The operational reports of One Identity Safeguard for Privileged Sessions (SPS) are available in Adobe Portable Document Format (PDF), and contain the following information:
-
Configuration changes: Lists the number of SPS configuration changes per page and per user. The frequency of the configuration changes is also displayed on a chart.
-
Main reports: Contains statistics about the total traffic that passed SPS, including the number of sessions that passed for every connection policy, the used usernames, clients, and servers, and so on.
NOTE: Connections that are still in progress when the report is generated are excluded from the report. Sessions that are being indexed and reporting jobs are listed in the Sessions with in progress indexing or reporting jobs section of the report.
-
Reports by connection: Contains separate statistics about every connection policy configured on SPS.
-
System health information: Displays information about the filesystem and network use of SPS, as well as the average load.
To configure a report, create a chapter and assign any of the existing subchapters to it. The following sources (statistics or other queries) are available as reporting subchapters:
To configure SPS to create custom reports
-
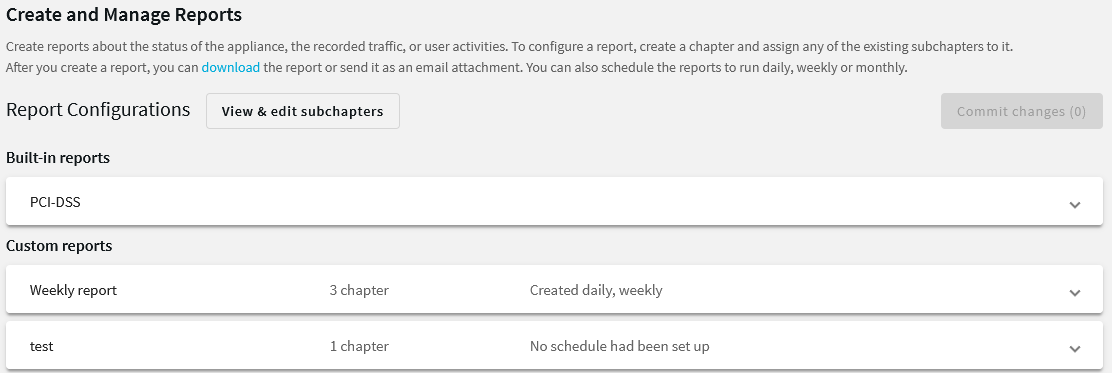
Login to the SPS web interface, and navigate to Reporting > Create & Manage Reports.
Figure 324: Reporting > Create & Manage Reports — Configuring custom reports
-
Click Create new report configuration and enter a name for the custom report.
Figure 325: Reporting > Create & Manage Reports — Configuring custom reports
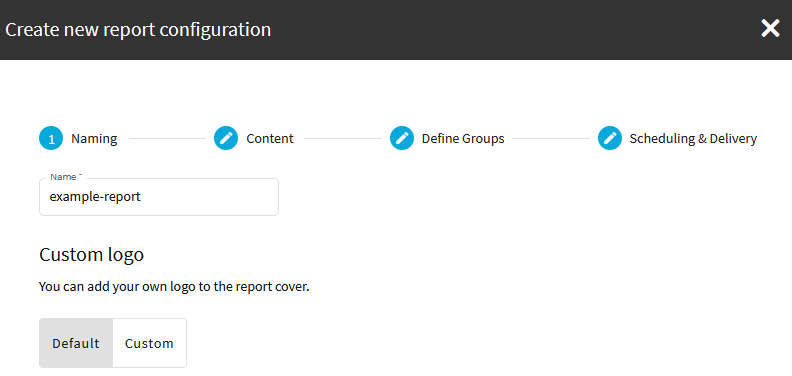
If you want to have the logo of your organization on the cover page of the report (instead of the One Identity logo), select Custom, select your logo file, then click Upload. You can upload GIF, JPEG, and PNG images. SPS will automatically resize the image to fit on the cover page.
-
Select Create new chapter, enter a name for the chapter. Repeat this step to create further chapters if needed.
-
Select Add new subchapter to add various reports and statistics to the chapter. Select any of the existing subchapters or create a new subchapter.
Figure 326: Reporting > Configuration > Add new subchapter — Adding subchapters to reports
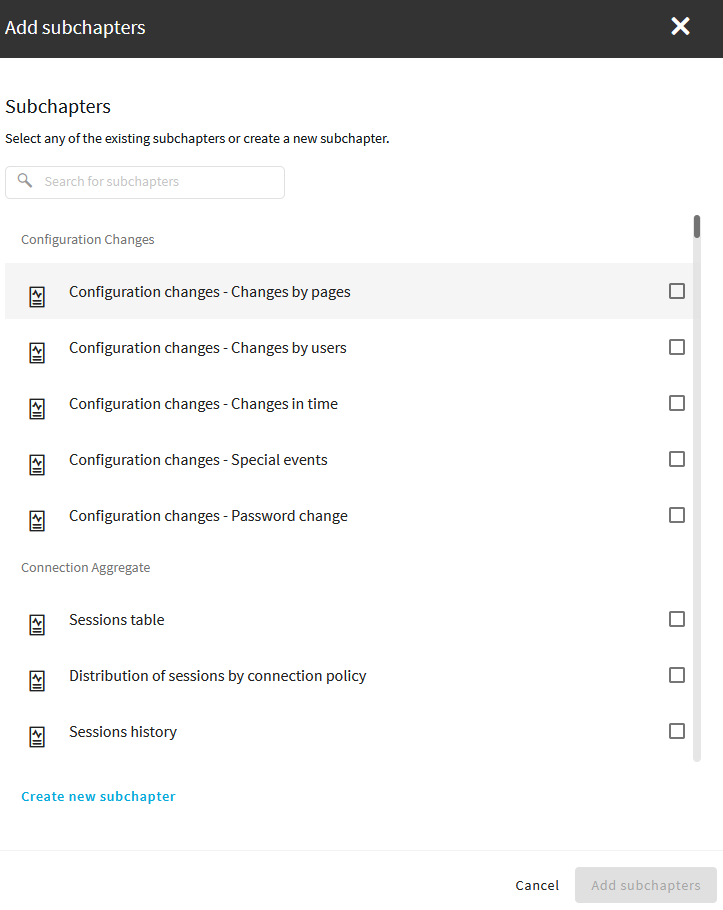
NOTE: When creating a subchapter that searches for keywords in HTTP, only the timestamp of the results will be visible in the report, without data.
-
Once selected, use drag and drop to change the order of the subchapters if needed.
-
By default, members of the report group can access the custom reports through the SPS web interface. To change this, enter the name of a different group into the Groups field.
NOTE: Members of the listed groups can access only these custom reports even if their groups do not have read access to the Reporting > Download reports page. However, only those reports will be listed, to which their group has access to.
-
Select how often SPS creates the report from the Scheduling field. Weekly reports are created on Mondays, while monthly reports on the first day of the month. If you want to create the report only manually, leave these fields empty.
-
By default, SPS sends out the reports in email to the address set in the Basic Settings > Management > Mail settings > Send reports to field.
NOTE: If this address is not set, the report is sent to the SPS administrator's email address.
-
To disable email sending, clear the Deliver in email option.
-
To email the reports to a different address, select Custom, and enter the email address where the reports should be sent. Click Add email to list multiple email addresses if needed.
-
Click Create report.
One Identity Safeguard for Privileged Sessions (SPS) can index the contents of audit trails using its own indexer service or external indexers. Indexing extracts the text from the audit trails and segments it to tokens. A token is a segment of the text that does not contain whitespace: for example words, dates (2009-03-14), MAC or IP addresses, and so on. The indexer returns the extracted tokens to SPS, which builds a comprehensive index from the tokens of the processed audit trails.
Once indexed, the contents of the audit trails can be searched from the web interface. SPS can extract the commands typed and the texts seen by the user in terminal sessions, and text from graphical protocols like RDP, Citrix ICA, and VNC. Window titles are also detected.
SPS has an internal indexer, which runs on the SPS appliance. In addition to the internal indexer, external indexers can run on Linux hosts.
Processing and indexing audit trails requires significant computing resources. If you have to audit lots of connections, or have a large number of custom reports configured, consider using an external indexer to decrease the load on SPS. For sizing recommendations, ask your One Identity partner or contact our Support Team.
SPS also creates statistics of the occurrences of the search keywords, as well as screenshots from the audit trail. These statistics and screenshots can be included in custom reports as subchapters.
NOTE: The screenshots of the sessions containing the search keywords are not included in the report output for security reasons, but you can access the screenshots by using the clickable QR codes.
For more information on accessing the screenshots, see section Report output.
NOTE: Consider the following:
-
The screenshot generated from the search results contains the first occurrence of the search keywords. If your search keywords are visible in the audit trail for a longer period, it is possible that the first occurrence is not the most relevant.
-
For technical reasons, trail data in terminal connections (SSH and Telnet) is aggregated for each second. The screenshot generated for the report reflects the terminal buffer, as it was visible at the end of that second. If data that contains the search keyword was pushed off-screen during this second, the search still finds it, but it will not be visible on the generated screenshot. Similarly, if you search for multiple keywords, it is possible that you will receive results that do not contain every keyword on the same screen (but they were separately visible within the one-second interval).
NOTE: Only audit trails created after the content subchapter has been configured will be processed. It is not possible to create reports from already existing audit trails.
Prerequisites for the indexer service
If you are indexing the audit trails with the indexer service, make sure to enable indexing for the connections you want to include in the report. Otherwise, reporting on audit trail content will not work. For more information, see Configuring the internal indexer.
To configure SPS to create reports from the contents of audit trails
-
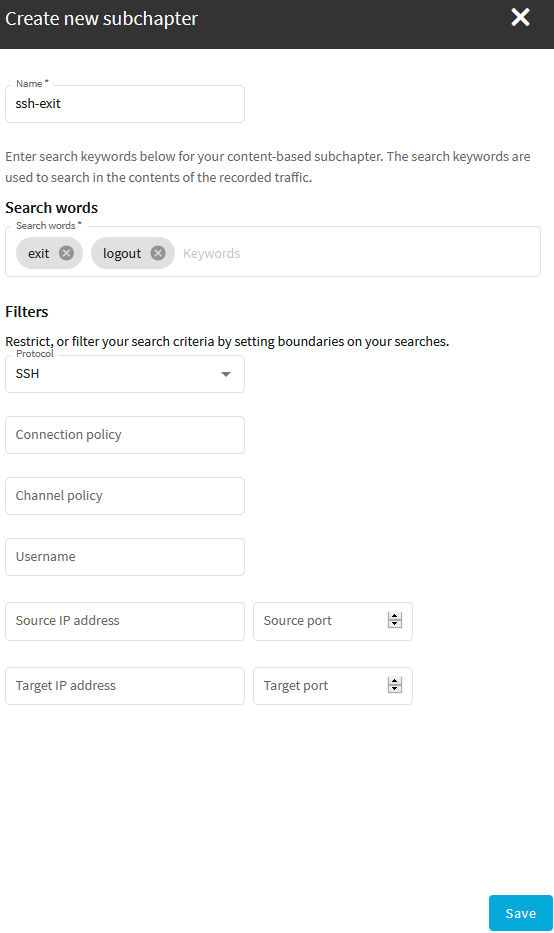
Login to the SPS web interface, and navigate to Reporting > View & edit subchapters > Content-based.
Figure 327: Reporting > View & edit subchapters > Content-based — Configuring audit trail reports
-
Click Create new and enter a name for the subchapter.
-
Enter the search keywords (or parts of the words) into the Search words field. The search keywords are used to search in the contents of the recorded traffic.
Note the following points.
-
Your search expression must be shorter than 255 characters.
-
The search is not case sensitive.
-
Wildcards and regular expressions are not supported.
-
To search for an exact phrase or expression, enclose the keywords in double quotes, for example "program files".
-
Configure filters to select the audit trails to index. The following filters are available:
-
Protocol: Process only audit trails of the specified traffic type (for example SSH).
-
Connection policy: Process only audit trails of the specified connection policy.
-
Channel policy: Process only audit trails of the specified channel policy.
-
Username: Process only audit trails where the specified username was used in the connection. Available only for protocols where the username is known (for example SSH).
-
Source IP address: Process only audit trails where the specified client IP address or port was used.
-
Target IP address: Process only audit trails where the specified server IP address or port was used.
NOTE: If you do not configure any filters, every available audit trail will be processed. Audit trails are created only for channels where the Record audit trail option is enabled for the particular channel in the channel policy.
-
Click Save.
-
Navigate to Reporting > Create & Manage Reports, and add the new subchapter to an existing report, or create a new report. For more information, see Configuring custom reports.
Figure 328: Reporting > Configuration > Add Subchapter — Adding subchapters to reports





