-
Program the OneLogin Defender Token: Program the OneLogin Token from ADUC for the user and do not activate it.
-
Update User Properties: Update the below User Properties from the ADUC (Active Directory Users and Computers) to sync the users with the OneLogin:
- First Name
- Last Name
- Display Name
- Email (this email address will be used to login to OneLogin Portal with same AD Password)
-
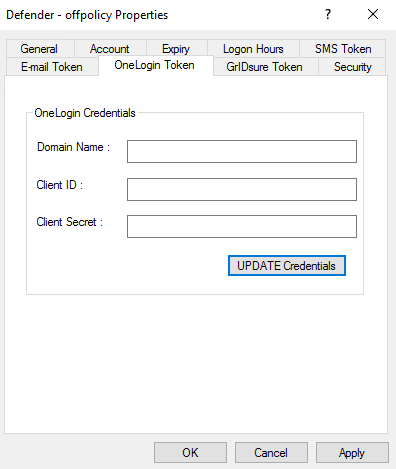
Input OneLogin API credential in Policy properties Dialog: On install/Upgrade to Defender version 6.5.0, a new tab named OneLogin Token under policies Properties Dialog is visible. Admin needs to enter OneLogin API credentials to use OneLogin Push Notification with OneLogin protect app for that policy. Click Apply to save the credentials. To update credentials, click UPDATE credentials.