Microsoft® Active Directory® LDS
389 Directory Service
Novell® eDirectory™
Windows Azure™ Active Directory® authentication
|
• |
|
3 |
Select the Applications tab. |
|
4 |
Click Add in the bottom toolbar and in the dialog that appears, select Add an application my organization is developing. |
|
5 |
Enter a name for the application, this is simply a description. Ensure that WEB APPLICATION AND/OR WEB API is selected and click the arrow to move to the next page. |
|
6 |
Enter http://CloudAccessManager in both the SIGN-ON URL and APP ID URI fields (these values are not used). Click the tick button to complete the dialog. |
|
7 |
When you have created the application, select the Configure tab and scroll down until you see the CLIENT ID field, you will need to copy and save the value here to use when configuring Cloud Access Manager. |
|
8 |
Scroll down to the permissions to other applications section, click the Application Permissions list and check Read directory data. |
|
9 |
Scroll back up to the keys section, select the required duration for the key and click SAVE. At this point you MUST copy and save the key value as it will not be available again and you need it to configure Cloud Access Manager. |
|
10 |
Click VIEW ENDPOINTS in the bottom toolbar, copy and save the MICROSOFT AZURE AD GRAPH API ENDPOINT and OAUTH 2.0 TOKEN ENDPOINT values. |
|
1 |
Log in to the Administration Console and select Add New from the Front-end Authentication section on the home page. |
|
2 |
|
a |
In the Client ID field, enter the client ID from the Azure portal. |
|
b |
In the Application Key field, enter the key that you created in the Azure portal. |
|
c |
In the Windows Azure AD Graph API Endpoint field, enter the Windows Azure AD Graph API Endpoint from the Azure portal App Endpoints page. |
|
d |
In the OAuth 2.0 Token Endpoint, enter the OAuth 2.0 Token Endpoint from the Azure portal App Endpoints page. |
|
e |
When you have entered the required configuration information, click Test Connection to verify the configuration. Click Next. |
|
3 |
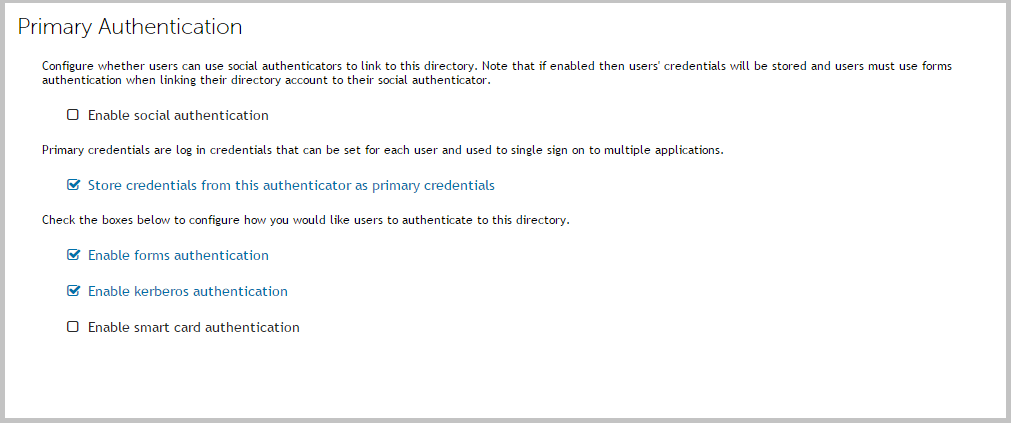
The settings on the Primary Authentication screen are split into three sections. When complete, click Next. |
|
a |
Enable kerberos authentication — Cloud Access Manager will check for a Kerberos ticket generated during Windows domain login and supplied by the browser. If the Kerberos ticket is present and valid, then the user will be successfully logged in. Successful Kerberos authentication requires correct configuration of the user's browser. Please refer to Configuring Cloud Access Manager for Integrated Windows Authentication for details. In addition some browsers do not support Kerberos authentication. Please refer to the Dell™ One Identity Cloud Access Manager Installation Guide for browsers that support Integrated Windows Authentication. |
|
b |
Enable smart card authentication — Users are given the opportunity to present an X.509 certificate in order to log in to Cloud Access Manager. The X.509 certificate may be located on a smart card or in the client computer's certificate store. If the certificate is invalid or expired the login attempt will be rejected. Please refer to the section Configuring smart card authentication for details. |
|
c |
Enable forms authentication — Users are prompted for their Azure Active Directory username and password using a login form. |
|
4 |
If you require two factor authentication each time users authenticate to Cloud Access Manager, select Use two factor authentication for all applications from the Two factor authentication mode list. Select the method of authentication from the Type of two factor authentication list. For information on how to configure the various authentication types or how to configure two factor authentication only for specific users or applications, refer to Configuring step-up authentication. When compete, click Next. |
|
5 |
In the Authenticator Name field, enter the name that will be used to identify the authenticator within Cloud Access Manager, then click Finish. |
|
6 |
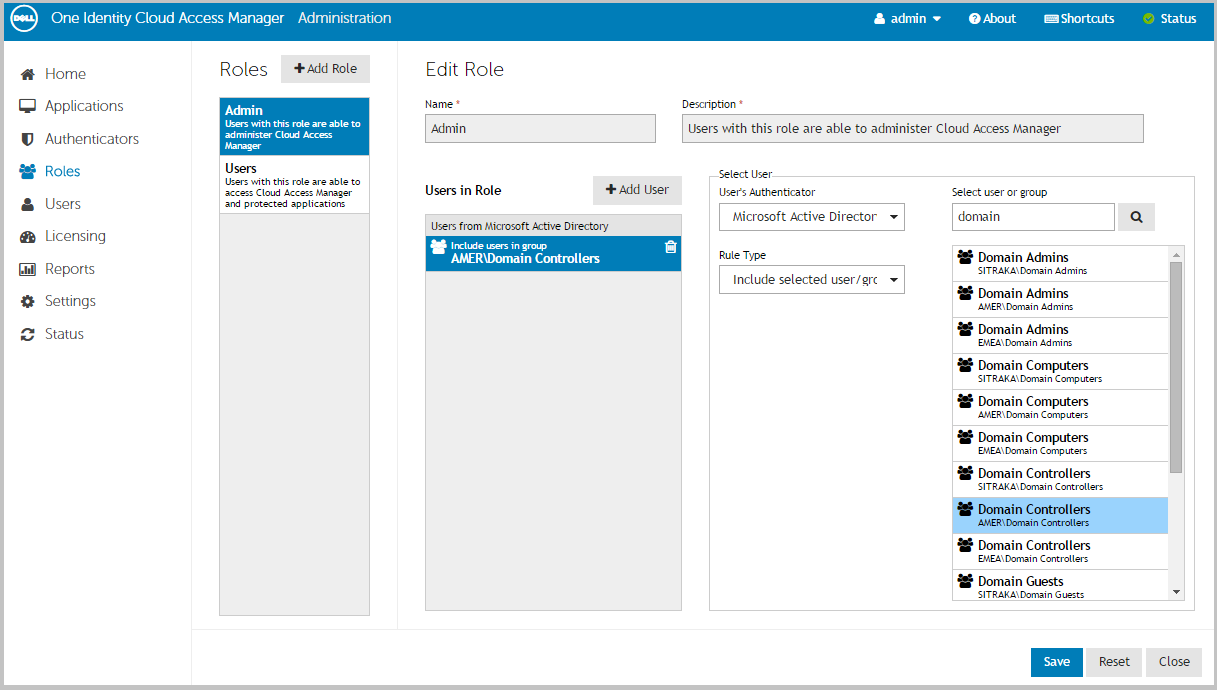
You have now created the front-end authentication method. Click Edit Roles. Before Cloud Access Manager administrators and users can log in to Cloud Access Manager using their Azure Active Directory credentials, you must tell Cloud Access Manager how to identify administrators and users based on their Azure Active Directory group membership. For example, the Domain Admins group for Cloud Access Manager administrators and the Domain Users group for regular Cloud Access Manager users. |
|
7 |
Click Admin. |
|
8 |
|
11 |
Click Save. |
|
13 |
Click +Add User. |
|
16 |
Click Save. |