You can configure the following login options under Users & Access Control > Settings:
-
Protect against brute-force attack
By default, the login addresses are protected against brute-force attacks. After the users reach the configured number of unsuccessful login attempts, SPS denies all following attempts for the configured time.
For more information, see Protecting against brute-force attacks.
-
Authentication banner
On the web and console login screen of SPS, you can display a banner that the users see every time they try to log in to SPS.
For more information, see Authentication banner.
-
Web interface timeout
You can configure the time after which SPS automatically logs the users out of the session.
For more information, see Web interface timeout.
This section describes the Protect against brute-force attacks option that you can configure on Users & Access Control > Settings.
How the Protect against brute-force attacks option works
By default, the web login addresses of administrators and users are protected against brute-force attacks. After the users reach the configured number of unsuccessful login attempts, SPS denies all following attempts for the configured time.
The Protect against brute-force attacks option blocks the user name or the IP address based on the following logic:
-
If the number of unsuccessful login attempts from the same IP address with any user name exceeds the threshold, the IP address is blocked.
-
If the number of unsuccessful login attempts with a user name from different IP addresses exceeds the configured threshold, the user name is blocked for all IP addresses.
The authentication attempts rejected by SPS during the blocking do not increase the lockout counters.
NOTE: The admin user is also subject to brute-force attack protection.
By default, Protect against brute-force attacks blocks the user name or the IP address for 10 minutes after 20 unsuccessful login attempts.
Accepted values:
Blocked users receive the Unable to authenticate error message, regardless of whether they enter valid or invalid credentials.
NOTE: The Unable to authenticate error message does not provide details about the error and the possible solutions to prevent providing information for attackers.
Log messages about blocked user names and IP addresses
If a user name or an IP address is blocked, a log event is created, which provides the details about the blocking. The log event contains the following information:
-
Cause of the blocking
-
User name
-
IP address
-
Duration of the blocking
Example: log message about a blocked user name
The following example provides the details about the blocking of a user name. The blocked user name is admin and the IP address used is 1.2.3.4. The reason for the blocking is that the user has exceeded the allowed number of unsuccessful authentication attempts. This user is blocked for 60 minutes.
Authentication denied, too many attempts, username is locked out; username='admin', remote_address='1.2.3.4', lockout='60 min'
Example: log message about a blocked IP address
The following example provides the details about the blocking of an IP address. The user is admin and the blocked IP address is 1.2.3.4. The reason for the blocking is that the allowed number of unsuccessful authentication attempts has been reached from this IP address. This IP address is blocked for 40 minutes.
Authentication denied, too many attempts, remote_address is locked out; username='admin', remote_address='1.2.3.4', lockout='40 min'
Unblocking blocked user names and IP addresses
SPS resets the web lockout counter for a user name or IP address if:
-
The lockout period is over.
-
The server is rebooted.
-
The secondary node becomes active after a High Availability (HA) failover.
-
After the root user clears the list of blocked users/IP addresses on the Troubleshooting page of the text-based physical or SSH console.
NOTE: If you are the root user, on the Troubleshooting page of the text-based physical or SSH console, you can clear the list of blocked user names and IP addresses using the Clear list of blocked users/IPs option. If you clear the list, users and IP addresses that previously were blocked due to exceeding the allowed number of web login attempts can attempt logging in again. Clearing the list does not disable the Protect against brute-force attacks option.
Configuring the Protect against brute-force attack option
To configure the Protect against brute-force attacks option
-
Navigate to Users & Access Control > Settings — Protect against brute-force attacks.
Figure 79: Users & Access Control > Settings — Protect against brute-force attacks
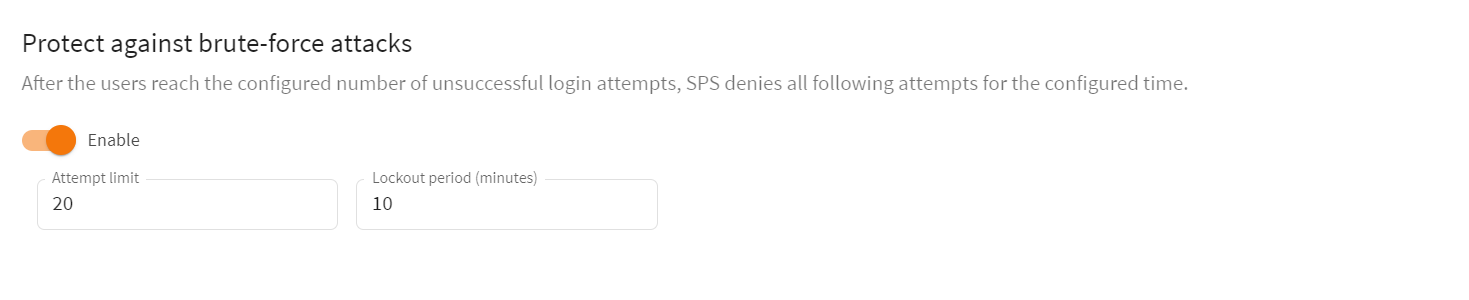
- (Optional) Modify the default values of Attempt limit, Lockout period, or both, according to your security requirements.
- To save the modifications, click Commit changes.
You can display a banner with a configurable text on the web and console login screen of One Identity Safeguard for Privileged Sessions (SPS).
Users will see the banner every time they try to log in to SPS. The login screen displays the banner text as plain text, with whitespaces preserved.
To enter a banner message, navigate to Users & Access Control > Settings — Authentication banner.
Figure 80: Users & Access Control > Settings > Authentication banner — Enter a banner message
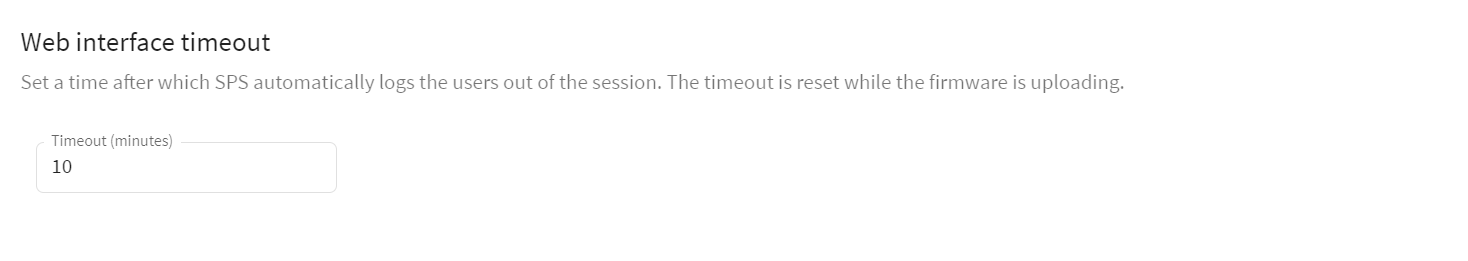
By default, One Identity Safeguard for Privileged Sessions (SPS) terminates the web session of a user after 10 minutes of inactivity. To change the value of this timeout, adjust the Users & Access Control > Settings > Web interface timeout option.
Figure 81: Users & Access Control > Settings — Web interface timeout