Creating and using virtual attributes
Active Roles provides the facility to define custom (virtual) attributes for any existing object type. This allows additional object properties to be specified without extending the Active Directory schema. For example, custom attributes can be used to store specific user data.
You can configure a virtual attribute to store the attribute value in the Active Roles database. Otherwise, to use the virtual attribute, you need to implement a script policy to handle the attribute value.
To create a virtual attribute
- In the console tree, expand Configuration | Server Configuration.
- Under Server Configuration, right-click Virtual Attributes and select New | Virtual Attribute.
- Follow the instructions in the Add Virtual Attribute wizard.
- In the Common-Name and the LDAP Display Name boxes, type a common name and an LDAP display name for the new attribute.
In the Unique X.500 object ID box, you can optionally change the default value of the attributeID property (OID) for the new attribute. The default value is generated automatically. If you want to generate your own value, you can use the Oidgen (oidgen.exe) tool, included with the Windows Server Resource Kit.
In the Schema ID GUID box you can optionally change the default value of the schemaIDGUID property. The default value is generated automatically. If you want the new attribute to have the fixed schemaIDGUID property, replace the default value with your own value. For example, you can generate GUID with the Uuidgen tool, included with the Microsoft Platform SDK.
- Optionally, in the Description box, type a description for the new virtual attribute. Click Next.
- In the Syntax list, click the syntax you want for the new virtual attribute. If you want the new attribute to be multi-valued, select the Multi-valued check box. Click Next.
- Select the check boxes next to the object classes with which you want the virtual attribute to be associated. Click Next.
If you need the new attribute to be associated with object classes that are not listed by default, select the Show all possible classes check box.
- If you want to store the values of the attribute in the Active Roles database, select the check box on the Attribute Storage page.
If you choose not to store the attribute values in the database, a script policy is required to supply the attribute value when retrieving the attribute and to save the attribute value when updating the attribute.
However, you should use this option carefully. Storing attribute values in the Active Roles configuration database may considerably increase the database size.
This option can be modified after the attribute is created, by managing properties of the virtual attribute.
- Click Next, and then click Finish to complete the wizard.
After the new virtual attribute has been added, reconnect to the Administration Service. The new virtual attribute appears in the Virtual Attributes container under Configuration/Server Configuration.
To view or modify the value of a virtual attribute on an object
- Right-click the object, and select All Tasks | Advanced Properties.
- Select the Show all possible attributes and the Include attributes with empty values check boxes, for the list in the Advanced Properties dialog box to display all attributes of the object.
- Click the attribute in the list, and then click the button beneath the list.
- In the dialog box that opens, view or modify the value of the attribute.
Scenario: Implementing a Birthday attribute
This scenario illustrates how to create and use a virtual attribute to store information on the birthdays of users.
To create the Birthday attribute
- In the console tree, expand Configuration | Server Configuration.
- Under Server Configuration, right-click Virtual Attributes, and select New | Virtual Attribute.
- Click Next.
- In the Common-Name and LDAP Display Name boxes, type Birthday, as shown in the following figure.
Figure 216: Attribute identification
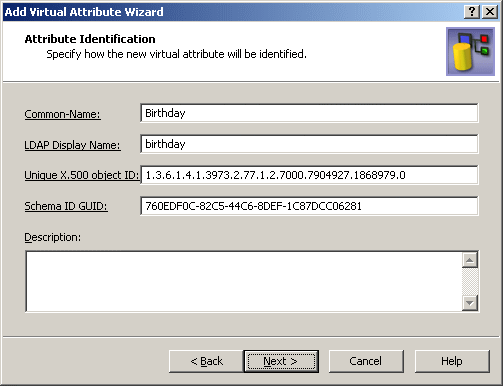
- Click Next.
The Attribute Syntax page should look as shown in the following figure.
Figure 217: Attribute syntax
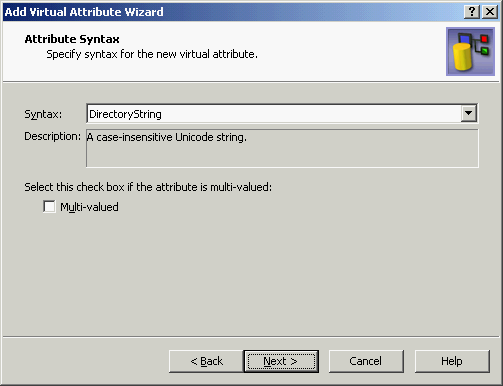
- Click Next.
- On the Object Classes page, select the check box next to User, as shown in the following figure.
Figure 218: Object classes
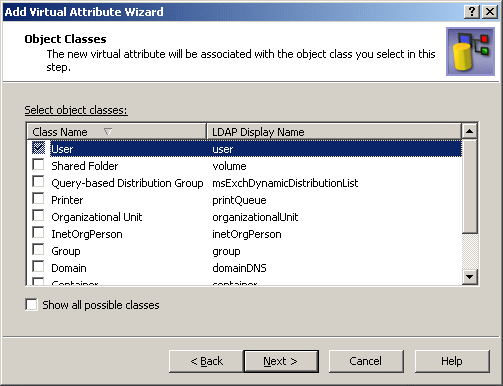
- Click Next.
- On the Attribute Storage window, select the Store values of this virtual attribute in the Active Roles Administration database check box.
- Click Next, and then click Finish to complete the wizard.
To enable the new attribute, reconnect to the Administration Service: right-click the console tree root and click Reconnect.
In the Active Roles console, you can manage the Birthday attribute on a user account as follows:
- Right-click the user account and select All Tasks | Advanced Properties.
- In the Advanced Properties dialog box, select both the Show all possible attributes and Include attributes with empty values check boxes.
- Click Birthday in the list of properties, and then click Edit.
- In the Value box, type a birthday date.
- Click OK.
You can also manage the Birthday attribute via the Active Roles Web Interface.
First, you need to add the Birthday field to a form that displays user properties, and associate that field with the Birthday attribute. You can accomplish this by customizing the form. For instructions on how to add a field to a form, refer to the Active Roles Web Interface Administration Guide.
Then, the Birthday attribute can be managed by accessing user properties in a Web Interface site. For example, users can view and modify this attribute via Site for Self-Administration, provided that you have self-administration implemented (see Scenario 2: Implementing Self-administration in the Role-based Administration chapter earlier in this document).
Examining client sessions
The Active Roles console displays comprehensive information about client sessions. With the console connected to a given Administration Service, you can examine which clients are using that Service. Session information provided by the console includes the following:
- User Logon name of the account used by the session to connect to the Administration Service.
- Active Roles Admin Whether or not the client is logged on as a member of the Active Roles Admin account, and thus has administrator rights on the Administration Service.
- Client Version Client application, such as MMC Interface or Web Interface, and its version.
- Last Access Time Date and time that the Administration Service was last accessed within this session.
- Logon Time Date and time that the session was opened.
- Client Host DNS name of the computer running the client application.
- Client Site Network site of the computer running the client application.
To display a list of client sessions on the Administration Service
- Connect to the Administration Service you want to examine for the client sessions.
- In the console tree, expand Configuration | Server Configuration, and select Client Sessions.
As a result, the details pane lists the client sessions for the Administration Service to which the console is connected.
By using the shortcut menu on a client session, you can also perform the following tasks:
- Send e-mail to the session user.
- Disconnect the session from the Administration Service.
- View additional information about the session.
For example, to view additional information about a session, right-click the session in the details pane and click Properties.
The Properties dialog box for a client session includes the following tabs:
- General Information about the session user, client version, client host, and client site.
- Client Activity Information about logon time, last access time, and the number of operations performed within the session, grouped by operation type.
- Member Of List of all security groups computed due to a transitive group membership expansion operation on the session user at the moment of session start.
- Domain Controllers Information about the domain controllers used to retrieve and update directory data within the session.
Monitoring performance
Active Roles includes a set of performance counters to monitor various aspects of the Administration Service’s performance. Counters are grouped into performance objects that include the following:
- Requests Counts data management requests submitted to the Administration Service.
- LDAP operations Counts LDAP requests issued by the Administration Service.
- Permissions propagation Counts changes to Active Directory security made by the Administration Service.
- External changes Counts data changes polled by the Administration Service from Active Directory, and changes made to the Administration Database.
- Script modules Counts the average execution time of Active Roles script modules, the number of times a particular script module was executed, and number of script module instances being currently executed.
- Miscellaneous Counts the number of clients connected to the Administration Service and the number of queued post-policy processing operations.
To examine Administration Service performance counters, you can use the Performance tool on the computer running the Administration Service:
- Start the Performance tool: click Start and select All Programs | Administrative Tools | Performance.
- In the console tree, select System Monitor.
- Click in the details pane, and then press CTRL+I to display the Add Counters dialog box.
- From the list in the Performance object box, select any name that begins with the prefix AR Server. For example, you might select AR Server:Requests.
- Select an item from the list of counters. For example, you might select Requests/sec.
- Click Add and then click Close.
As a result, the Performance tool displays the output of the counter you have selected.



