Modifying Privilege Manager role properties
Once you open a Privilege Manager policy, the console lists the roles and restricted shell roles associated with it.
To modify Privilege Manager role properties
- From the PM Policy Editor view, double-click a role, select it and click Properties, or right-click the role and choose Properties from the context menu.
To find a particular policy role,
- Type a string in the Search for role box for either a name or a description. (This is case sensitive and searches dynamically.)
- Sort or filter the list of roles by type (enabled roles, disabled roles, enabled shell roles, or disabled shell roles) from the Role state column represented with the exclamation mark (!).
- Click a column title to sort the list of roles by name or description.
Note: Disabled roles are greyed out. However, you can modify or delete disabled roles.
When a role opens, the Edit Role dialog displays.
See Adding a Privilege Manager role or Add a Privilege Manager restricted shell role for details about the role properties.
Overriding role property defaults
If a role property has a global default, it will be indicated by the "default override" check box to the left of the property, in a green background, and the default role property to the right, in a disabled state. If a property does not have a "default override" check box, there is no global default for that property. For example, the following screen indicates the Enable role property does not have a global default, but the Enable keystroke logging property does. The default for the Enable keystroke logging property is Enabled.
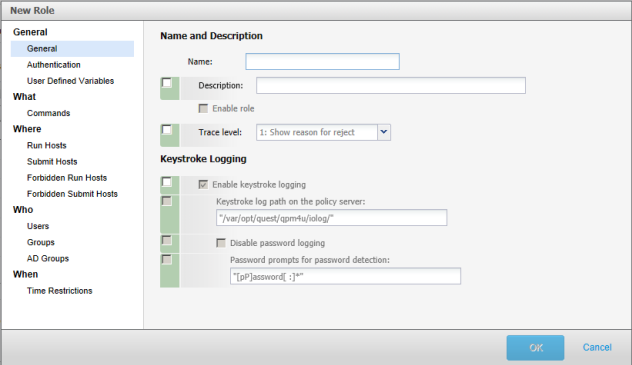
To override a global default
-
Select the override check box, change the role property, as needed, and click OK.
When you override the global default, the value you specify takes precedence over the global default and remains effective even if the global default changes.
NoteS:
- If you leave the global override check box deselected, the role uses the global default automatically. In the example above, the new role will have keystroke logging enabled and create the keystroke log in /var/opt/quest/qpm4u/iolog/ even though the override check boxes are not selected. If you always want keystroke logging to be enabled for this role even if the global default is changed in the future, select the override check box and leave the Enable keystroke logging option selected.
- You can set a global default for the Enable role property, applicable to all roles, using the text editor. See Managing role defaults for details.
Role property variables
Privilege Manager roles (or profiles) define who, what, where, when, and how users are permitted to perform various privileged account actions using variable values in the policy configuration file. You set the values for these user-defined variables in global_profile.conf, the default Privilege Manager policy configuration file, using either a GUI editor or a text editor.
The following tables identify the policy variables associated with each GUI editor setting for both Privilege Manager roles and restricted shell roles. The Manage Defaults column indicates which variables you can set as global defaults using the Manage Defaults button on the GUI editor; you must use the text editor to set global defaults for variables marked No. See Managing role defaults for details.
Table 5: General Settings
| General |
| Description |
Both |
pf_profiledescription |
No |
| Enable role |
Both |
pf_enableprofile |
No |
| Trace level |
Both |
pf_tracelevel |
Yes |
| Enable keystroke logging |
Both |
pf_enablekeystrokelogging |
Yes |
| Keystroke log path |
Both |
pf_iologdir |
Yes |
| Disable password logging |
Both |
pf_logpasswords |
Yes |
| Password prompts |
Both |
pf_passprompts |
Yes |
| Authentication |
| Require authentication |
Both |
pf_enableauthentication |
Yes |
| Authenticate on host running command |
Both |
pf_authenticateonclient |
Yes |
| PAM service |
Both |
pf_pamservice |
Yes |
| Command line prompt |
Both |
pf_pamprompt |
Yes |
| Allow scp / non-interactive SSH |
Shell |
pf_allowscp |
Yes |
Table 6: What Settings
| Commands |
| Path on host |
Role |
pf_authpaths |
Yes |
| Commands |
Role |
pf_authcmds |
Yes |
| Allow commands from authorized submit hosts |
Role |
pf_enableremotecmds |
Yes |
| Shell Commands |
| Accept only commands |
Shell |
pf_shellcommandsaccept |
No |
| Reject commands |
Shell |
pf_shellcommandsreject |
No |
| Authorize shell builtins |
Shell |
pf_checkbuiltins |
No |
| Command rejection message |
Shell |
pf_shellreject |
No |
| Pre-authorized Commands |
| Commands allowed by shell |
Shell |
pf_shellallow |
Yes |
| Commands allowed only from pipe |
Shell |
pf_shellallowpipe |
Yes |
| Commands rejected by shell |
Shell |
pf_shellforbid |
Yes |
Table 7: Where Settings
| Run Hosts |
| Hosts where commands can run |
Both |
pf_authrunhosts |
No |
| Submit Hosts |
| Hosts where commands can be submitted |
Role |
pf_authsubmithosts |
No |
| Forbidden Run Hosts |
| Hosts where members are forbidden to run commands |
Role |
pf_forbidrunhosts |
No |
| Forbidden Submit Hosts |
| Hosts where members are forbidden to submit commands |
Role |
pf_forbidsubmithosts |
No |
Table 8: Who Settings
| Users |
| Users authorized to run commands |
Both |
pf_authusers |
No |
| Runas User |
Both |
pf_authuser |
No |
| Groups |
| Local and Unix-enabled AD groups |
Both |
pf_authgroups |
No |
| Runas Group |
Both |
pf_authgroup |
No |
| User must be member of authorized group |
Both |
pf_useservergroupinfo |
No |
| AD Groups |
| Non Unix-enabled AD Groups |
Both |
pf_authgroupsad |
No |
| Default AD Domain |
Both |
pf_addomain |
No |
Table 9: When Settings
| Time Restrictions |
| Restrict by day, date, time |
Both |
pf_enabletimerestrictions |
Yes |
| By Time Period |
Both |
pf_restrictionhours |
Yes |
| By Date |
Both |
pf_restrictiondates |
Yes |
| By Day of Week |
Both |
pf_restrictiondow |
Yes |
Table 10: How Settings
| Shell Settings |
| PM secure shells allowed to run |
Shell |
pf_allowshells |
Yes |
| Run in restricted mode |
Shell |
pf_restricted |
Yes |
| Environment variables that cannot change |
Shell |
pf_shellreadonly |
Yes |
| Shell execution directory |
Shell |
pf_shellcwd |
Yes |
| Shell session PATH |
Shell |
pf_shellpath |
Yes |
Note: You can not manage the following variables using the GUI editor; you must use the text editor:
- pf_cpolicy -- the path to a customer-specific pmpolicy file included after matching the user to a profile, but before authenticating the user. If configured, add this file to the repository, and identify it using a relative path (relative to the policy directory).
- pf_realshell -- specifies the actual shell program to run, in the case of pmloginshell. Note: This variable is obsolete in vr 5.6.0 and only provided here only for reference to the obsolete vr 5.5.2 pmloginshell program.
- pf_forbidsubmithostsad -- Active Directory host groups where members are forbidden to submit commands.
- pf_authsubmithostsad -- Active Directory host groups where commands can be submitted.
- pf_forbidrunhostsad -- Active Directory host groups where members are forbidden to run commands.
- pf_authrunhostsad -- Active Directory host groups where commands can run.
Adding a Privilege Manager role
To create a new Privilege Manager role
- From the PM Policy Editor view, click the Add Role button.
- From the Select Role Type dialog, choose Privilege Manager Role and click OK.
The New Role dialog displays and allows you to specify:
- General Settings
- General Settings
- Authentication Settings
- User Defined Variables
- What Settings
- Where Settings
- Run Hosts Settings
- Submit Hosts Settings
- Forbidden Run Hosts Settings
- Forbidden Submit Hosts Settings
- Who Settings
- Users Settings
- Groups Settings
- AD Groups Settings
- When Settings
- Time Restrictions Settings
See Overriding role property defaults for more information about specifying role-specific overrides for a specific property.

