Upon creation or renaming of a home folder for a particular user account, this option ensures that the user account is set as the owner of the home folder.
An owner of a folder is authorized to make any changes to permission settings on the folder. For example, an owner can authorize other persons to access the folder.
Upon creation or renaming of a home folder for a particular user account, this option ensures that the user account has the specified access rights on the home folder.
With the Grant Full Access setting, the user account is authorized to perform any operation on the folder and its contents except for making changes to permission settings. With the Grant Change Access setting, the user account is authorized to view and modify the contents of the folder.
When finished, click Next to display the Home Share Management page. This page lets you configure policy options for creating home shares.
Figure 50: Home share management
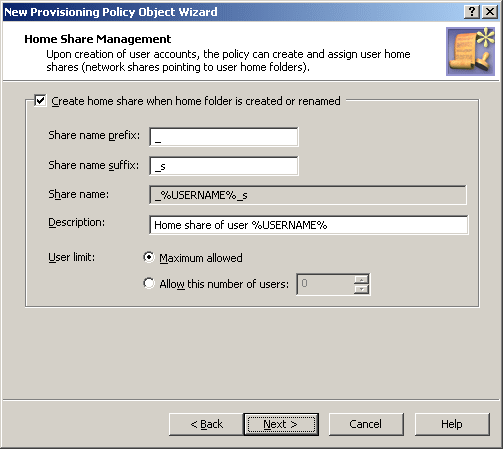
To have the policy create home shares, select the Create home share when home folder is created or renamed check box.
When you configure the policy to create home shares, you can specify the prefix and suffix for the home share names.
Specifying a prefix and suffix allows you to establish a naming convention for home shares. Suppose you want home shares to be displayed at the top of the list of shares. To do so, you can use an underscore as the prefix.
You may also assign a suffix to distinguish home shares created by the policy. For example, to distinguish the home shares of users from the Sales department, you could use the suffix _s. Then, when you create a user account with the pre-Windows 2000 logon name set to JohnB, the policy will map the user’s home folder to the selected drive and specify \\Server\_JohnB_s as the path to the home folder. The policy will also create the share _JohnB_s that points to the folder \\Server\Home\JohnB.
Optionally, in the Description box, you can type a comment about the home share. The users will see it when viewing share properties.
You can also limit the number of users that can connect to the share at one time. Click Maximum allowed or Allow this number of users. With the latter option, specify a number in the box next to the option.
If you want to configure Active Roles so that setting or changing home folder related properties on any user account in any managed domain does not result in an attempt to create or rename a folder on a file server, then you can use the Active Roles Console to modify the built-in Policy Object:
-
In the Console tree, select Configuration > Policies > Administration > Builtin.
-
In the Details pane, double-click Built-in Policy - Default Rules to Provision Home Folders.
-
On the Policies tab, select the policy from the list and then click View/Edit.
-
On the Home Folder tab, clear the Create or rename home folder on file server as needed check box.
-
Click OK to close the dialogs you opened.
If you have any other Policy Objects containing policies of the Home Folder AutoProvisioning category, then you need to configure them as appropriate: Select or clear the Create or rename home folder on file server as needed check box in each of those policies depending on whether or not Active Roles should attempt creation or renaming of home folders for user accounts that fall within the scope of the respective Policy Object.
Another scenario may require Active Roles to create or rename home folders for user accounts that are outside a certain scope (such as a certain domain, Organizational Unit, or Managed Unit), whereas creation or renaming of home folders should not be attempted on user accounts that fall within that particular scope. In this scenario, ensure that the Create or rename home folder on file server as needed option is selected in the built-in Policy Object. Then, create and configure a Policy Object containing a policy of the Home Folder AutoProvisioning category with the Create or rename home folder on file server as needed option cleared, and apply that Policy Object to the scope in question.
When creating home folders, Active Roles operates in the security context of the service account under which the Administration Service is running, so the service account must have sufficient rights to create home folders. Normally, the service account has administrative rights on an entire file server, which enables Active Roles to create home folders in any folder on any network file share that exists on that server. The Home Folder Location Restriction is used to restrict to a certain list the network file shares and folders in which Active Roles is authorized to create home folders.
The Home Folder Location Restriction policy determines the folders on the network file shares in which Active Roles is allowed to create home folders, and prevents Active Roles from creating home folders in other locations. The restrictions imposed by this policy do not apply if the home folder creation operation is performed by an Active Roles Admin role holder (normally, these are the users that have membership in the Administrators local group on the computer running the Active Roles Administration Service). Thus, when an Active Roles Admin role holder creates a user account, and a certain policy is in effect to facilitate home folder provisioning, the home folder is created regardless of the Home Folder Location Restriction policy settings.
By default, no network file shares and folders are listed in the policy. This means that Active Roles cannot create a home folder unless the user management operation that involves creation of the home folder is performed by the Active Roles Admin role holder. In order to allow delegated administrators to create home folders, you have to configure the policy so that it lists the folders on the network file shares in which creation of home folders is allowed. You can do this by using the Active Roles Console as follows.
To configure the Home Folder Location Restriction policy
-
In the Console tree, expand Configuration > Policies > Administration, and select Builtin under Administration.
-
In the Details pane, double-click Built-in Policy - Home Folder Location Restriction.
-
On the Policies tab, double-click the list item under Policy Description.
-
On the Allowed Locations tab, view or modify the list of folders on the network file shares where creation of home folders is allowed.
When adding a folder to the list, specify the UNC name of the folder. If you specify the name in the form \\<Server>\<Share>, home folders can be created in any folder on the network file share specified. If you specify the name in the form \\<Server>\<Share>\<PathtoFolder>, home folders can be created in any sub-folder of the folder.

