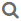Rules page
The Rules page is displayed when the Rules link is clicked in the navigation bar. The Rules page is used for managing the entitlement classification rules that Starling Identity Analytics & Risk Intelligence will use to help you identify high risk accounts.
The following options appear on this page:
New Rule
This opens the New Rule page used to add a rule from the data source. For more information see, Adding a new rule.
Hovering over this icon displays a search box used to locate specific rules within the Rules table. To use the field, start typing the name of the rule in the field and the table will automatically update to display rules that match.
For information on the table appearing at the bottom of the Rules page, see Rules table. For information on the default rules, see Available rules.
Rules table
The Rules table is displayed at the bottom of the Rules page. It displays information on the entitlement classification rules currently configured for Starling Identity Analytics & Risk Intelligence.
The following information and options appear listed in the table:
Name
This is the name of the entitlement rule. If the rule is only applicable to a specific type of data source module, the type of data source module will be indicated before the rule's name (for example, ActiveRoles: Configuration Modify and Safeguard: Admin or Partition Owner).
Description
This is a description of the rule.
Matched Accounts
This displays the number of matched accounts.
Status
This is the current status of the entitlement rule.
Clicking one of the rules (or the 
|
|
IMPORTANT: You are unable to delete a default rule, but default rules can be disabled using the Rule Details page (for more information, see Disabling a rule). |
|
|
IMPORTANT: Adding a new rule will override any existing default rule of that type. The default rule will then be hidden until all customized rules for it are deleted. Once the custom rules are deleted, the default rule (including any previous edits) will reappear on the Rules table. |
Available rules
The following table lists all of the rules that are available on the Rules page and the related permissions that impact an evaluation:
| Rule name | Data source(s) | Permissions |
|---|---|---|
|
Account Best Practices - Computers
|
Active Roles, Active Directory |
For more information, see Account Best Practices rules. |
|
Account Best Practices - Users |
Active Roles, Active Directory, Azure Active Directory |
For more information, see Account Best Practices rules. |
|
ActiveRoles: Configuration Full Control |
Active Roles |
Detected permissions:
|
|
ActiveRoles: Configuration Modify |
Active Roles |
Detected permissions:
Ignored permissions:
|
|
Change Group Type and Scope |
Active Roles |
Detected permissions:
|
|
Active Directory |
Detected permissions:
| |
|
Create Groups |
Active Roles |
Detected permissions:
|
|
Active Directory |
Detected permissions:
| |
|
Create Organizational Units |
Active Roles |
Detected permissions:
|
| Active Directory |
Detected permissions:
| |
|
Create Users |
Active Roles |
Detected permissions:
|
|
Active Directory |
Detected permissions:
| |
|
Delete Groups |
Active Roles |
Detected permissions:
|
|
Active Directory |
Detected permissions:
| |
|
Delete Organizational Units |
Active Roles |
Detected permissions:
|
|
Active Directory |
Detected permissions:
| |
|
Delete Users |
Active Roles |
Detected permissions:
|
|
Active Directory |
Detected permissions:
| |
|
Enable/Disable Users |
Active Roles |
Detected permissions:
|
|
Active Directory |
Detected permissions:
| |
|
Highly Privileged Group Members |
Active Roles, Active Directory, Safeguard, Azure Active Directory |
For more information, see Highly Privileged Group Members rule. |
|
Highly Privileged Role Members |
Azure Active Directory |
For more information, see Highly Privileged Role Members rule. |
|
Modify Group Members |
Active Roles |
Detected permissions:
|
|
Active Directory |
Detected permissions:
| |
|
Reset User Passwords |
Active Roles |
Detected permissions:
|
|
Active Directory |
Detected permissions:
| |
|
Safeguard: Access Request by Local User |
Safeguard |
Detected permissions:
|
|
Safeguard: Access Request via Emergency Access |
Safeguard |
Detected permissions:
|
|
Safeguard: Access Request without 2FA |
Safeguard |
Detected permissions:
|
|
Safeguard: Admin or Partition Owner |
Safeguard |
Detected permissions:
|
|
Safeguard: Session and Password Access Request to Same Account |
Safeguard |
Detected permissions:
|
|
Unlock Users |
Active Roles |
Detected permissions:
|
|
Active Directory |
Detected permissions:
|
Adding a new rule
From the Rules page, you can add new rules for the configured data sources.
|
|
NOTE: Adding a new rule will override any existing default rule of that type. The default rule will then be hidden until the overriding custom rule is deleted. Once the custom rule is deleted, the default rule (including any previous edits) will reappear on the Rules table. |
Adding a new rule
- From the Rules page, click New Rule to open the New Rule page.
-
Use the configuration options to identify and add a new rule. The new rule must have a unique name, a description, and at least one data source must be selected.
NOTE: To edit the name or description of a rule, click the
button to the right of the field. Once you finish editing the rule name or description, you must click the
button to save your edits. This will only save the changes made in that field. To remove any edits made in those fields, use the
button.
NOTE: There are specific configuration options for the Account Best Practices, Highly Privileged Group Members, and Highly Privileged Role Members rules. For more information, see Account Best Practices rulesHighly Privileged Group Members rule and Highly Privileged Role Members rule.
NOTE: Once you have finished configuring the rule, clicking Preview shows what happens if the new rule is applied.
- Click Save to add the rule. The rule will now be available for use.