Steps for creating an Access Template
To create an Access Template
- In the console tree, under Configuration | Access Templates, locate and select the folder in which you want to add the Access Template.
You can create a new folder as follows: Right-click Access Templates and select New | Access Template Container. Similarly, you can create a sub-folder in a folder: Right-click the folder and select New | Access Template Container.
- Right-click the folder, and select New | Access Template to start the New Object - Access Template wizard.
- On the first page of the wizard, do the following, and then click Next:
- In the Name box, type a name for the Access Template.
- In the Description box, type any optional information about the Access Template.
- On the second page of the wizard, configure the list of permission entries, and then click Next.
The instructions on how to add, modify, or delete permission entries are given later in this topic.
- Click Finish to create the Access Template that includes the permission entries you have specified.
To add a permission entry to an Access Template
- On the page that displays a list of permission entries included in the Access Template, click Add to start the Add Permission Entries wizard.
- On the first page of the wizard, select one of these options:
- All object classes The rights defined by this permission entry apply to objects of any class.
- Only the following classes The rights defined by this permission entry apply to objects of specific classes. Select object classes from the list. If the list does not include the object class you want, select Show all possible classes.
- Click Next.
- On the second page of the wizard, select one of these options:
- Full control access The rights to create or delete child objects, read and write properties, examine child objects and the object itself, add and remove the object from the directory, and read or write with any extended right. This option does not have any configuration parameters.
- Object access The rights to exercise certain generic permissions and extended rights on the objects. Select permissions and extended rights from the list to configure this option as appropriate.
- Object property access The rights to read or write certain properties of the object. Select check boxes to configure this option as appropriate: Read properties, Write properties. On the next page of the wizard, you can select the properties you want to be controlled by this permission entry.
- Creation/Deletion of child objects The rights to create or delete child objects of the object. Select check boxes to configure this option as appropriate: Create child objects, Delete child objects, Move objects into this container. On the next page of the wizard, you can specify the class or classes of child object you want to be controlled by this permission entry.
- If you want the Access Template to deny the rights defined by this permission entry, select the Deny permission check box. Otherwise, leave the check box cleared.
- Do the following, depending on the option you selected and configured in Step 4:
- Full control access or Object access Click Finish to add the permission entry to the Access Template.
- Object property access or Creation/Deletion of child objects Click Next to continue configuring the option.
- On the third page of the wizard, continue configuring the option you selected in Step 4, and then click Finish to add the permission entry to the Access Template:
- If you selected Object property access, select the properties to be controlled by this permission entry. You have two options: All properties and The following properties. With the second option, you must select properties from the list. If the list does not include the property you want, select Show all possible properties.
- If you selected Creation/Deletion of child objects, specify the class or classes of child object to be controlled by this permission entry. You have two options: Child objects of any class and Child objects of the following classes. With the second option, you must select one or more object classes from the list. If the list does not include the object class you want, select Show all possible classes.
To view or modify a permission entry in an Access Template
- On the page that displays a list of permission entries included in the Access Template, select the permission entry you want to view or modify, and click View/Edit to display the Modify Permission Entry dialog box.
- Examine the Apply Onto tab in the Modify Permission Entry dialog box. On this tab, you can view or modify the same settings as on the first page of the Add Permission Entries wizard (see Step 2 in the procedure above).
- Examine the Permissions tab in the Modify Permission Entry dialog box. This tab provides the same options as the second page of the Add Permission Entries wizard (see Step 4 in the procedure above). The options are read-only, so you cannot change the option that was selected upon creation of the permission entry. However, you can manage the configuration of the option:
- Object access Select generic permissions or extended rights you want to add to the Access Template.
- Object property access Select or clear these check boxes: Read properties, Write properties.
- Creation/Deletion of child objects Select or clear these check boxes: Create child objects, Delete child objects, Move objects into this container.
- If you want the Access Template to deny the rights defined by this permission entry, select the Deny permission check box on the Permissions tab. Otherwise, leave the check box cleared.
- If Object property access is selected on the Permissions tab, use the Object Properties tab in the Modify Permission Entry dialog box to view or modify the settings that determine which properties are controlled by this permission entry (see Step 7 in the procedure above).
- If Creation/Deletion of child objects is selected on the Permissions tab, use the Object Classes tab in the Modify Permission Entry dialog box to view or modify the settings that determine which classes of child object are controlled by this permission entry.
To delete a permission entry from an Access Template
- On the page that displays a list of permission entries included in the Access Template, select the permission entry you want to delete, and click Remove.
- Click Yes to confirm the deletion.
Applying Access Templates
You can assign permissions to Active Directory (AD) objects with Access Templates (ATs) in the Active Roles Console.
Delegating permissions with ATs is an effective method to grant specific types of access for specific users or groups to specific organizational resources. For example, directory administrators of a domain can receive full control for managing that domain, while helpdesk operators can quickly receive permission to reset passwords for domain users.
Active Roles supports specifying ATs to all AD object types: administrative views (Managed Units), directory folders (containers), or individual (leaf) objects as well. When applying an AT to an AD object, you:
-
Designate a trustee (also known as security principal) who will receive the permissions granted by the AT. Trustees are typically users or groups.
-
Assign permissions to that trustee for the AD object in the scope of the AT. Such AD objects are called securable objects.
As a result, the trustee receives access to the securable object according to the permissions defined in the AT.
You can apply ATs to an AD object with the Delegation of Control Wizard. To start the wizard, navigate to either:
-
The AT you want to apply on an AD object. When you start the Delegation of Control Wizard this way, you can select the securable AD objects for which the access is granted, and the trustees who receive the access to those securable objects.
For the steps of this procedure, see Applying an Access Template directly.
-
The securable AD object (container, Managed Unit or leaf object) whose access and administration permissions you want to configure. When you start the Delegation of Control Wizard this way, you can select the trustees who receive the access to the securable object and the ATs defining the permissions of the trustees to the securable object.
For the steps of this procedure, see Applying Access Templates on a securable object.
-
The trustee for which you want to assign permissions. When you start the Delegation of Control Wizard this way, you can select the securable AD object to which the trustee will receive access and the ATs defining the permissions of the trustee to the securable object.
For the steps of this procedure, see Applying Access Templates on a user or group.
NOTE: ATs support propagating their permission settings for the child objects of the securable objects too.
Applying an Access Template directly
You can configure permissions for a trustee to a securable Active Directory (AD) object via an Access Template (AT) by selecting the AT directly in the Active Roles Console.
To apply an Access Template on a trustee or trustees
-
In the Active Roles Console, in the Active Directory (AD) tree, navigate to Configuration > Access Templates.
-
Right-click the AT you want to assign to a trustee (or trustees), then click Links.
TIP: For more information on the ATs, see the Description of the AT or the Active Roles Built-in Access Templates Reference Guide document.
-
In the Links dialog, to start the Delegation of Control Wizard, click Add. Click Next on the Welcome page, when it appears.
-
In the Objects step, specify the securable objects that you want to add to the scope of the AT.
-
To specify a new securable object or objects, click Add. Then, in the Select Objects window, locate and select the securable objects you want to add to the scope of the AT, and click Add.
Once you finalized the list, to close the Select Objects window and apply your selection, click OK.
TIP: If no securable objects appear in the window, use the Click here to display objects link.
Figure 16: Delegation of Control Wizard – Select objects window when specifying securable objects

Figure 17: Delegation of Control Wizard – Selecting securable objects

-
To remove securable objects added earlier to the scope of the AT, select them in the Objects step, and click Remove.
To continue, click Next.
-
In the Users or Groups step, specify the trustee(s) for which you want to grant the permissions of the AT.
-
To specify a new trustee or new trustees, click Add. Then, in the Select Objects window, locate and select the users or groups you want to add to the scope of the AT, and click Add. Once you finalized the list, to close the Select Objects window and apply your selection, click OK.
TIP: If no users or groups appear in the window, use the Click here to display objects link.
Figure 18: Delegation of Control Wizard – Select Objects window when specifying trustees
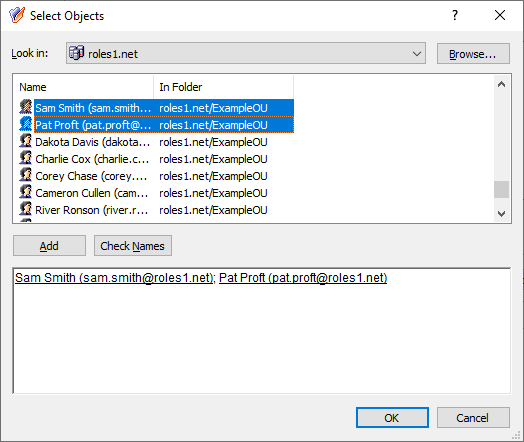
Figure 19: Delegation of Control Wizard – Selecting trustees

-
To remove existing trustees added earlier to the scope of the AT, select them in the Users or Groups step, and click Remove.
To continue, click Next.
-
In the Inheritance Options step, specify with the Apply permissions onto setting the scope of securable objects to which Active Roles applies the permissions of the AT:
-
This directory object: Trustees receive the AT permissions only to the selected securable object.
-
Child objects of this directory object: Trustees receive the AT permissions to the children of the securable object. To limit the granted permissions only to the direct children of the object, select Immediate child objects only as well.
Figure 20: Delegation of Control Wizard- Inheritance Options
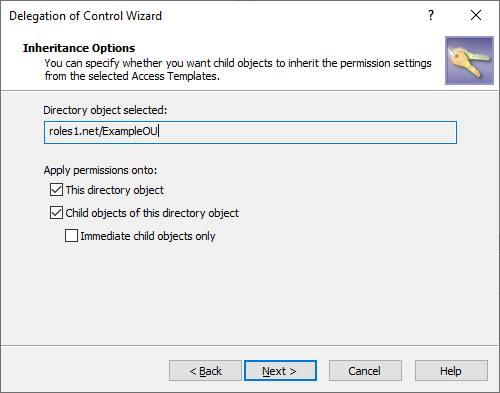
To continue, click Next.
-
In the Permissions Propagation step, to synchronize the configured permission settings to the native Active Directory (AD) access controls, select Propagate permissions to Active Directory.
Figure 21: Delegation of Control Wizard – Permissions propagation
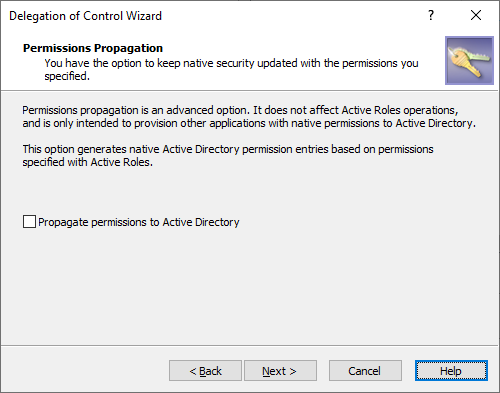
Selecting this setting will modify the authorization information of the AD objects with the permission settings defined in Active Roles, providing more flexibility for users and groups that use native AD management tools besides Active Roles.
IMPORTANT: Selecting this setting will result in trustees keeping their configured permissions outside of the Active Roles environment, with the potential risk of bypassing policies configured and enforced with Active Roles.
Therefore, select this option only if the selected trustees have the required security clearance and/or meet all security guidelines in effect within your organization.
TIP: Once Propagate permissions to Active Directory is selected and configured, you can change this setting at any time with the Active Roles Security > Sync to AD setting, or with the Advanced Details > Sync to AD setting. For more information, see Synchronizing permissions to Active Directory.
To continue, click Next.
-
To complete the wizard, click Finish.
Applying Access Templates on a securable object
You can configure permissions for a trustee (or trustees) to a securable Active Directory (AD) object via Access Templates (ATs) by selecting the securable object in the Active Roles Console.
To configure permissions with an Access Template from a securable object
-
In the Active Roles Console, in the Active Directory (AD) tree, navigate to the securable object for which you want to configure an AT.
-
To open the Delegation of Control Wizard from the securable object:
-
If the securable object is a container or Managed Unit, right-click the object, then click Delegate Control > Add.
-
If the securable object is a leaf object, right-click the object and click Properties. Then, in the Properties window, click Administration > Security > Add.
When the Welcome screen of the Delegation of Control Wizard appears, click Next.
-
In the Users or Groups step, specify the trustee(s) for which you want to grant the permissions of the AT.
-
To specify a new trustee or new trustees, click Add. Then, in the Select Objects window, locate and select the users or groups you want to add to the scope of the AT, and click Add. Once you finalized the list, to close the Select Objects window and apply your selection, click OK.
TIP: If no users or groups appear in the window, use the Click here to display objects link.
Figure 22: Delegation of Control Wizard – Select Objects window when specifying trustees

Figure 23: Delegation of Control Wizard – Selecting trustees

-
To remove existing trustees added earlier to the scope of the AT, select them in the Users or Groups step, and click Remove.
To continue, click Next.
-
In the Access Templates step, specify the ATs you want to assign to the selected trustees for the configured securable object. Expand the containers of the ATs, then select the AT or ATs you want to apply.
Figure 24: Delegation of Control Wizard – Selecting Access Templates
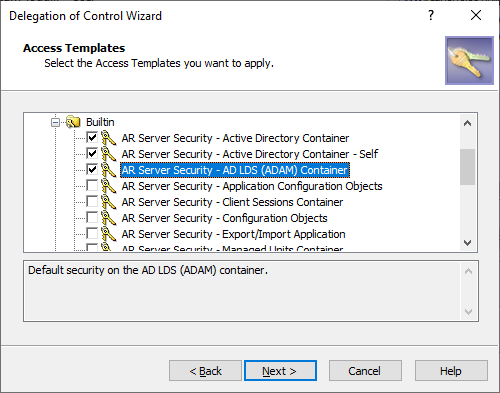
To continue, click Next.
-
In the Inheritance Options step, specify with the Apply permissions onto setting the scope of securable objects to which Active Roles applies the permissions of the AT:
-
This directory object: Trustees receive the AT permissions only to the selected securable object.
-
Child objects of this directory object: Trustees receive the AT permissions to the children of the securable object. To limit the granted permissions only to the direct children of the object, select Immediate child objects only as well.
Figure 25: Delegation of Control Wizard- Inheritance Options

To continue, click Next.
-
In the Permissions Propagation step, to synchronize the configured permission settings to the native Active Directory (AD) access controls, select Propagate permissions to Active Directory.
Figure 26: Delegation of Control Wizard – Permissions propagation

Selecting this setting will modify the authorization information of the AD objects with the permission settings defined in Active Roles, providing more flexibility for users and groups that use native AD management tools besides Active Roles.
IMPORTANT: Selecting this setting will result in trustees keeping their configured permissions outside of the Active Roles environment, with the potential risk of bypassing policies configured and enforced with Active Roles.
Therefore, select this option only if the selected trustees have the required security clearance and/or meet all security guidelines in effect within your organization.
TIP: Once Propagate permissions to Active Directory is selected and configured, you can change this setting at any time with the Active Roles Security > Sync to AD setting, or with the Advanced Details > Sync to AD setting. For more information, see Synchronizing permissions to Active Directory.
To continue, click Next.
-
To complete the wizard, click Finish.







