, you can configure two source types: Syslog, or SQL.
For more information about configuring an SQL source type in your own, customized message source, see Configuring your own, customized SQL type message source.
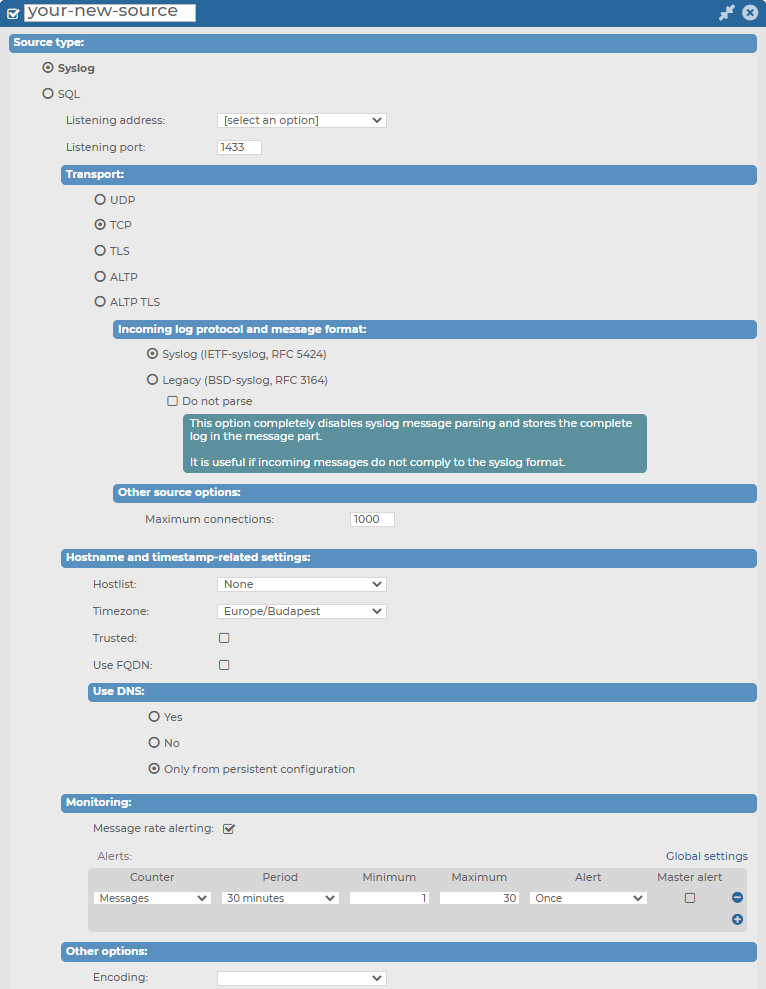
Figure 129: Log > Sources > <your-new-source > — Syslog source type in your own, customized message source
Prerequisites for configuring your own, customized Syslog type message source
Limitations to configuring your own, customized Syslog type message source
Configuration options for your own, customized Syslog type message source
While configuring your own, customized Syslog type message source, you can customize the following:
-
The Listening address and Listening port of your Syslog source type.
-
Transport protocol options, including Incoming log protocol and message format options, and the number of maximum connections under Other source options.
-
Hostname and timestamp-related settings.
-
Monitoring options.
-
Setting the Syslog source type's Encoding under Other options.
For further details on the configuration options, see the following subsections:
Topics:
Under Log > Sources > <your-new-source> > Syslog, you can first customize the Listening address and Listening port for your Syslog type message source.
To configure the Listening address and Listening port of your Syslog type message source
-
Navigate to Log > Sources > <your-new-source> > Source type and select Syslog.
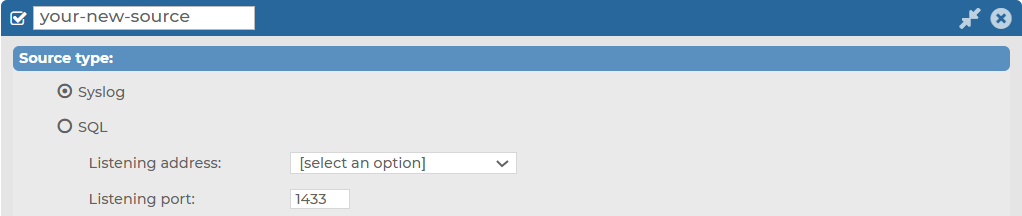
Figure 130: Log > Sources > <your-new-source> > Syslog — Customizing the Listening address and the Listening port for your Syslog type message source
-
Select the Listening address of your choice.
NOTE: Although from version 6.4, syslog-ng Store Box (SSB) supports IPv6 addresses on the external interface and the management interface, you can only select IPv4 addresses for your Syslog sources in the Listening address field.
-
Enter the Listening port on which you want your log source to listen.
Under Log > Sources > your-new-source > Syslog > Transport, you can customize your Transport settings for your syslog-type message source.
To customize your Transport settings for your syslog-type message source
-
Navigate to Log > Sources > your-new-source > Syslog > Transport.
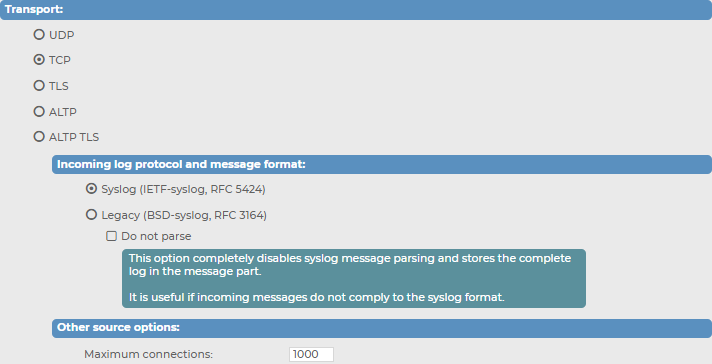
Figure 131: Log > Sources > your-new-source > Syslog > Transport — Configuring transport options for your syslog-type message source
-
In the Transport field, select the networking protocol (UDP, TCP, TLS, ALTP or ALTP TLS) that your clients use to transfer the messages to syslog-ng Store Box (SSB).
-
In case of UDP, TCP or TLS: select the syslog protocol used by the clients from the Incoming log protocol and message format section. The ALTP and ALTP TLS sources only work with the IETF-syslog protocol.
-
If the clients use the legacy BSD-syslog protocol (RFC3164), select Legacy (BSD-syslog, RFC3164). This protocol is supported by most devices and applications capable to send syslog messages.
-
If the clients use the new IETF-syslog protocol (for example the clients are syslog-ng 3.0 applications that use the syslog driver, or other drivers with the flags(syslog-protocol) option), select Syslog (IETF-syslog, RFC 5452).
To disable syslog message parsing and store the complete log in the message part, select Do not parse. It is useful if incoming messages do not comply with the syslog format.
-
When using TLS, SSB displays a certificate to the client. This certificate can be set at Log > Options > TLS settings (for details, see Setting the certificates used in TLS-encrypted log transport). Optionally, SSB can perform mutual authentication and request and verify the certificate of the remote host (peer). Select the verification method to use from the Peer verification field.
-
None: Do not request a certificate from the remote host, and accept any certificate if the host sends one.
-
Optional trusted: If the remote host sends a certificate, SSB checks if it is valid (not expired) and that the Common Name of the certificate contains the domain name or the IP address of the host. If these checks fail, SSB rejects the connection. However, SSB accepts the connection if the host does not send a certificate.
-
Optional untrusted: Accept any certificate shown by the remote host. Note that the host must show a certificate.
-
Required trusted (default setting): Verify the certificate of the remote host. Only valid certificates signed by a trusted certificate authority are accepted. See Uploading external certificates to SSB for details on importing CA certificates. Note that the Common Name of the certificate must contain the domain name or the IP address of the host.
-
Required untrusted: SSB requests a certificate from the remote host, and rejects the connection if no certificate is received. However, SSB accepts the connection if:
-
the certificate is not valid (expired), or
-
the Common Name of the certificate does not contain the domain name or the IP address of the host.
When using ALTP TLS, SSB only accepts Required-trusted peer verification.
|

|
Caution:
UDP is a highly unreliable protocol. When using UDP, a large number of messages may be lost without any warning. Use TCP, TLS or ALTP whenever possible. |
-
Configure other, source-related options in the Other source options section, depending on what transport you have selected.
-
When using TCP or TLS, you can set the maximum number of parallel connections in the Maximum connections field. This option corresponds to the max_connections() syslog-ng parameter.
In case of ALTP or ALTP TLS: enter the number of maximum connections. The default value is 1000 connections. Select Allow compression to allow compression on level 6. Compression level cannot be changed.
-
When using TLS or ALTP TLS, configure the strength of the allowed cipher suites using one of the following options:
-
Compatible: It is a large set of cipher suites determined by the following cipher string:
ALL:!aNULL:!eNULL
The Compatible setting may allow permitting (and hence not safe) cipher suites for the Transport Layer Security (TLS) negotiations.
-
Secure: A smaller and more strict set of cipher suites where vulnerable cryptographic algorithms are eliminated. This cipher suite set is determined by the following cipher string:
HIGH:!COMPLEMENTOFDEFAULT:!aNULL:!eNULL:!DHE-RSA-AES128-SHA:!DHE-RSA-AES256-SHA:!ECDHE-RSA-AES128-SHA:!ECDHE-RSA-AES256-SHA:!AES128-SHA:!AES256-SHA
-
(Optional) Customize the number of your Maximum connections.
Under Log > Sources > <your-new-source> > Syslog > Hostname and timestamp-related settings, you can first customize your settings related to hostnames and timestamps for your Syslog type message source.
To customize your settings related to hostnames and timestamps for your syslog-type message source
-
Navigate to Log > Sources > <your-new-source> > Syslog > Hostname and timestamp-related settings.
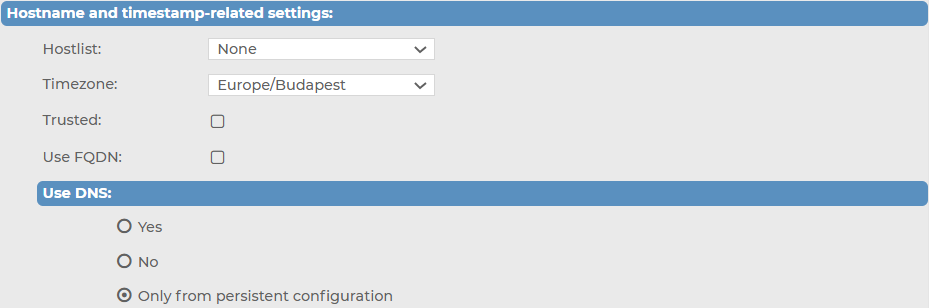
Figure 132: Log > Sources > <your-new-source> > Syslog > Hostname and timestamp-related settings — Customizing your settings related to hostnames and timestamps for your syslog-type message source
-
In the Hostname and time stamp related settings section, configure the following, based on your preferences:
-
To accept messages only from selected hosts, create a hostlist and select it in the Hostlist field. For details on creating hostlists, see Creating hostlist policies.
-
Set the Timezone option of the incoming messages if needed.
-
If the information sent by the hosts to this source can be trusted, enable the Trusted option. The syslog-ng Store Box (SSB) appliance keeps the time stamps and the hostname of the messages sent by trusted clients. This corresponds to enabling the keep_timestamp() and keep_hostname() syslog-ng Premium Edition (syslog-ng PE) options for the source.
-
Select the Use FQDN option if you wish to store the full domain name of the sender host.
-
Select the name resolving method to use from the Use DNS field.
-
To allow using DNS, select Yes.
-
To disable using DNS, select No.
-
To only allow using DNS when using a persistent configuration, select Only from persistent configuration.





