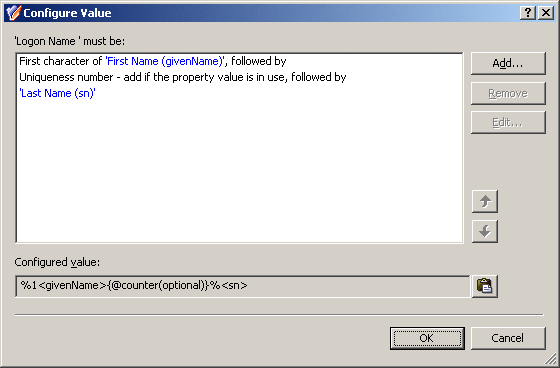
The User Logon Name Generation provisioning Policy Object type is used to automate the assignment of pre-Windows 2000 user login names when creating or modifying a user account, with flexible options to ensure the uniqueness of the policy-generated name.
For a detailed description of this policy, see Concept: User Logon Name Generation in the Active Roles Feature Guide.