vWorkspace integration
You can configure Cloud Access Manager to connect to a vWorkspace server and retrieve a list of allowed resources, which can then be displayed on the Cloud Access Manager application portal.
How Cloud Access Manager Works
This section provides detailed information on how Cloud Access Manager works and describes:
Topics:
Authentication and identity federation
Form-fill single sign-on without a proxy
Application coverage and support
Single sign-on
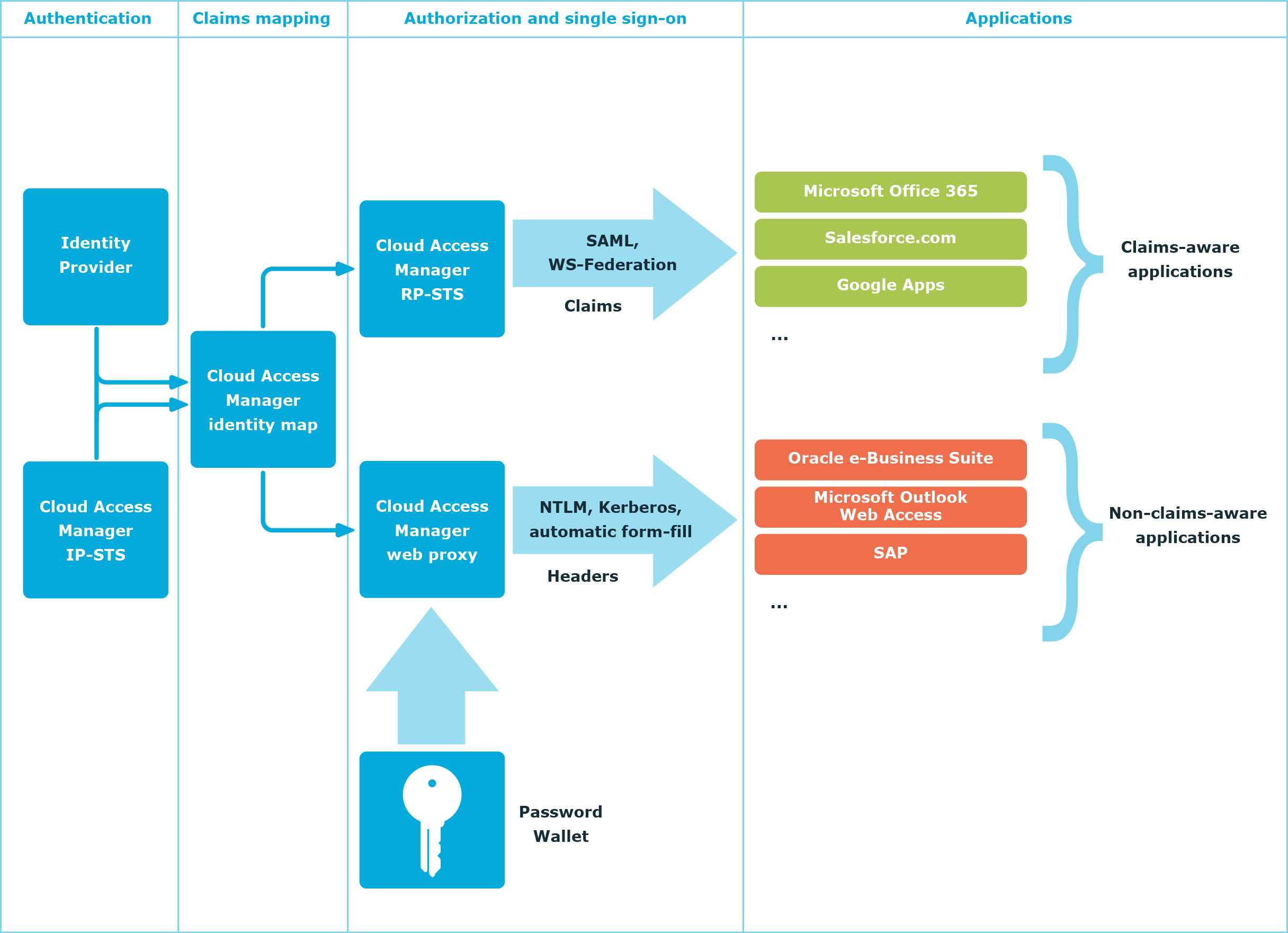
Cloud Access Manager uses protocol transition to translate credentials supplied to it at login into a form. The form can be consumed by applications the user accesses through Cloud Access Manager.
When a user enters their username and password at login this information can be used to:
- Create a Kerberos ticket on-the-fly using delegation protocols to automate login to a web site supporting Windows Integrated Authentication.
- Generate a SAML assertion or WS-Federation security token — signed using Cloud Access Manager’s identity provider certificate — to support Single Sign-On (SSO) to a claims-aware application.
- Key into the user’s Password Wallet containing the usernames and passwords that Cloud Access Manager has remembered for that user, which in turn can be used to automate login to applications that support forms based, NTLM digest, or HTTP basic authentication.
- Generate an HTTP header containing the subject information, and forward it to the firewalled application. The application is modified to recognize and trust the header as an authentication token.
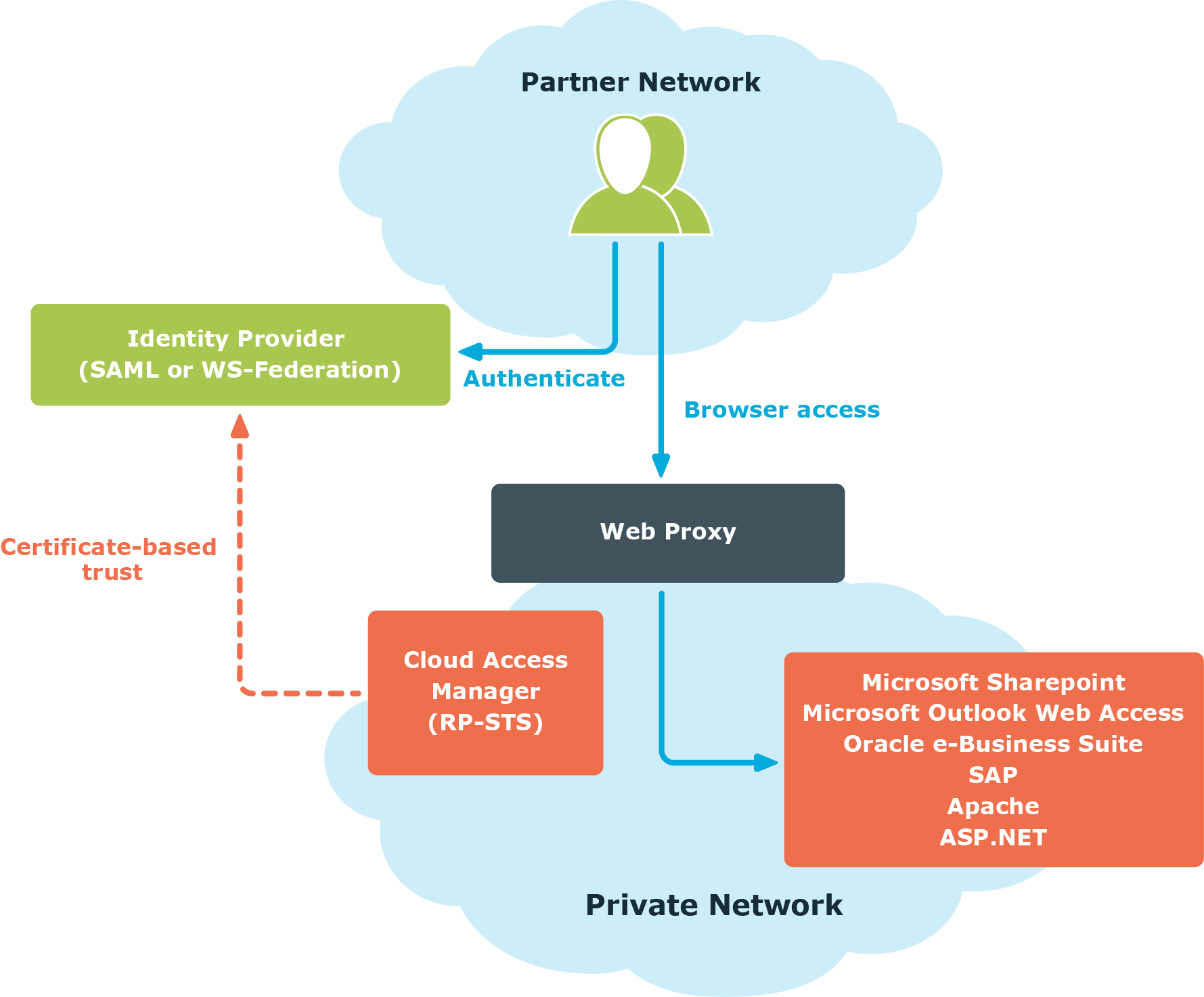
Authentication and identity federation
Cloud Access Manager allows you to set up front-end authentication to use any Lightweight Directory Access Protocol (LDAP) compliant user directory using its built-in Security Token Service (STS). If users in other organizations or forests need access to your applications, this can be achieved through identity federation. To do this, an identity provider must be installed on the remote network. If the identity provider is SAML or WS-Federation compliant, Cloud Access Manager can use it to authenticate the user.
You can configure Cloud Access Manager to extract claims from the security token sent by the identity provider. This information can make authorization decisions within Cloud Access Manager and can also be forwarded to the user's applications.