Password Manager provides the opportunity to granularly apply and manage password policies.
The following diagram shows available password policies and their structure:
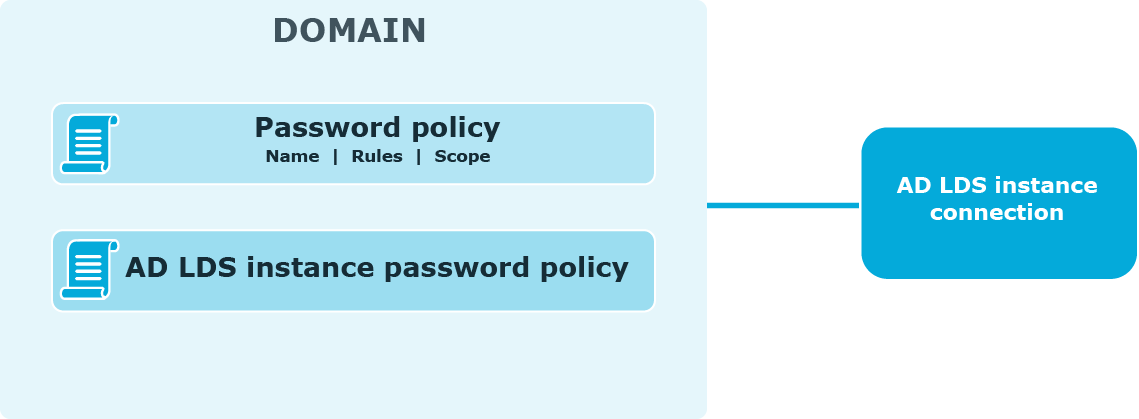
By default, AD LDS enforces the local or domain policy applied to the computer on which an AD LDS instance runs. You can also configure password policies. Note that the password policy applied to the computer on which the AD LDS instance runs cannot be automatically displayed on the Self-Service site when users change or reset passwords. To display such policy, use the Custom rule available in password policies. In this rule, enter the settings of the password policy applied to the computer running the AD LDS instance. For more information, see Custom Rule.
To create and manage password policies, you need to add a connection to the AD LDS instance on the Password Policies tab of the Administration site. When adding the connection, you specify the application directory partition to which password policies will be applied and the credentials that will be used to access the partition.
After you have added the connection, you can create password policies for this application directory partition. For each password policy, you can specify a name, a set of policy rules, and a scope.
Note that password policy rules are applied and displayed on the Self-Service site when users change or reset passwords, only after you have added the connection and created policies for the corresponding application directory partition.
If a user is found in the scopes of several password policies, then the policy with the highest priority is applied to the user. Note that priority can be changed for policies with the same scope.
This section provides an overview of the reCAPTCHA service, system requirements for using it and references.
reCAPTCHA V2 is a free CAPTCHA service provided by Google. You can use it to protect the Self-Service from bots attempting to access restricted areas.
As reCAPTCHA uses images that optical character recognition software has been unable to read, it provides a secure protection for websites.
-
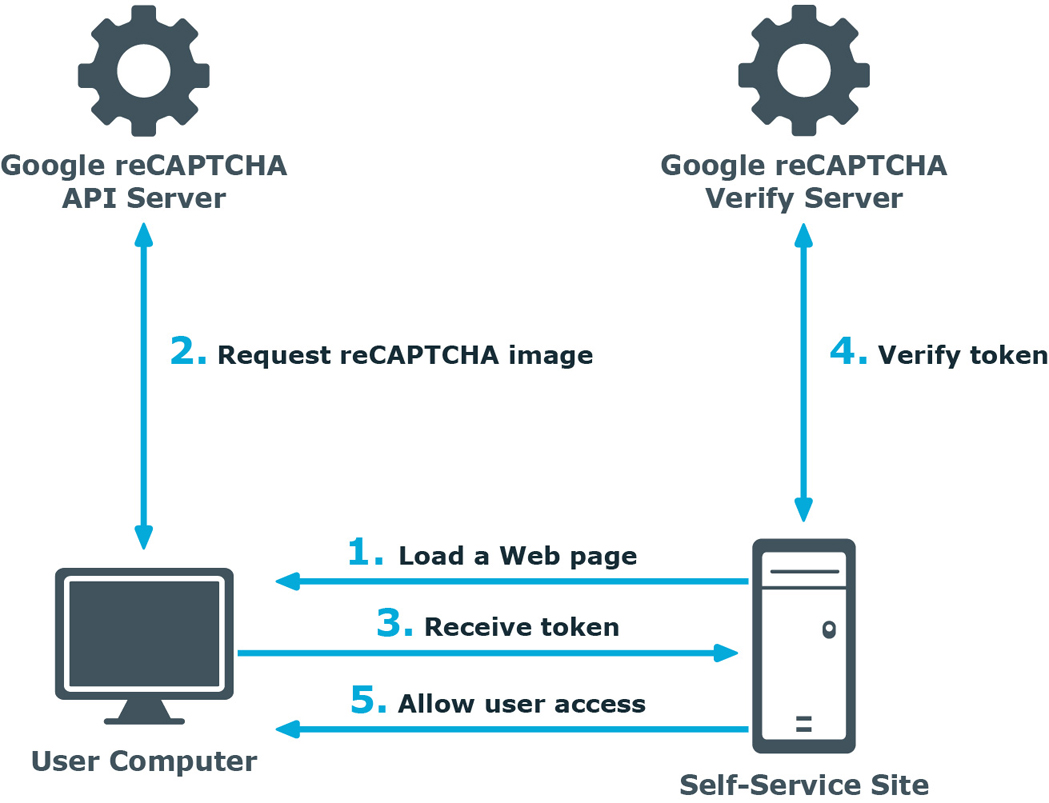
A user opens the Self-Service site.
-
The user’s browser sends the site key obtained during registration on the reCAPTCHA V2 site to the Google reCAPTCHA V2 API server and requires the user to select the check box indicating the user is not a robot.
-
Use this activity to verify reCAPTCHA on the Self-Service site. User must select the I'm not a robot check box before beginning a workflow. This will either pass the user immediately (with No CAPTCHA) or challenge them to validate whether or not they are human. This feature provides enhanced protection against automated attacks.
-
The token and the secret key (obtained during registration on the reCAPTCHA V2 site) are then transferred to the Google reCAPTCHA V2 Verify server to be checked. After checking the response, the reCAPTCHA V2 server sends a reply back to the Password Manager server.
-
If the response is correct, the user is granted access to further steps on the Password Manager site.
To display reCAPTCHA images on the Self-Service site, include the Display reCAPTCHA activity in required workflows. To require users to reply to a reCAPTCHA challenge before authentication, place the Display reCAPTCHA activity before any authentication activity in a workflow designer.
For more information on using reCAPTCHA in workflows, see Display reCAPTCHA.
You can also use reCAPTCHA on the Find Your Account page of the Self-Service site and require users to reply to the reCAPTCHA challenge before searching for their accounts. For more information, see Configuring Security Options.


