Configuring a front-end authentication method
Microsoft® Active Directory® authentication
Configuring smart card authentication
LDAP authentication
Microsoft® Active Directory® LDS
389 Directory Service
Novell® eDirectory™
Windows Azure™ Active Directory® authentication
SAML federated
WS-Federated
Social authenticators
Integration with password management applications
Primary credentials
Configuring user front-end authentication method selection
Adding a web application
Integrated Windows Authentication
Form fill authentication
Proxy-less form fill authentication
SAML federation
Configuring advanced SAML token settings
Configuring advanced WS-Federation token settings
OpenID Connect/OAuth 2.0
Manual user provisioning
HTTP basic authentication
HTTP header value
No back-end SSO
Exporting an application configuration template
Forwarding claims to federated applications
Adding HTTP headers to proxy applications
Configuring step-up authentication
Configuring front-end authenticators
Configuring each application
Configuring for external users
Configuring Defender as a Service with Cloud Access Manager
Using Dell's Security Analytics Engine
Enabling Dell's Security Analytics Engine
Configuring Cloud Access Manager to use Dell's Security Analytics Engine for access control
Managing your SSL certificate
Obtaining a signed certificate
Replacing an expiring certificate
Installing a fully signed certificate from a certificate archive file
Installing a certificate authority certificate
Changing the Cloud Access Manager service account password
Cloud Access Manager IIS Application Pool
Dell Redistributable Secure Token Server
Front-end authenticators
Reporting
Customizing Dell™ One Identity Cloud Access Manager
SAML federated
This example uses Microsoft® AD FS v2 to federate users using SAML 2.0. However, it should be possible to use any SAML 2.0 compliant IDP.
|
1 |
Log in to the Administration Console and select Add New from the Front-end Authentication section on the home page. |
|
2 |
|
3 |
In the Federation Metadata URL field, enter the federation metadata URL provided by your IDP. The example URL shown below can be found in ADFS Management Console | Service | Endpoints | Metadata. https://<Host FQDN>/FederationMetaData/2007-06/FederationMetaData.xml |
Alternatively, click Browse to locate the file containing federation metadata. Refer to your IDP configuration interface for assistance with locating this information.
If you have entered the federation metadata URL as described above, click Next and skip to Step 6.
If you have entered the federation metadata URL as described above, click Next and skip to Step 6.
|
4 |
In the IDP Login URL field, enter the Issuer/IDP Service URL. For ADFS v2, this will be https://<FederationServiceName>/adfs/ls/. To find the Federation Service Name from the AD FS host, open the AD FS 2.0 management console and click Edit Federated Service Properties. |
|
5 |
Click Browse to locate and upload the contents of the IDP's public signing certificate in Base-64 encoded X.509 (.CER) format. |
For AD FS v2, this certificate is known as the Token-signing certificate. To obtain the certificate from the AD FS host, open the AD FS 2.0 management console, click Service | Certificates, then double-click the Token-signing certificate. From here, click Copy to file to save the certificate.
|
6 |
|
7 |
In the Authenticator Name field, enter the name that will be used to identify the authenticator within Cloud Access Manager, then click Finish. |
The Front-end Authentication Method Created page is now displayed. Leave this page open.
|
8 |
Before you click Edit Roles, we will switch to the SAML host (AD FS v2 in this case) and configure Cloud Access Manager as a Relying Party. |
|
9 |
|
10 |
Click Start to launch the wizard. |
|
• |
To configure this in AD FS, select Import data about the relying party published on a local network and enter the metadata URL shown in the Cloud Access Manager console. |
|
• |
Or download the Cloud Access Manager metadata from the console and select Import data about the relying party from a file to upload the file to AD FS and click Next. |
|
12 |
|
13 |
|
14 |
|
15 |
Select Enable support for the SAML 2.0 WebSSO protocol. |
|
16 |
Enter the Relying Party SAML 2.0 SSO service URL. To find this URL, switch back to the Cloud Access Manager console and copy the Recipient URL. For example, https://www.webapps.democorp.com/CloudAccessManager/RPSTS/Saml2/Login.aspx. Click Next. |
|
17 |
Enter the Relying party trust identifier. To find this information, switch back to the Cloud Access Manager console and copy the Audience/SP Identity value. For example, urn:CloudAccessManager/RPSTS. Click Add, then Next. |
|
18 |
|
20 |
|
21 |
Click Add Rule. |
|
22 |
|
23 |
Enter a claim rule name, for example Cloud Access Manager Claims. |
|
24 |
Set the Attribute store to Active Directory. |
|
25 |
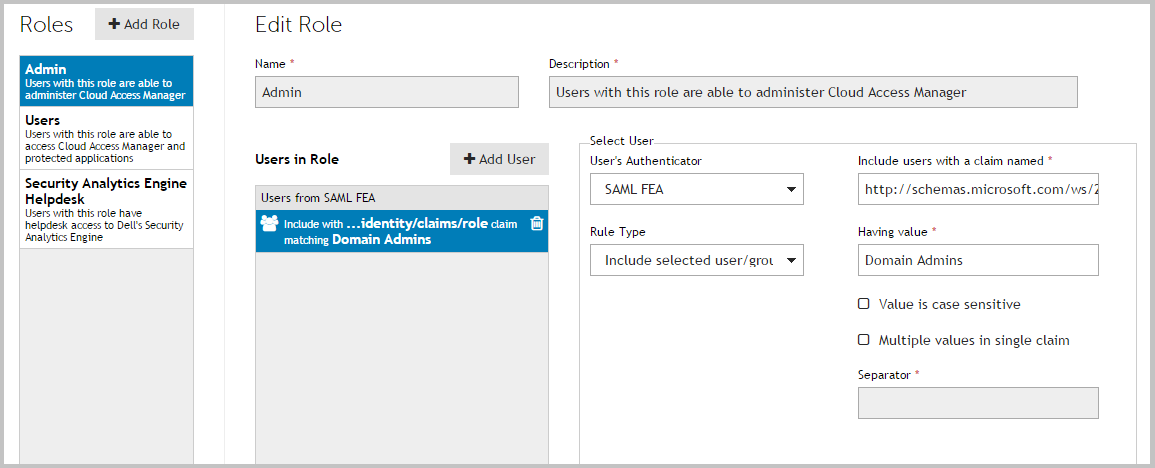
Select an LDAP Attribute of SAM-Account-Name and an Outgoing Claim Type of Name ID for the first claim mapping. This claim is required to identify the user to Cloud Access Manager. |
|
26 |
On the second row, select an LDAP Attribute of Token-Groups - Unqualified Name and an Outgoing Claim Type of Role. |
|
27 |
|
28 |
|
c |
In AD FS view the Properties for the newly created Relying Party Trust and switch to the Signature tab |
|
d |
Click Add… and select the Cloud Access Manager signing certificate. |
|
30 |
You now need to add the certificate to Trusted Root Certification Authorities so that it is trusted by ADFS. Go to the Signature tab in the ADFS Properties and click View... if the certificate is not trusted you will see a warning similar to the one below. 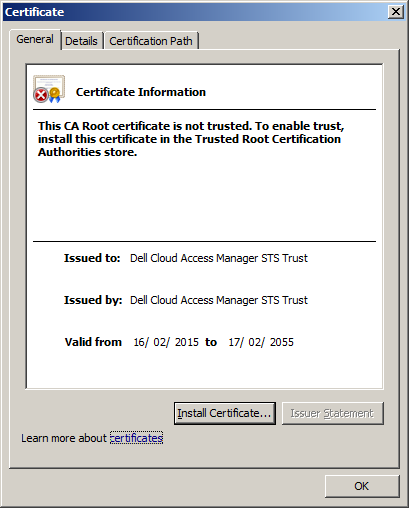 To allow the certificate to be trusted: |
|
a |
Click Install Certificate… |
|
b |
|
c |
|
d |
When the Security Warning dialog is displayed, confirm that the certificate is for Dell Cloud Access Manager STS Trust and click Yes. The certificate is now trusted. You can confirm this by closing and re-opening the certificate dialog. The certificate will now appear as below. 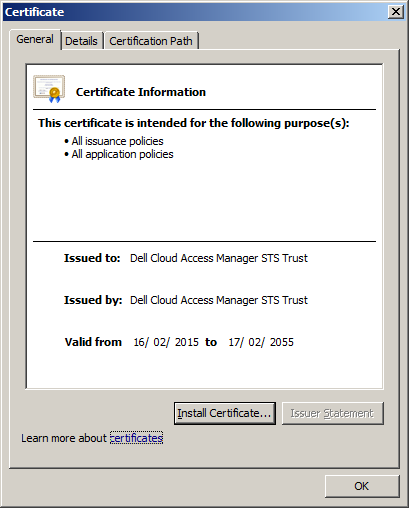 |
|
31 |
To complete the configuration you will need to set the hash algorithm for the relying party trust. In AD FS view Properties for the newly created Relying Party Trust, switch to the Advanced tab and select SHA-1 from the list of secure hash algorithms. Click OK. |
|
33 |
|
NOTE: By default Cloud Access Manager will look for claims of the type role. If you configured claims of a different type, update the Allow users with a claim named field with the different type. |
|
35 |
Click Admin. |
|
36 |
Click +Add User. |
|
38 |
|
39 |
|
40 |
|
42 |
Click Add User. |
|
43 |
Select the new SAML front-end authentication method from the list. |
|
44 |
|
45 |
Click Save. |
|
46 |
Click Close to return to the Cloud Access Manager Administration Console. |
The configuration is now complete. Cloud Access Manager administrators and users can now log in to Cloud Access Manager using their Active Directory federated credentials. For example, users who belong to the AD Domain Admins security group will be able to log in and configure Cloud Access Manager and all domain users will be able to log in to the Cloud Access Manager portal using their federated identity.
WS-Federated
This example uses Microsoft® AD FS v2 to federate users using WS-Federation.
|
1 |
Log in to the Administration Console and select Add New from the Front-end Authentication section on the home page. |
|
2 |
|
3 |
In the Federation Metadata URL field, enter the federation metadata URL provided by your IDP. The example URL shown below can be found in ADFS Management Console | Service | Endpoints | Metadata. |
Alternatively, click Browse to locate the file containing federation metadata. Refer to your IDP configuration interface for assistance with locating this information.
|
4 |
Enter the Endpoint URL. For AD FS v2 this will be https://<FederationServiceName>/adfs/ls/ . To obtain the Federation Service Name from the AD FS host, open the AD FS 2.0 management console and click Edit Federated Service Properties. |
|
5 |
Click Browse to locate and upload the contents of the IDP's public signing certificate in Base-64 encoded X.509 (.CER) format. For AD FS v2 this certificate is known as the Token-signing certificate. To obtain the certificate from the AD FS host, open the AD FS 2.0 management console, click Service Certificates, then double-click the Token-signing certificate. Click Copy to file to save the certificate. |
|
6 |
|
7 |
|
8 |
In the Authenticator Name field, enter the name that will be used to identify the authenticator within Cloud Access Manager, then click Finish. |
|
9 |
The Front-end Authentication Method Created page is displayed. Leave this page open. |
|
11 |
Click Start to launch the wizard. |
|
• |
To configure this in AD FS, select Import data about the relying party published on a local network and enter the metadata URL shown in the Cloud Access Manager console |
|
• |
Or download the Cloud Access Manager metadata from the console and select Import data about the relying party from a file to upload the file to AD FS, and click Next. |
|
13 |
Enter a name for the trust, for example Cloud Access Manager, then click Next. If using metadata skip to Step 19 |
|
14 |
|
15 |
Click Next on the optional token encryption page to skip this step. |
|
16 |
Select Enable support for the WS-Federation Passive protocol. |
|
17 |
Enter the Relying Party WS-Federation Passive protocol URL. To find this URL, switch back to the Cloud Access Manager console and copy the Relying Party Endpoint URL. For example, https://www.webapps.democorp.com/CloudAccessManager/RPSTS/WSFed/Login.aspx . Click Next. |
|
18 |
Enter the Relying party trust identifier. To find this information, switch back to the Cloud Access Manager console and copy the Relying Party Realm/Identity value. For example urn:CloudAccessManager/RPSTS. Click Add, then Next. |
|
19 |
Select Permit all users to access this relying party and click Next. |
|
21 |
|
22 |
Click Add Rule. |
|
23 |
|
24 |
Enter a claim rule name, for example Cloud Access Manager Claims. |
|
25 |
Set the Attribute store to Active Directory. |
|
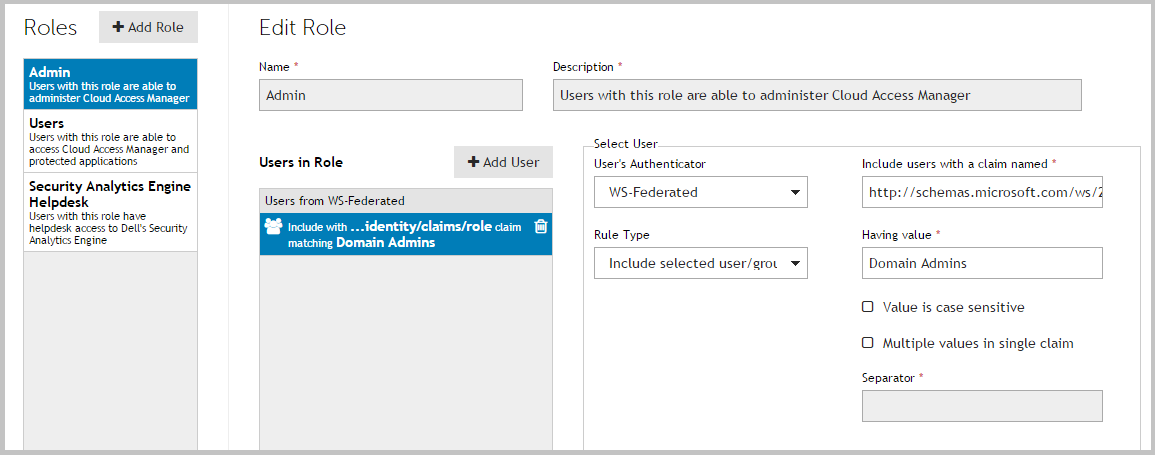
26 |
Select an LDAP Attribute of SAM-Account-Name and an Outgoing Claim Type of Name ID for the first claim mapping. This claim is required to identify the user to Cloud Access Manager. |
|
27 |
On the second row, select an LDAP Attribute of Token-Groups - Unqualified Names and an Outgoing Claim Type of Role. 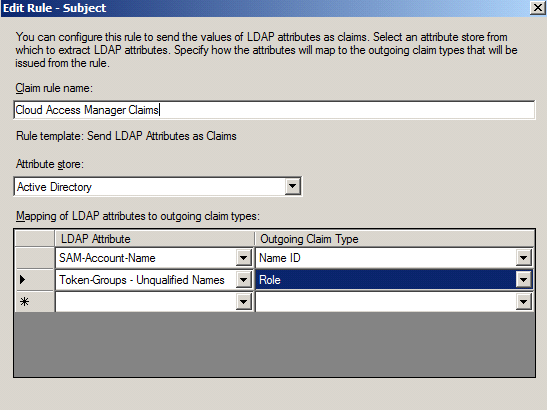 |
|
28 |
Click Finish. |
|
29 |
|
31 |
|
NOTE: By default, Cloud Access Manager will look for claims of the type role. If you configured claims of a different type, update the Allow users with a claim named field with the different type. |
|
33 |
Click Admin. |
|
34 |
Click +Add User. |
|
36 |
|
37 |
|
39 |
Click Add User. |
|
41 |
|
42 |
Click Close to return to the Cloud Access Manager Administration Console. |
The configuration is now complete. Cloud Access Manager administrators and users can now log in to Cloud Access Manager using their Active Directory federated credentials. For example, users who belong to the Active Directory Domain Admins security group will be able to log in and configure Cloud Access Manager, and all domain users will be able to log in to the Cloud Access Manager portal using their federated identity.
Social authenticators
Social authenticators allow users to link third party authenticators, for example Facebook, Google, Twitter and Microsoft® Live ID, with their Cloud Access Manager account.
For future logons, the user will only need to authenticate using either third party credentials or their Cloud Access Manager credentials. The user can unlink the accounts using the Manage Links option on the Navigate Menu on the Cloud Access Manager home page. The following example uses Microsoft Live ID as the third party authenticator.
|
1 |
Log in to the Cloud Access Manager Administration Console and select Add New from the Front-end Authentication section on the home page. |
|
2 |
|
3 |
On the Provider Settings page, complete the Client Id field with the client Id for your application in the Microsoft account Developer Center. |
|
4 |
In the Shared Secret field, enter the shared secret for your application in the Microsoft account Developer Center, then click Next. |
|
5 |
In the Authenticator Name field, enter the name that will be used to identify the authenticator within Cloud Access Manager, then click Finish. |
|
6 |
From the displayed Provider Settings, copy the Redirect URL and enter it as a redirect URL in the API Settings for the application in the Microsoft account Developer Center, then click Close. |
|
NOTE: Use of social authenticators must be enabled per directory authenticator, please refer to Microsoft® Active Directory® authentication and LDAP authentication for details on enabling social authentication for a directory authenticator. |
Integration with password management applications
When users authenticate using a directory authenticator, for instance Active Directory® or Lightweight Directory Access Protocol (LDAP), Dell™ One Identity Cloud Access Manager can link to password management software to allow users to reset their passwords or unlock their accounts.
Click Yes to open a new tab in the browser and load the password management application. If a user specific URL is configured, information about the authenticated user is communicated to the password management application.
|
1 |
Log in to the Administration Console, navigate to the Settings page and then to Turn Features On/Off. |
|
2 |
In the Password Management Options section enter the URL in the URL of password management application field. |
|
1 |
Log in to the Administration Console, navigate to the Settings page and then to Turn Features On/Off. |
|
2 |
In the Password Management Options section enter a URL in the URL of password management application with user information field. The following parameters may be inserted into the URL. |
|
1 |
Log in to the Administration Console, navigate to the Settings page and then to Turn Features On/Off. |
|
2 |
In the Password Management Options section enter the number of days before the password expiration reminder will be displayed. To prevent users being notified that their password is about to expire, set this value to zero. |