Primary assignment of company resources
You make a primary assignment using a department, cost center, or location foreign key reference in identity, device and workdesk objects. To do this, use the role fields on the identity, device, and workdesk main data forms. Primary assignment inheritance can be enabled through configuration parameters. Primary assignment is enabled for identities by default.
Figure 8: A primary assignment schema
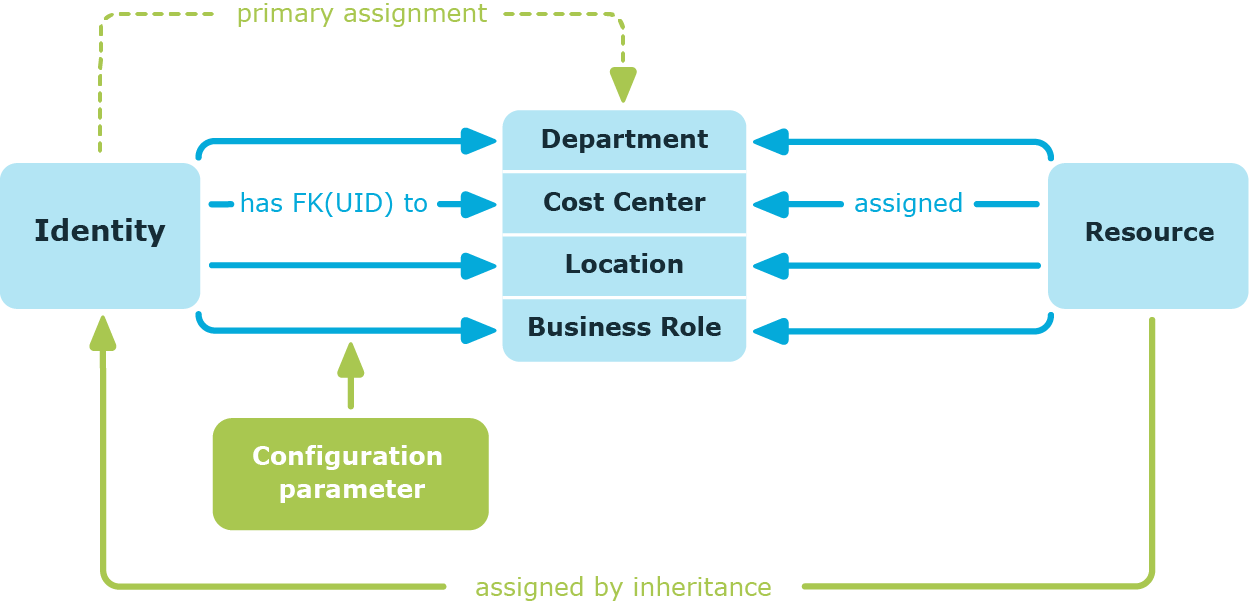
NOTE: Changes to the configuration parameter result in the inheritance data being recalculated! That means: if the primary assignment is disabled at a later date, the inheritance data created in this way will be removed from the database.
Table 1: Configuration parameters for primary assignment
|
QER | Structures | Inherite | Person |
Identities can inherit through primary assignment. |
|
QER | Structures | Inherite | Person | GroupExclusion |
Identities inherit assignments from their primary department (Person.UID_Department). |
|
QER | Structures | Inherite | Person | FromLocality |
Identities inherit assignments from their primary location (Person.UID_Locality). |
|
QER | Structures | Inherite | Person | FromProfitCenter |
Identities inherit assignments from their primary cost center (Person.UID_ProfitCenter). |
|
QER | Structures | Inherite | Hardware |
Devices can inherit through primary assignment. |
|
QER | Structures | Inherite | Hardware | FromDepartment |
Devices inherit assignments from their primary department (Hardware.UID_Department). |
|
QER | Structures | Inherite | Hardware | FromLocality |
Devices inherit assignments from their primary location (Hardware.UID_Locality). |
|
QER | Structures | Inherite | Hardware | FromProfitCenter |
Devices inherit assignments from their primary cost center(Hardware.UID_ProfitCenter). |
|
QER | Structures | Inherite | Workdesk |
Workdesks can inherit though primary assignment. |
|
QER | Structures | Inherite | Workdesk | FromDepartment |
Workdesks inherit assignments from their primary department (Workdesk.UID_Department). |
|
QER | Structures | Inherite | Workdesk | FromLocality |
Workdesks inherit assignments from their primary location (Workdesk.UID_Locality). |
|
QER | Structures | Inherite | Workdesk | FromProfitCenter |
Workdesks inherit assignments from their primary cost center (Workdesk.UID_ProfitCenter). |
Assigning company resources through dynamic roles
Assignment through dynamic roles is a special case of indirect assignment. Dynamic roles are used to specify role memberships dynamically. Identities, devices, and workdesks are not permanently assigned to a role, just when they fulfill certain conditions. A check is performed regularly to assess which identities, devices, or workdesks fulfill these conditions. This means the role memberships change dynamically. For example, company resources can be assigned dynamically to all identities in a department in this way; if an identity leaves the department they immediately lose the resources assigned to them.
Related topics
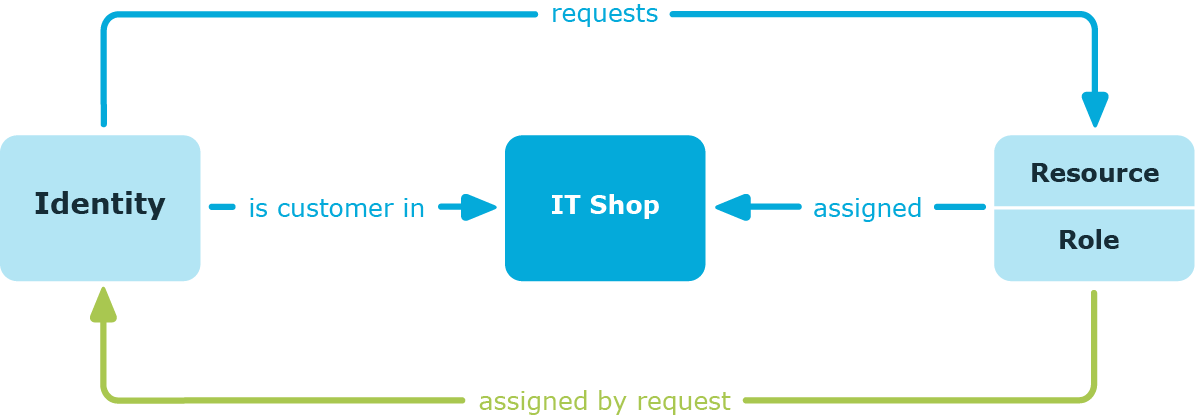
Assigning company resources through IT Shop requests
Assignment through the IT Shop is a special case of indirect assignment. Add identities to a shop as customers so that company resources can be assigned through IT Shop requests. All company resources assigned as product to this shop can be requested by the customers. Requested company resources are assigned to the identities after approval is granted. Role memberships can be requested through the IT Shop as well as company resources.
Figure 9: Schema of assignment by requests
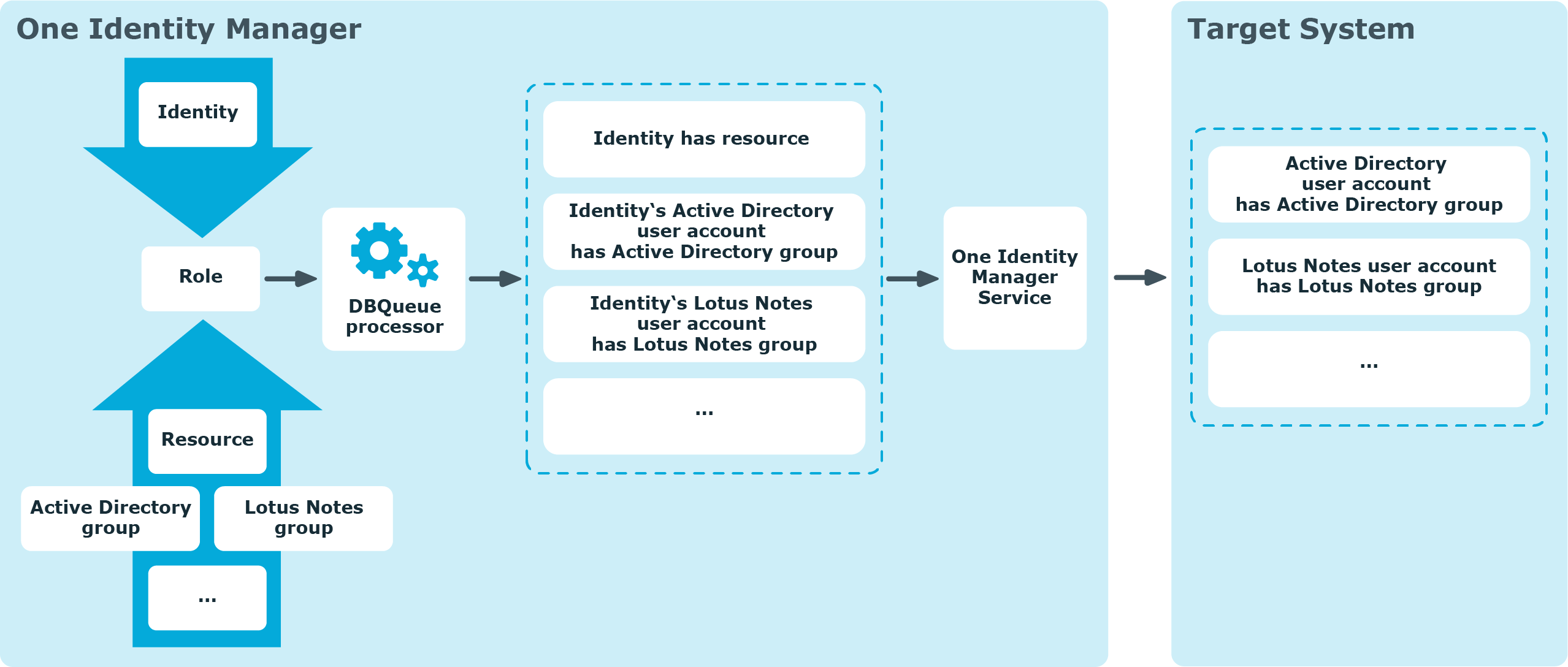
Basics of calculating inheritance
Objects assigned through inheritance are calculated by the DBQueue Processor. Tasks are added to the DBQueue when assignments relevant to inheritance are made. These tasks are processed by the DBQueue Processor and result in follow-on tasks for the DBQueue or in processes for process component HandleObjectComponent in the Job queue. Resulting assignments of permissions to user accounts in the target system are inserted, modified, or deleted during process handling.
Figure 10: Overview of inheritance calculation
Detailed information about this topic



