Two-factor authentication
You can configure Cloud Access Manager to enforce two-factor authentication. When the user attempts to access a Cloud Access Manager resource after entering their username and password, Cloud Access Manager makes a program call to an authentication service such as that provided by One Identity Defender. Cloud Access Manager will broker the authentication request between the user and the authentication service. The user will be asked for additional credentials according to the policy defined at the authentication service. For instance, the authentication service may require the user to enter a one-time password as generated by a handheld authentication device, usually referred to as an authentication token.
|
|
NOTE: This feature requires authentication software, for example One Identity Defender, which is compliant with the Remote Authentication Dial-In User Service (RADIUS) protocol. |
Web proxy and password wallet
Cloud Access Manager’s web proxy component runs on a network perimeter and acts as a security gateway between users located on an untrusted network and applications running on a trusted network. It acts as a Secure Sockets Layer (SSL) endpoint relaying Secure HTTP (HTTPS) packets between the user’s browser and the web application.
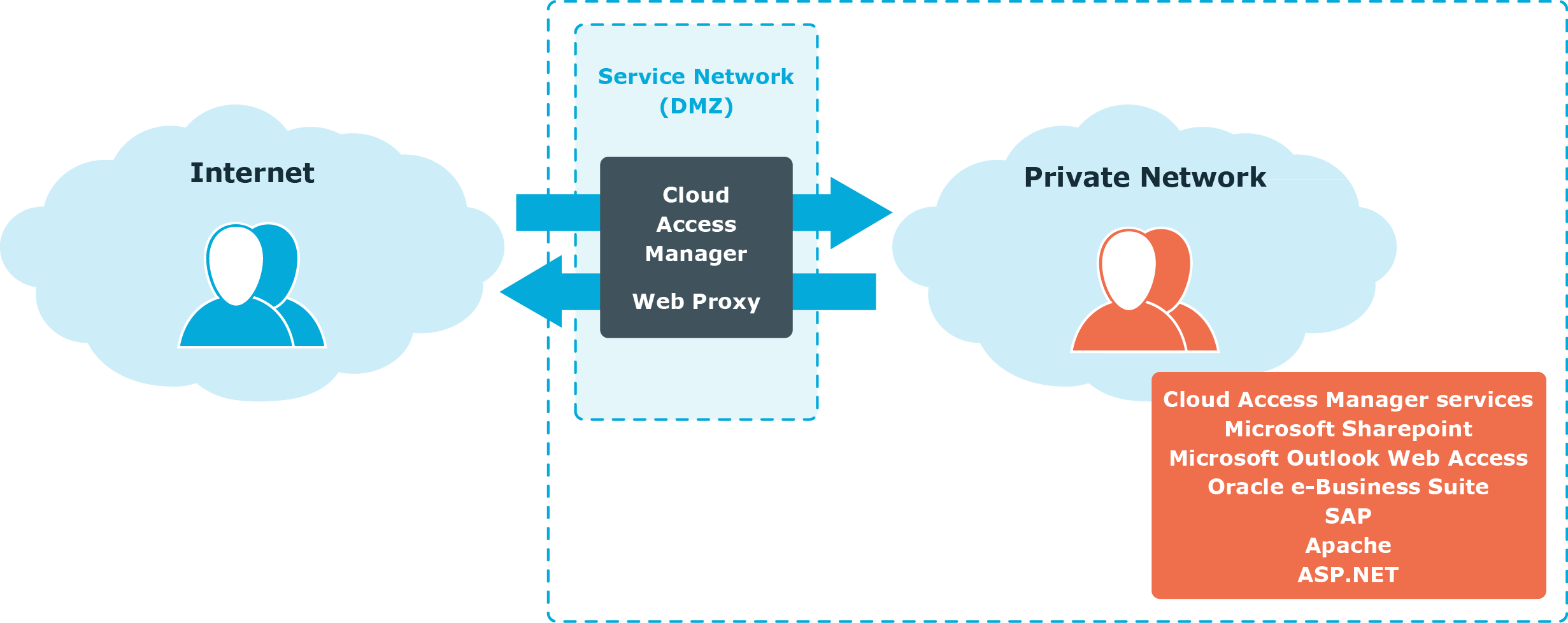
In addition to providing URL-based access control to firewalled applications, the web proxy also protects Cloud Access Manager web components such as the Security Token Service (STS) login pages, application portal and administration interface. The web proxy enforces authentication and authorization policies to applications running on the trusted network.
Because the web proxy stands between the user’s browser and the web application, it can automatically log the user onto their applications by learning the user’s application credentials, and inserting them when the user launches the application. When you configure an application, you can associate a login page URL with that application.
When the user attempts to access that URL, Cloud Access Manager automatically inserts the stored application user name and password into the appropriate form controls and posts the completed form back to the server. If Cloud Access Manager does not know the user’s application credentials it prompts the user for them. The user’s application credentials are encrypted in a Password Wallet within Cloud Access Manager’s configuration database, the user can view and update the Password Wallet from the Application Portal.
Form-fill single sign-on without a proxy
While the use of a reverse HTTP proxy is effective as a method of exposing internal applications to external users, it also carries with it an associated cost, such as hardware deployment and maintenance and implies a performance degradation. For this reason if alternatives are available, the use of a reverse proxy solely to effect automated sign on to a web application is not the preferred method.
Cloud Access Manager makes it possible to launch certain web applications directly from the application portal, without the need to proxy the application. This can be useful in scenarios where extranet access to the application is not required.
Application coverage and support
Cloud Access Manager offers a number of options for implementing Single Sign-On (SSO) to applications, as well as the ability to expose applications to users using a reverse HTTP proxy.
While the majority of applications are supported using the technologies delivered by Cloud Access Manager, there may be certain applications that are not supported. Please contact Support if you have questions regarding support for any specific application.
|
|
NOTE: Public multi-tenant, cloud based applications are subject to change, possibly without warning, and usually beyond the control of the subscribing organization. Since form fill SSO methods can be adversely affected by such changes, we recommended that federated authentication is used in preference, where available. |

