Management Console for Unix is a JEE (Java Enterprise Edition) web application that simplifies local user and group management on Unix, Linux, and Mac systems using a "mangement console". You access the mangement console through a supported web browser.
Management Console for Unix is deployed on a web server, or more specifically a Java Servlet container running on a Java Virtual Machine (JVM).
Figure 1: Management Console for Unix Architecture
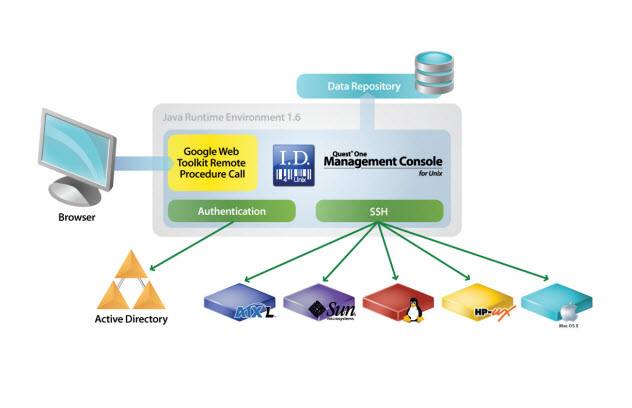
By default, requests are secured by enforcing connections over HTTPS. Communication between the web browser and web server are accomplished through HTTP requests over SSL. Requests from a supported web browser are sent to the web server, which processes the request and returns a response.
The web server fulfills requests by gathering data from one or more locations. These requests are filled from data found in Active Directory, the supplied database, or by collecting data from one or more Unix, Linux, and Mac systems.
The data is stored in a local database on the Management Console for Unix web server. Access to the database is accomplished through JDBC (Java Database Connectivity) technology and is secured by credential authentication (that is, only administrators have access to the Management Console for Unix data directory). Active Directory connections are made through LDAP. These LDAP connections are authenticated with a valid Active Directory user account.
Secure connections to all Unix, Linux, and Mac systems are performed through the SSH protocol. Prior to exchanging SSH credentials, the system’s SSH host key is compared against a known SSH host key. If the key validation is successful an authentication attempt is performed. If the key validation determines that the system SSH host key does not match the known SSH host key, authentication will not be attempted until the known SSH host key matches a system SSH host key.
You can run Management Console for Unix separately in a supported web browser or, you can run the mangement console from within the Authentication Services Control Center. You can install it on Windows, Unix, or Linux. One Identity does not advise managing a Unix host by more than one mangement console in order to avoid redundancy and inconsistencies in stored information. If you manage the same Unix host by more than one mangement console, you should enable auto-profile for that host to minimize inconsistencies that may occur between instances of the mangement consoles.
To remotely manage local users and groups on Unix, Linux, and Mac systems with the mangement console, you must install a Java-based web application that runs on a server which allows you to run a "mangement console" inside a web browser.
The topics in this section explain how to install Management Console for Unix for the first time and how to upgrade it from an older version. It includes the steps for installing and configuring the mangement console on a Windows, Unix, or Linux machine. These instructions assume that you are installing the mangement console from a product ISO.
Prior to installing Management Console for Unix, ensure your system meets the minimum hardware and software requirements for your platform.
NOTE: When setting up a virtual environment, carefully consider the configuration aspects such as CPU, memory availability, I/O subsystem, and network infrastructure to ensure the virtual layer has the necessary resources available. Please consult One Identity's Product Support Policies for more information on environment virtualization.
Table 1: System requirements
| Supported Platforms |
Can be installed on the following configurations:
- Windows x86 (32-bit)
- Windows x86-64 (64-bit)
- Unix/Linux systems for which Java 8 is available
|
| Server Requirements |
The Management Console for Unix server requires Java 8 (also referred to as JRE 8, JDK 8, JRE 1.8, and JDK 1.8). |
| Managed Host Requirements |
Click www.oneidentity.com/products/authentication-services/ to view a list of Unix, Linux, and Mac platforms that support Authentication Services.
Click www.oneidentity.com/products/privilege-manager-for-unix/ to review a list of Unix and Linux platforms that support Privilege Manager for Unix.
Click www.oneidentity.com/products/privilege-manager-for-sudo/ to review a list of Unix, Linux, and Mac platforms that support Privilege Manager for Sudo.
NOTE: To enable the Management Console for Unix server to interact with the host, you must install both an SSH server (that is, sshd) and an SSH client on each managed host. Both OpenSSH 2.5 (and higher) and Tectia SSH 5.0 (and higher) are supported.
NOTE: Management Console for Unix does not support Security-Enhanced Linux (SELinux).
NOTE: When you install Authentication Services on Solaris 10 (SPARC - 32/64-bit), the Solaris 10 packages are installed. |
| Default Memory Requirement: |
1024 MB
|
Management Console for Unix must be able to communicate with Active Directory including domain controllers, global catalogs and DNS servers using Kerberos, LDAP and DNS protocols. The following table summarizes the network ports that must be open and their function.
Table 2: Network ports
| 22 |
TCP |
Default TCP port number used for Secure Shell (SSH) access to Unix hosts being managed by the mangement console. |
| 53 |
TCP and UDP |
Used for DNS. Since Management Console for Unix uses DNS to locate domain controllers, DNS servers used by the Unix hosts must serve Active Directory DNS SRV records. |
| 88 |
TCP and UDP |
Used for Kerberos authentication and Kerberos service ticket requests against Active Directory Domain Controllers. UDP is used by default, but TCP is also used if the Kerberos ticket is too large for UDP transport. |
| 137 |
TCP and UDP |
Used for resolving NetBIOS names, as per RFC1002. UDP is tried first, with fall back to TCP. |
| 389 |
TCP and UDP |
Used for LDAP searches against Active Directory Domain Controllers. TCP is normally used, but UDP is used when detecting the Active Directory site membership. |
| 3268 |
TCP |
Used for LDAP searches against Active Directory global catalogs. TCP is always used when searching against the global catalog. |
| 9001 |
TCP |
Default TCP port used internally on the loopback interface of the Management Console for Unix server for JDBC connections. |
| 9080 |
TCP |
Non-SSL Port number (http:) for the Management Console for Unix Web server; configurable at install time. |
| 9443 |
TCP |
Default Management Console for Unix Web server TCP port used for HTTPS; configurable at install time. |

