Use the following procedure to map a SAP account to an Active Directory account.
-
In SAP GUI, run transaction SU01 - User Maintenance:

-
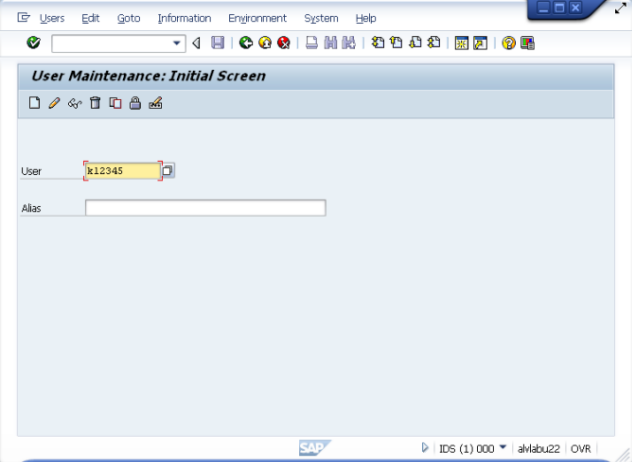
Create a new user or edit and existing user.
-
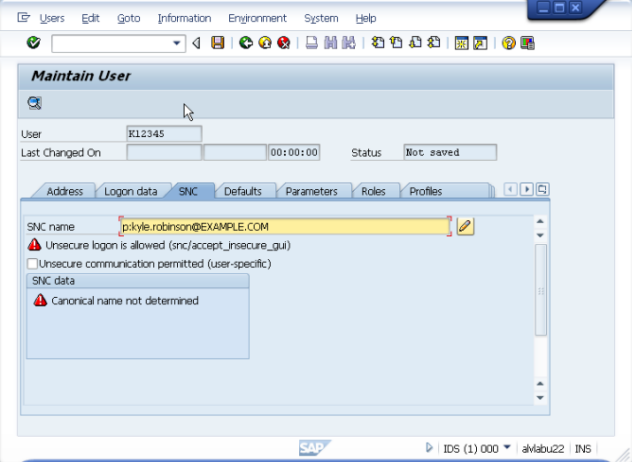
On the SNC tab, enter p: followed by the user's Implicit User Principal Name (sAMAccountName@DOMAIN) being careful to match case. Save the changes.
-
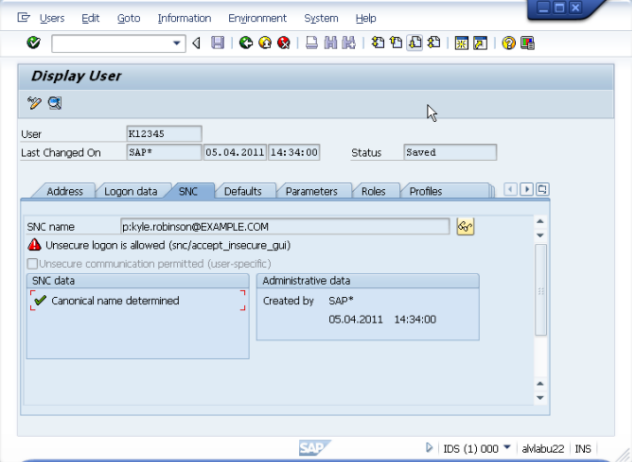
Return to the SNC tab to check for Canonical name determined.
-
Open the SSO configured SAP GUI connection as the Active Directory user, and connect to test SSO/SNC functionality.
Before you can configure your SAP Server, you must have Safeguard Authentication Services installed on your UNIX server and joined to the Active Directory domain. For instructions on how to install and join the domain, see the Safeguard Authentication Services product documentation.
Single Sign-on for SAP supports the SAP GUI on Windows XP, 2003, Vista, 2008, 7, and 2008 R2.
For a complete list of supported Unix and Linux platforms, see the Safeguard Authentication Services Installation Guide or Release Notes.
One Identity recommends the steps described in this section as a best practice for defining a distinct service account for SAP authentication.
Active Directory service accounts provide a means for authenticating and managing services and rights to access host resources. When you create a service account, it generates a random password for the account and a Kerberos keytab for the service. The previous section describes a configuration where SAP uses the host keytab, while this section describes the recommended configuration where SAP uses a service account.
Each service account has a KRB5 Principal Name (KPN) and an optional set of Service Principal Names (SPN’s). The KPN is the sAMAccountName of the service account (case sensitive) including the domain in the form "sAMAccountName@realm". The keytab file is created in the Safeguard Authentication Services configuration directory at /etc/opt/quest/vas. The default permissions on the keytab file are 0600 and the file is owned by root. You must update the ownership of the file so that the service has rights to read from the keytab file.
To create and use a Service Account for the SAP Service
-
Create the service account using vastool on the SAP Server host:
vastool –u Administrator service create SAP/
This command creates the /etc/opt/quest/qas/SAP.keytab file. Administrator is the name of the Active Directory user with administrative privileges to create a new service account. The user is prompted for their Active Directory password.
-
Set the password to "never expires" and "can not be changed": set the userAccountControl attribute by entering vastool -u administrator setattrs SAP/ userAccountControl 66048.
-
Change the file permissions on the newly created service.keytab file so that the corresponding service has the rights to read from the keytab file by entering chmod 640 /etc/opt/quest/vas/SAP.keytab.
Change the group ownership of the keytab to the sapsys group by entering chgrp sapsys /etc/opt/quest/vas/SAP.keytab.
-
Set the snc/identity/as value and the SNC Name (in Advanced Options of SAPlogin) to p:sAMAccountName@realm
where example.com is the name of the domain to which the R3 server is joined.
You can obtain the sAMAccountName of the service account by running vastool -u host/ attrs -q SAP/ sAMAccountName.
-
On the SAP Server, set the environment variable KRB5_KTNAME to the location of the previously created SAP.keytab file.
For example, in ~<instance>adm/.cshrc add setenv KRB5_KTNAME /etc/opt/quest/vas/SAP.keytab.
-
Restart the SAP services.




