Step 2: Configure Synchronization Service
Step 2: Configure
To configure you installed in Step 1: Install Synchronization Service, you can use one of the following methods:
- Specify new SQL Server or Azure SQL Server databases for storing the data.
With this method, you can select to store the configuration settings and synchronization data either in a single new SQL Server database or in two separate databases.
- Share existing configuration settings between two or more instances of .
Prerequisite:
-
If you are using an Azure SQL Server, set the db_owner database role to the user of the Azure SQL Server.
-
If you are using an SQL Server, set the dbcreator server role to the user of the SQL Server.
dbcreator is the minimum role that the user of the SQL Server or Azure SQL Server requires for the initial configuration of .
After creating the new database, you can revoke the dbcreator role because the db_owner role automatically assigned to the same user of the SQL Server is sufficient for Synchronization Service database connection.
To configure using a new database
- Start the Administration Console.
- Follow the steps in the wizard that starts automatically to configure .
- On the Service Account and Mode page, specify the following and click Next:
- The account under which you want Synchronization Service to run.
- The mode (local or remote) in which you want to use Synchronization Service. Use the remote mode to work with connectors installed remotely. For more information, see Using connectors installed remotely. If you select the remote mode, click Finish to close the wizard.
- Select Create a new configuration and click Next.
-
On the Database Connection page, specify an SQL Server database.
-
(Optional)Select the Store sync data in a separate database check box.
-
If you want to store the configuration settings and synchronization data in a single SQL Server database, clear the checkbox.
-
If you want to store the configuration settings and synchronization data in two separate databases, select the check box, and then specify the database in which you want to store the synchronization data.
-
On the Database Connection page, select an SQL Server authentication method, and click Next.
NOTE: For all Azure SQL Server variants, select Use SQL Server authentication because Windows authentication is not supported.
-
Use Windows authentication: Allows you to access the SQL Server in the security context of the account under which the Synchronization Service is running.
-
Use SQL Server authentication: Allows you to access the SQL Server in the security context of the SQL Server user account whose user name and password you specify.
- On the Configuration File page, select the file for storing the created configuration profile, protect the file with a password, and click Finish.
To configure using an existing database
- Start the Administration Console.
- Follow the steps in the wizard that starts automatically to configure .
- On the Service Account and Mode page, specify the following and click Next:
- The account under which you want Synchronization Service to run.
- The mode (local or remote) in which you want to use Synchronization Service. Use the remote mode to work with connectors installed remotely. For more information, see Using connectors installed remotely. If you select the remote mode, click Finish to close the wizard.
- Select Use an existing configuration and click Next.
- On the Configuration File page, select the I have the configuration file check box to provide the configuration file you exported from an existing Synchronization Service instance, enter the password if necessary, and click Next. If you do not have the configuration file, after clicking Next you will need to enter the required settings.
- If you provided the configuration file, specify the authentication method for accessing the database. Otherwise, enter the required database name and select the authentication method. Click Finish.
After you configure Synchronization Service, you can change its settings at any time using this Configuration wizard. To start the wizard, start the Administration console and click the gear icon in the upper right corner of the console.
Step 3: Configure Azure Backsync
In hybrid environments, on-premises Active Directory objects are synchronized to Azure AD, for example via Azure AD Connect. When you deploy Active Roles in such a hybrid environment, this synchronization works only if existing user and group information (such as the Azure objectID) are also synchronized back from Azure AD to the on-premises AD. Active Roles uses Azure back-synchronization (also known as Azure BackSync) for this purpose.
Prerequisites
The hybrid environment must meet the following requirements to configure Azure BackSync:
-
Azure AD Connect must be installed and configured.
-
Azure Active Directory (Azure AD) module version 2.0.0.131 or later must be installed and configured.
-
The Directory Writers role must be enabled in Azure Active Directory. To enable the role, use the following script:
$psCred=Get-Credential
Connect-AzureAD -Credential $psCred
$roleTemplate = Get-AzureADDirectoryRoleTemplate | ? { $_.DisplayName -eq "Directory Writers" }
# Enable an instance of the DirectoryRole template
Enable-AzureADDirectoryRole -RoleTemplateId $roleTemplate.ObjectId
In addition, the user account you use to configure Azure BackSync must have the following roles:
Automatic and Manual Azure BackSync
You can perform Azure back-synchronization via the Active Roles Console, either automatically or manually:
- You can configure automatic Azure back-synchronization via the
 (Settings) > Configure Azure BackSync option of the Active Roles Console. For more information, see Configuring automatic Azure BackSync.
(Settings) > Configure Azure BackSync option of the Active Roles Console. For more information, see Configuring automatic Azure BackSync.
- You can also configure manual Azure back synchronization, using existing Active Roles feature components. For more information, see Configuring manual Azure BackSync.
Configuring automatic Azure BackSync
You can configure automatic Azure back-synchronization (Azure BackSync) via the  (Settings) > Configure Azure BackSync option of the Active Roles Console. After you finish configuration, the Azure BackSync registration, its required connections, mappings and workflows will be created automatically by the Active Roles .
(Settings) > Configure Azure BackSync option of the Active Roles Console. After you finish configuration, the Azure BackSync registration, its required connections, mappings and workflows will be created automatically by the Active Roles .
For more information on setting up manual Azure back-synchronization, see Configuring automatic Azure BackSync.
To configure an automatic Azure BackSync workflow in Active Roles Synchronization Service
-
Open the Configure BackSync operation in Azure with on-prem Active Directory objects window of the Active Roles Console. To do so, click  (Settings) > Configure Azure BackSync.
(Settings) > Configure Azure BackSync.
-
Select the number of Azure AD services in your Azure tenant:
-
If you have a single Azure AD in your Azure tenant, select I have one Azure AD in my Azure tenant.
-
If you have multiple Azure AD services in your Azure tenant, select I have more than one Azure AD in my Azure tenant.
-
Authenticate your access to Azure AD:
-
If you have selected I have one Azure AD in my Azure tenant, authenticate your access to Azure AD by clicking Log in to Azure.
-
If you have selected I have more than one Azure AD in my Azure tenant, then in the Tenant ID text box, specify the GUID of the Azure AD for which you want to set up synchronization.
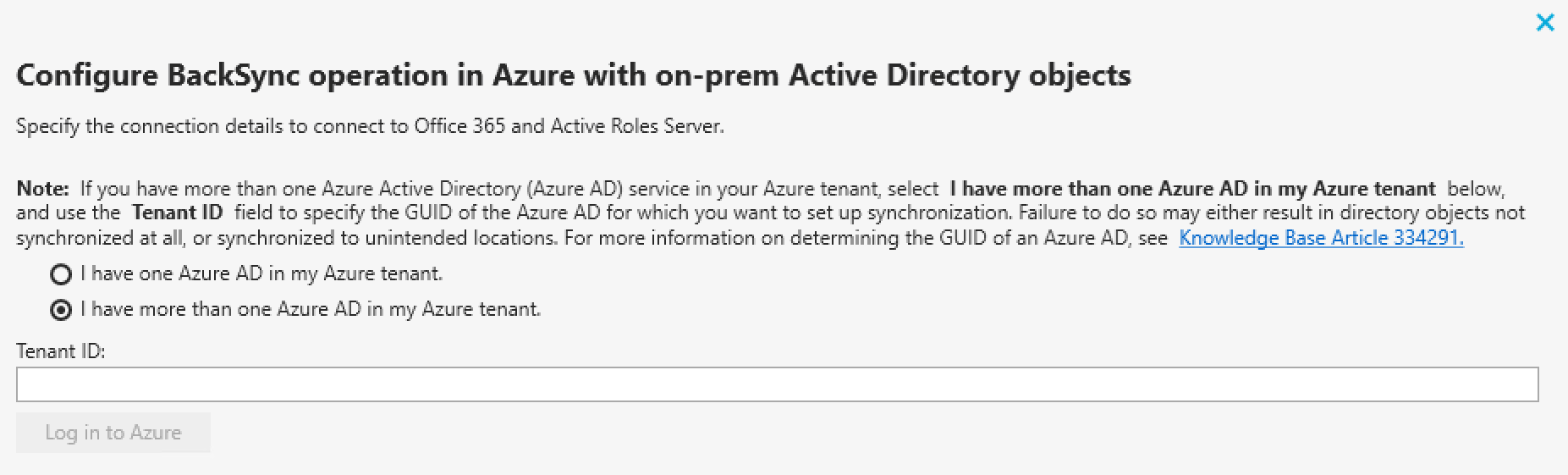
After specifying the tenant ID, click Log in to Azure to authenticate your access to Azure AD.
NOTE: If I have more than one Azure AD in my Azure tenant is selected, the Log in to Azure button will be enabled only if you specify a well-formed Azure AD GUID in the Tenant ID text box.
- Specify whether you want to use a proxy server for the connection:
-
Use WinHTTP settings: Configures the connector to use the proxy server settings configured for Windows HTTP Services (WinHTTP).
-
Automatically detect: Automatically detects and uses proxy server settings.
-
Do not use proxy settings: Specifies to not use proxy server for the connection.
-
Under Connect to, specify the domain name of the computer where the Active Roles Console is running.
-
Select the validation method used to access the Active Roles Administration Service. Depending on how Active Roles has been deployed in your organization, you can either use Synchronization Service account or Windows account-based validation. If you have selected Windows account authentication, enter your Windows user name and password.
-
To test the configured Active Roles connection, click Test Active Roles Connection. Successful validation will be indicated by a success message.
-
To apply your changes, click Configure BackSync.
NOTE: If the Azure BackSync settings have already been configured previously, Active Roles will display a warning message to confirm if you want to override the existing Azure BackSync settings with the new settings.
-
To override the existing settings, click Override BackSync Settings.
-
To keep the existing settings, click Cancel.
-
An Application Consent dialog will appear, prompting you for authentication. To consent Active Roles, click OK.
Active Roles will then automatically perform Azure application registration, and will create the required connections, mappings, and workflow steps for back-synchronization. For more information on the automatically created Azure BackSync settings, see Settings updated after Azure backsync configuration operation.
-
To make the new Azure BackSync workflow appear under Sync Workflows, close and reopen the Active Roles Console. The new Azure BackSync workflow will appear with the following default name: AutoCreated_AzureADBackSyncWorkFlow_<tenant-name>.
Configuring manual Azure BackSync
You can configure manual Azure back-synchronization (Azure BackSync) by using the existing features of Active Roles components. When setting up manual Azure BackSync, you must configure synchronization workflows to identify Azure AD-specific users or groups, and to map them to the corresponding on-premises AD users or groups. After a manual Azure BackSync operation is completed, Active Roles will display the configured Azure attributes for the synchronized objects.
For more information on setting up automatic Azure back-synchronization, see Configuring automatic Azure BackSync.
Prerequisites
The hybrid environment must meet the following requirements to configure Azure BackSync manually:
-
Azure AD Connect must be installed and configured.
-
Azure Active Directory (Azure AD) module version 2.0.0.131 or later must be installed and configured.
-
You must authenticate the Azure tenant of the Azure AD for which you configure back-synchronization. Also, you must consent Active Roles as an Azure application.
For more information, see Configuring Active Roles to manage Azure AD using the GUI in the Active Roles Administration Guide.
-
For the container where Active Roles performs back-synchronization, you must enforce the built-in Azure AD policy that automatically sets the attribute edsvaazureOffice365enabled to true.
- Your Active Roles user must have write permissions for the following attributes:
-
Your Active Roles user must also have local administrator privileges on the machine where Active Roles is running.
To configure a manual Azure BackSync workflow
-
Create a connection to Azure AD using the Azure AD Connector. The configuration requires the following data:
-
Create an Azure Web Application (or use any relevant existing Azure Web Application) under the Azure tenant of your Azure AD. The application must have Application Permissions to read and write directory data in Azure AD.
- Open the application properties and copy the following:
-
Use the Client ID and Client Key when creating a new Azure AD connection or modifying an existing one. For more information, see Configuring a Microsoft Azure AD connection
NOTE: Two applications are required for Azure BackSync operations:
-
The Web Application that you created in this step, or is already available for the Azure AD Connector.
-
An Azure application that you created while configuring Azure AD in the Active Roles Administration Service.
For details, see Configuring Active Roles to manage Azure AD using the GUI in the Active Roles Administration Guide).
Both applications are required for Azure BackSync operations.
-
Create a connection to Active Roles using the Active Roles Connector. The configuration requires the local domain details and the version of Active Roles you use. Define the scope to select the container from which Active Roles will select the objects for synchronization.
-
In the Active Roles Console, create a new sync workflow with Sync Workflows > Add sync workflow. Use the Azure AD and Active Roles connections configured previously, and add a synchronization step to synchronize the Azure AD users or groups with the on-premises users or groups in Active Roles.
-
In the on-premises Active Roles users or groups, set the edsvaAzureAssociatedTenantIdattribute attribute to the value of the Azure tenant ID.
NOTE: If you did not configure edsvaAzureAssociatedTenantIdattribute, an error will be logged for each object in the Event Viewer.
-
Configure the Forward Sync Rule to synchronize the following:
-
The Azure Object ID property of the Azure AD user or group to the edsvaAzureObjectID property of the corresponding on-premises Active Roles user or group.
-
Set the edsvaAzureOffice365Enabled attribute in the on-premises Active Roles user or group to true.
-
Set the edsvaAzureAssociatedTenantId attribute to the value of the Azure tenant ID.
-
Create a Mapping Rule. A mapping rule has two functions:
For example, the property userprincipalname can be used to map users between the on-premises AD and Azure AD in a federated environment.
|

|
CAUTION: Based on the environment, make sure to create the correct mapping rule to identify the user or group uniquely. Incorrect mapping rules may create duplicate objects, resulting in Azure BackSync not working as expected. |
NOTE: Consider the following when configuring manual Azure back-synchronization:
-
You must perform the initial configuration and back-synchronization of Azure AD user IDs only once.
-
Azure AD groups cannot be created in Federated or Synchronized environments. Instead, Azure AD groups are created in Active Roles and are synchronized to Azure AD using native Microsoft tools, such as AAD Connect. To manage the Azure AD group through Active Roles, you must perform periodic back-synchronization to the on-premises AD.

 (Settings) > Configure Azure BackSync option of the Active Roles
(Settings) > Configure Azure BackSync option of the Active Roles 
