The following configuration parameters are additionally available in One Identity Manager after the module has been installed.
Table 6: Configuration parameters for managing software applications
|
Software |
Specifies whether software management is supported. |
|
Software | Application |
Preprocessor relevant configuration parameter to control the database model components for managing software. If the parameter is set, the components for managing software are available. Changes to this parameter require the database to be recompiled.
NOTE: If you disable the configuration parameter at a later date, model components and scripts that are no longer required, are disabled. SQL procedures and triggers are still carried out. For more information about the behavior of preprocessor relevant configuration parameters and conditional compiling, see the One Identity Manager Configuration Guide. |
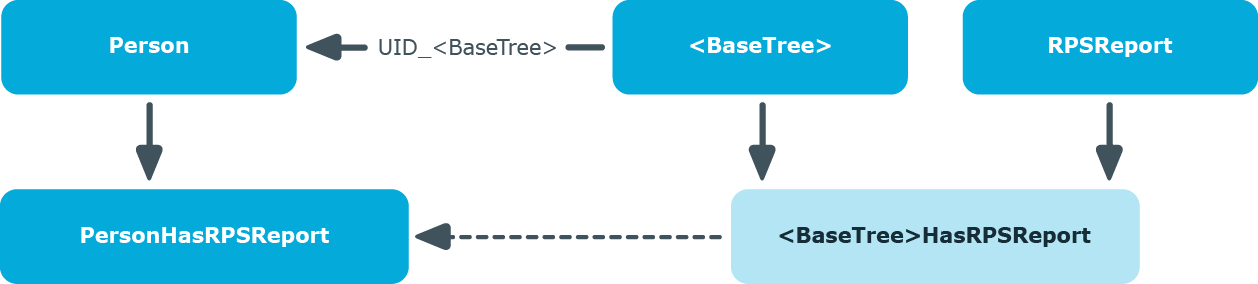
Identities can directly obtain software. Furthermore, identities inherit (and pass on) all software applications from all the roles of which they are members (PersonIn<BaseTree> table) as well as the software of all the roles that are referenced over a foreign key relationship (Person table, UID_<BaseTree> column). Direct and indirect assignments of software to identities are mapped in the PersonHasApp table.
A workdesk can directly obtain software. Furthermore, workdesks inherit (and pass on) all software applications from all the roles of which they are members (PersonIn<BaseTree> table) as well as the software of all the roles that are referenced over a foreign key relationship (Workesk table, UID_<BaseTree> column). Direct and indirect assignments of software to workdesks are mapped in the WorkdeskhasApp table.
Assignments of roles to software are stored in the <BaseTree>HasApp table. Software can also be inherited through system roles. For more information, see the One Identity Manager System Roles Administration Guide.
Figure 1: Inheritance with direct assignment of software to identities

Figure 2: Inheritance with indirect secondary assignment of software to identities

Figure 3: Inheritance with indirect primary assignment of software to identities