This section describes the configuration format and options of the HTTP indexer (that is, how and which fields of the HTTP audit trails are indexed). For details on how to customize HTTP indexing, see Customizing the indexing of HTTP traffic.
NOTE: If you want to index HTTP POST messages, include the "application/x-www-form-urlencoded" Content-Type in the General > WhiteList list. The indexer will decode URL encoding (percentage encoding), and create key=value pairs from the form fields and their values. Note that in the values, the indexer will replace whitespace with the underscore (_) character. To avoid indexing sensitive information (for example, passwords from login forms), use the Form > Blacklist option.
General
Type: Top level item
Description: Determines which HTTP Content-Types are indexed. An HTTP message is indexed only if its Content-Type is listed in Whitelist and is not listed in Blacklist.
For example:
"General": {
"Whitelist": ["text/.*", ".*json.*", "multipart/.*", "application/x-www-form-urlencoded"],
"Blacklist": ["text/css", "application/javascript", "text/xslt", ".*xml.*"]
},
General (Whitelist)
Type: list
Description: The list of HTTP Content-Types to index. Every entry of the list is treated as a regular expression.
For example:
"Whitelist": ["text/.*", ".*json.*", "multipart/.*", "application/x-www-form-urlencoded"],
General (Blacklist)
Type: list
Description: The list of HTTP Content-Types that are not indexed. Every entry of the list is treated as a regular expression.
For example:
"Blacklist": ["text/css", "application/javascript", "text/xslt", ".*xml.*"]
Form
Type: Top level item
Description: Determines which fields are indexed in HTTP POST messages.
For example:
"Form": {
"Blacklist": ["password", "pass"]
},
NOTE: If you want to index HTTP POST messages, include the "application/x-www-form-urlencoded" Content-Type in the General > WhiteList list. The indexer will decode URL encoding (percentage encoding), and create key=value pairs from the form fields and their values. Note that in the values, the indexer will replace whitespace with the underscore (_) character. To avoid indexing sensitive information (for example, passwords from login forms), use the Form > Blacklist option.
Form (Blacklist)
Type: list
Description: The list of fields that are not indexed in HTTP POST messages (for example, when submitting forms, such as login forms). Every entry of the list is treated as a regular expression.
For example:
"Blacklist": ["password", "pass"]
Html
Type: Top level item
Description: Include this section in the configuration to process text/html messages. HTML tags are stripped from the text, and only their content is indexed (for example, <html><title>Title</title></html> becomes Title).
For example:
"Html": {
"Attributes": ["href", "name", "value", "title", "id", "src"],
"StrippedTags": ["script", "object", "style", "noscript", "embed", "video", "audio", "canvas", "svg"]
}
Html (Attributes)
Type: list
Description: The list of HTML attributes that extracted as key=value pairs and indexed. Note that in the values, the indexer will replace whitespace with the underscore (_) character, and decode URL encoding. For example:
"Attributes": ["href", "name", "value", "title", "id", "src"],
Note that for the content attribute of the meta name="description", meta name="keywords", meta name="author" and meta name="application-name" is always indexed.
For example, if an audit trail contains the following HTML:
<head>
<meta name="description" content="Web page description">
<meta name="keywords" content="HTML,CSS,XML,JavaScript">
<meta name="author" content="OI SA">
<meta charset="UTF-8">
</head>
Then the index will contain the following text:
description=Web_page_description keywords=HTML,CSS,XML,JavaScript author=OI_SA
Html (StrippedTags)
Type: list
Description: The list of HTML tags that are not indexed.
For example:
"StrippedTags": ["script", "object", "style", "noscript", "embed", "video", "audio", "canvas", "svg"]
This section provides an overview on how to use the Sessions interface. It describes how you can access the Sessions interface, lists the steps to take to search effectively, view the details of a connection, replay the audit trails, or export the search results as a comma-separated text file.
Prerequisites
Users need the Search privilege to access the Sessions interface.
NOTE: Assigning the Search privilege to a user on the Users & Access Control > Appliance Access page, automatically enables the Search in all connections privilege, and grants the user access to every audit trail, even if the user is not a member of the groups listed in the Access Control option of the particular connection policy.
If you want users to access audit trails only for connections for which they are granted permission, see Assigning search privileges.
For information on configuring:
-
To access the Sessions interface, navigate to Sessions.
Sessions are displayed sorted by date. For ongoing sessions, the Search interface is updated in real-time to always show the most up-to-date information.
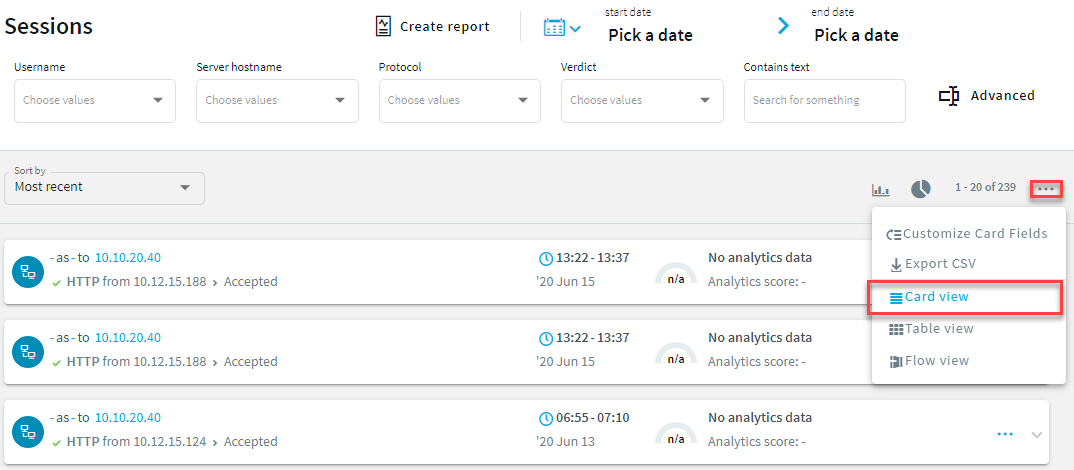
You can view sessions in a card, table or flow view. Click  for more details and select from the list.
for more details and select from the list.
-
Specify a date and time range to restrict your search criteria as described in Specifying time ranges.
-
Filter connections as described in Using search queries.
-
Search the contents of audit trails as described in Searching in the contents of audit trails.
-
View connection details as described in Viewing session details.
-
Download and replay audit trails as described in Replaying audit trails in your browser.
-
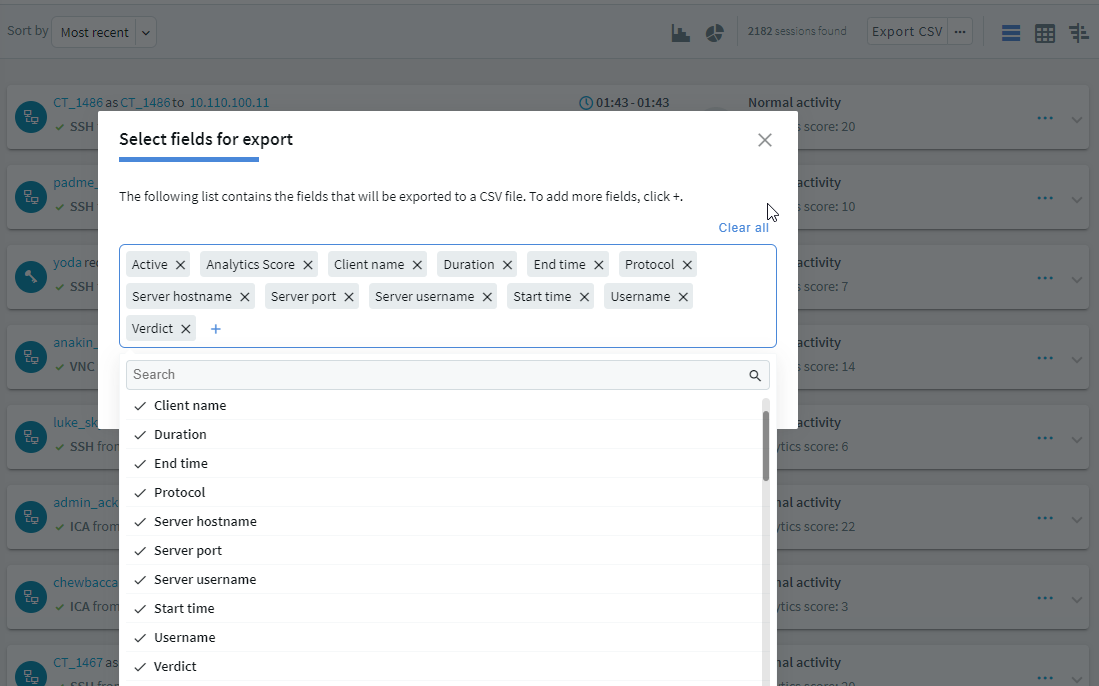
To export the search results as a comma-separated text file, click  for more details and select Export CSV. Note that if your search returns more than 10.000 results, only the first 10.000 rows are exported. If you want to see all results, refine your search.
for more details and select Export CSV. Note that if your search returns more than 10.000 results, only the first 10.000 rows are exported. If you want to see all results, refine your search.
To customize which fields are exported, click  for more details and select Export CSV ....
for more details and select Export CSV ....
You can view sessions in a card, table or flow view. Click  for more details and select from the list.
for more details and select from the list.
In card view, you can add additional search fields to the Search interface. For more information, see Adding custom fields to the card view.
Figure 257: Sessions — Card view

 for more details and select from the list.
for more details and select from the list.
