Configuring each application
Configuring step-up authentication for an application is a two stage procedure. The:
- Front-end authenticator must be configured to support two factor authentication
- Application must be configured for step-up authentication.
|
|
NOTE: If multiple front-end authenticators are configured, step-up authentication is only available for users who authenticate with front-end authenticators that have two-factor authentication configured. |
To configure the front-end authenticator for step-up authentication
- Navigate to the Front-end Authentication page and click the name of the authenticator that you want to configure.
- Click the Two Factor Authentication tab.
- Select Use two factor authentication for specific applications.
- Configure the RADIUS connection settings if not already configured, please refer to Configuring a front-end authentication method for further information.
To configure the application for step-up authentication
- Navigate to the Applications page and click the name of the application that you want to configure.
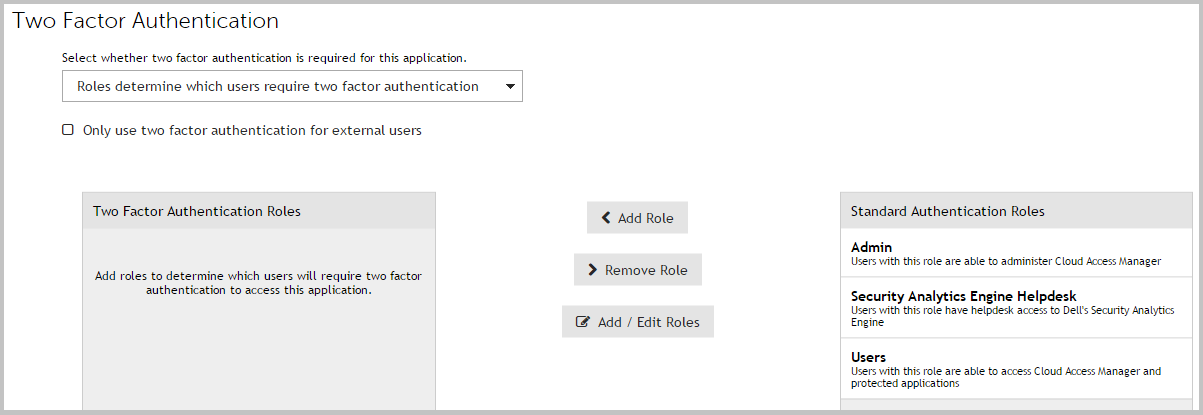
- Click the Two Factor Authentication tab.
-
From the list, select the users who will require two factor authentication to access the application. This will be either:
- All users of this application require two factor authentication, or
- Roles determine which users require two factor authentication.
-
If you are configuring role based access, select the required roles from the Standard authentication roles list and click Add Role to add the role to the list of Two factor authentication roles.
Configuring for external users
Two factor authentication may also be applied only for external users. In this context, external users are defined as users whose IP addresses do not fall in the following ranges:
- 10.0.0.0 - 10.255.255.255
- 172.16.0.0 - 172.31.255.255
- 192.168.0.0 - 192.168.255.255
Two factor authentication for external users may be configured either to apply to all applications, or it can be configured on a per application basis.
To configure two factor authentication for external users for all applications
- Navigate to the Front-end Authentication page and click on the name of the authenticator that you want to configure.
- Click the Two Factor Authentication tab.
- Select Use two factor authentication for all applications for external users only.
- Configure the RADIUS Connection Settings if not already configured, please refer to Configuring a front-end authentication method for further information.
To configure two factor authentication for external users for specific applications
- To configure the front-end authenticator follow the steps in To configure the front-end authenticator for step-up authentication.
- To configure the application follow the steps in To configure the application for step-up authentication.
- Select the Only use two factor authentication for external users check box on the application's Two Factor Authentication tab.
Configuring Starling 2FA with Cloud Access Manager
Configuring Starling 2FA with Cloud Access Manager
Starling 2FA is a cloud based authentication service that allows users to self-register and access their one time passwords on both mobile and desktop devices.
Purchasing a subscription
If you do not currently have a Starling 2FA subscription please email sales@oneidentity.com or telephone: 1-800-306-9329 for assistance.