|
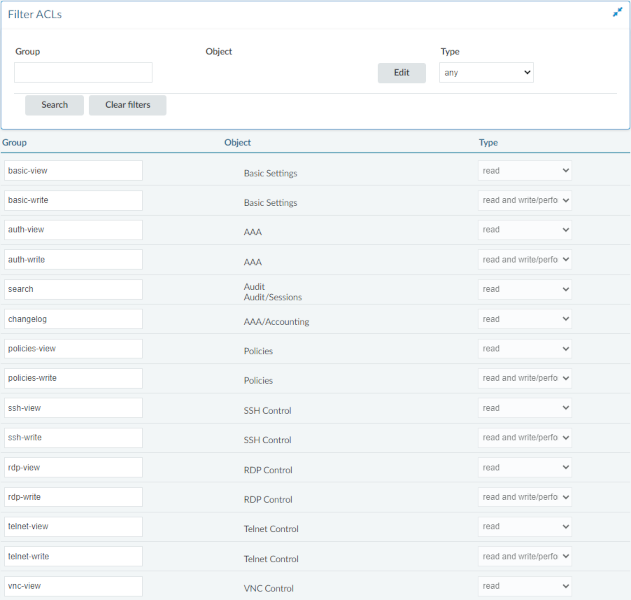
All |
Every menu point |
Gives access to every setting. |
|
System Debug |
Basic Settings > Troubleshooting > Create support bundle |
Enables support bundle generation. |
|
Policy Administrator |
Traffic Control > Quick Connection Setup |
Enables configuring SSH connections and their connection-related policies. |
|
Traffic Control > SSH |
|
Policies > Analytics policies |
|
Policies > Audit policies |
|
Policies > Content policies |
|
Policies > Local User Databases |
|
Policies > Time policies |
|
Policies > User Lists |
|
Policies > Usermapping policies |
|
Import configuration |
Basic Settings > System > Import configuration |
Enables configuration import. |
|
Export configuration |
Basic Settings > System > Export configuration |
Enables configuration export. |
|
Firmware |
Basic Settings > System > Firmwares |
Enables uploading, installing and deleting firmwares on SPS. |
|
Use static subchapters ACLs |
Does not affect menu points. |
Restricts users to add only specific subchapter types to reports. |
|
REST server / REST configuration |
Traffic Controls > Quick Connection Setup |
Enables configuring connections via the Connection Setup Wizard and the REST API. |
|
REST Server / REST |
Users & Access Control > Audit Data Access |
Enables configuring audit data access rules (ADARs) for user groups. |
|
Active sessions |
Pending Connections > Active connections |
Gives access to view and terminate all active sessions monitored by SPS. |
|
Basic Settings / Network |
Basic Settings > Network |
Enables configuring network-related settings. |
|
Basic Settings / Local services |
Basic Settings > Local services |
Enables configuring various services of SPS. |
|
Basic Settings / Management |
Basic Settings > Management |
Gives access to configuring system-level settings. |
|
Basic Settings > Cluster Management |
Enables configuring multiple SPS appliances joining into cluster for scalability, easier monitoring and auditing. Additionally, it enables joining SPS to One Identity Safeguard for Privileged Passwords (SPP). |
|
Basic Settings > Trust stores |
Enables configuring local certificate storage for storing trusted certificates that validate TLS connections. Additionally, it authorizes the user to manage cryptography settings. |
|
Basic settings / Alerting Monitoring |
Basic Settings > Alerting and monitoring |
Gives access to alerting and monitoring configuration. |
|
Basic settings / Date and time |
Basic Settings > Date & Time |
Gives access to date and time configuration. |
|
Basic settings / Dashboard |
Basic Settings > Dashboard |
Gives access to various statistics and status history of system data and performance on the dashboard. |
|
Basic settings / System |
Basic Settings > System |
Gives access to system-related configuration. |
|
Basic settings / Troubleshooting |
Basic settings > Troubleshooting |
Gives access to tools that help troubleshooting network issues, viewing log files and generating support bundles. |
|
Basic settings / Plugins |
Basic settings > Plugins |
Gives access to plugin management. |
|
Basic settings / High availability |
Basic settings > High availability |
Gives access to high availability setup. |
|
Basic settings / Cluster management |
Basic settings > Cluster management |
Gives access to cluster management. |
|
Basic settings / Join to Starling |
Basic settings > Starling integration |
Gives access to the Starling Integration configuration and status page. |
|
Audit / Sessions |
Audit > Sessions |
Enables querying sessions. However, without an audit data access rule (ADAR), no session data is visible. Gives access to the Audit > Sessions page. |
|
Audit / Access all sessions |
Does not affect menu points. |
Authorizes to search and view all sessions, but does not give access to the Audit > Sessions page. In other words, it works like an unfiltered ADAR. |
|
Audit / Access all users |
Audit > Users |
Enables viewing data about audited users. However, it does not give access to view user-related session data. To view user-related session data, you either need the combination of Audit / Sessions ACL with ADAR, or the combination of the Audit / Sessions ACL and the Audit / Access all sessions ACL. |
|
Users & Access Control / Settings |
Users & Access Control > Settings |
Enables configuring the login settings of SPS. |
|
Users & Access Control / Local Users and Groups |
Users & Access Control > Local Users and Groups |
Enables configuring local users and local user groups for accessing SPS. |
|
Users & Access Control / Access Control |
Users & Access Control > Appliance Access |
Enables configuring access control for user groups. |
|
Users & Access Control / Accounting |
Users & Access Control > Configuration History |
Enables access to view the configuration history of SPS. |
|
Users & Access Control / Permission Query |
Users & Access Control > Access Rights Report |
Enables viewing access rights reports. |
|
Policies / AA Plugin Configurations |
Policies > AA Plugin Configurations |
Enables configuring authentication and authorization plugins to authenticate to target hosts. |
|
Policies / Analytics Policies |
Policies > Analytics Policies |
Enables configuring analytics policies that specify algorithms to analyze monitored user behavior and build user baselines. |
|
Policies / Audit Policies |
Policies > Audit Policies |
Enables configuring audit policies specifying encryption, signature and timestamping of the recorded audit trail files. |
|
Policies / Backup & Archive |
Policies > Backup & Archive |
Enables configuring policies to backup and archive audit data. |
|
Policies / Audit Data Cleanup Policies |
Policies > Audit Data Cleanup Policies |
Enables configuring policies to cleanup audit data. |
|
Policies / Content Policies |
Policies > Content Policies |
Enables configuring policies to take action when a predefined content appears in a session. |
|
Policies / Credential Stores |
Policies > Credential Stores |
Enables configuring user credential stores that store credentials for authenticating to target servers. |
|
Policies / Indexer Policies |
Policies > Indexer Policies |
Enables configuring policies specifying what data to capture and index from sessions. |
|
Policies / LDAP Servers |
Policies > LDAP Servers |
Enables configuring LDAP servers to query users and user groups for authentication purposes. |
|
Policies / Local User Databases |
Policies > Local User Databases |
Enables configuring databases storing user credentials for authenticating clients on SPS in gateway authentication scenarios. |
|
Policies / Signing CAs |
Policies > Signing CAs |
Enables configuring certificate authorities (CAs) for signing certificates. |
|
Policies / Time Policies |
Policies > Time Policies |
Enables configuring time intervals to use in other policy settings. |
|
Policies / Trusted CA Lists |
Policies > Trusted CA Lists |
Enables configuring trusted certificate authorities for validating certificates. |
|
Policies / User Lists |
Policies > User Lists |
Enables configuring user lists specifying user access for sessions. |
|
Policies / Usermapping Policies |
Policies > Usermapping Policies |
Enables configuring policies specifying who can use a specific user name to access the remote server. |
|
Indexer |
Indexer Status |
Enables viewing information related to session indexing. |
|
HTTP Control ACLs |
Menu points under Traffic Controls > HTTP. |
Enables configuring HTTP connections. |
|
ICA Control ACLs |
Menu points under Traffic Controls > ICA. |
Enables configuring ICA connections. |
|
MSSQL Control ACLs |
Menu points under Traffic Controls > MSSQL. |
Enables configuring MSSQL connections. |
|
RDP Control ACLs |
Menu points under Traffic Controls > RDP. |
Enables configuring RDP connections. |
|
SSH Control ACLs |
Menu points under Traffic Controls > SSH. |
Enables configuring SSH connections. |
|
Sudo iolog Control |
Traffic Controls > Sudo iolog |
Enables configuring Sudo iolog connections. |
|
Telnet Control ACLs ACLs |
Menu points under Traffic Controls > Telnet. |
Enables configuring Telnet connections. |
|
VNC Control ACLs |
Menu points under Traffic Controls > VNC. |
Enables configuring VNC connections. |
|
Reporting ACLs |
Menu points under Reporting. |
Enables configuring, generating and downloading reports via SPS. |
|
Unlock Credential Store |
User menu > Unlock Credential store |
Enables accessing user credential stores that store credentials for authenticating to target servers. |