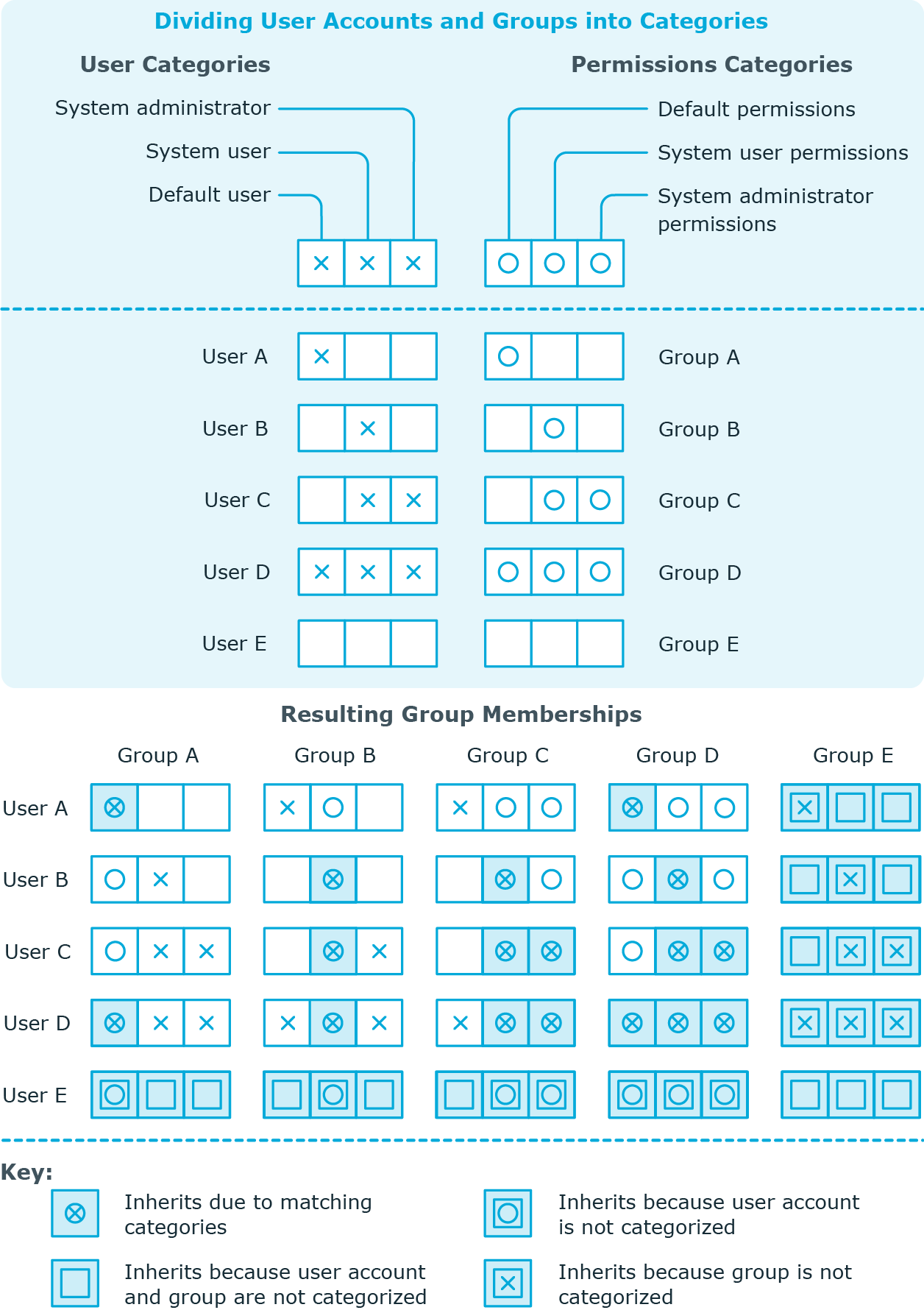
Group inheritance based on categories
In One Identity Manager, groups can be selectively inherited by user accounts. For this purpose, the groups and the user accounts are divided into categories. The categories can be freely selected and are specified using a mapping rule. Each category is given a specific position within the template. The template contains two tables; the user account table and the group table. Use the user account table to specify categories for target system dependent user accounts. In the group table enter your categories for the target system-dependent groups. Each table contains the Position 1 to Position 31 category positions.
Every user account can be assigned to one or more categories. Each group can also be assigned to one or more categories. The group is inherited by the user account when at least one user account category items matches an assigned group. The group is also inherited by the user account if the group or the user account is not put into categories.
NOTE: Inheritance through categories is only taken into account when groups are assigned indirectly through hierarchical roles. Categories are not taken into account when groups are directly assigned to user accounts.
Table 42: Category examples
| 1 |
Default user |
Default permissions |
| 2 |
System users |
System user permissions |
| 3 |
System administrator |
System administrator permissions |
Figure 2: Example of inheriting through categories.
To use inheritance through categories
- Define categories in the cloud target system.
- Assign categories to user accounts through their master data.
- Assign categories to groups through their master data.
Related topics
Assigning permissions controls
Use this task to assign permissions controls to groups.
To assign permissions controls to a group
- Select the Cloud Target Systems | <target system> | Groups category.
- Select the group in the result list.
- Select the Assign permissions controls task.
- In the Add assignments pane, double-click on the permission controls you want to assign.
- OR -
In the Remove assignments pane, double-click on the permissions controls you want remove.
- Save the changes.
Related topics
Assigning extended properties
Extended properties are meta objects, such as operating codes, cost codes, or cost accounting areas that cannot be mapped directly in One Identity Manager.
To specify extended properties for a group
- Select the Cloud Target Systems | <target system> | Groups category.
- Select the group in the result list.
- Select the Assign extended properties task.
- In the Add assignments pane, assign extended properties.
- OR -
In the Remove assignments pane, remove extended properties.
- Save the changes.
For more detailed information about setting up extended properties, see the One Identity Manager Identity Management Base Module Administration Guide.
Deleting groups
To delete a group
- Select the Cloud Target Systems | <target system> | Groups category.
- Select the group in the result list.
- Click
 to delete the group.
to delete the group.
- Confirm the security prompt with Yes.
This deletes the group completely from the One Identity Manager database. Once you have deleted a group, it is also deleted in the Universal Cloud Interface Module through the provisioning process and then in the cloud application. The deletion is logged as a pending change. You can see whether the group has been deleted in the cloud application from the process status for the pending change. The same applies if memberships of user accounts in groups are deleted.
Related topics


 to delete the group.
to delete the group.