You can attach a debugger to the script host of the Administration Service for a given policy script or scheduled task script. When the specified Administration Service runs the script, you can use the debugger for identifying and isolating problems.
To enable script debugging
-
In the Console tree, navigate to Configuration > Script Modules.
-
Right-click the script module that you want to debug, and select Properties.
-
In the Properties window, select the Debugging tab, then select Enable debugging.
-
Depending on type of the script, the following options are available:
-
If you are debugging a PowerShell script, select from the Debug trace level drop-down.
-
If you are debugging any other type of script, select the following:
-
(Optional) To automatically run the debugger when an error occurs, select Enter debugger on error.
-
(Optional) To freeze all operation while the debugger is running, select Break into debugger at the earliest opportunity.
-
In the Debug on server drop-down, select the Active Roles instance where you want the debugger to run.
The policy described in this example scenario prevents administrators from creating a new universal group or converting an existing group to a universal group in Active Roles Console or Active Roles Web Interface.
The script checks the property values submitted to the Administration Service and analyzes the value of the groupType attribute to determine if the universal group scope option was set. If the script detects that the groupType value would set the group as a universal group, it raises a policy violation event in the Administration Service.
As a result, the application that initiated the request, such as the Active Roles Console or Web Interface, displays an error message provided by the script.
As a result, neither the Active Roles Console, nor the Active Roles Web Interface can be used to set the universal group scope option when creating a new group or modifying an existing group.
The script used in this scenario is installed with the Active Roles SDK. By default, the file path and name of the script file is the following:
%ProgramFiles%\One Identity\Active Roles\Active Roles\SDK\Samples\RestrictGroupScope\RestrictGroupScope.ps1
To import the script using Active Roles Console
-
In the Console tree, navigate to Configuration > Script Modules.
-
Select the folder to which you want to add the script module.
TIP: To create a new folder, right-click Script Modules, and select New > Scripts Container.
-
Right-click the folder, and click Import.
TIP: One Identity recommends storing custom script modules in a separate folder.
-
Select the RestrictGroupScope.ps1 file, and click Open.
You can create and apply the Script Execution policy that is described in Example: Restricting the group scope in a Script Execution policywith the New Policy Object Wizard.
To configure the Script Execution policy to restrict the group scope
-
In the Console tree, navigate to Configuration > Policies > Administration.
-
To open the New Policy Object Wizard dialog, choose one of the following:
-
To add a provisioning policy, right-click Administration, then select New > Provisioning Policy.
-
To add a deprovisioning policy, right-click Administration, then select New > Deprovisioning Policy.
-
On the Name and Description page, provide a unique Name for the new Policy Object. Optionally, also provide a Description. To continue, click Next.
-
On the Policy to Configure page, select Script Execution, then click Next.
-
On the Script Module page, click Select a script module, then select RestrictGroupScope from the list of script modules.
Figure 38: Adding the RestrictGroupScope script module for the Policy Object
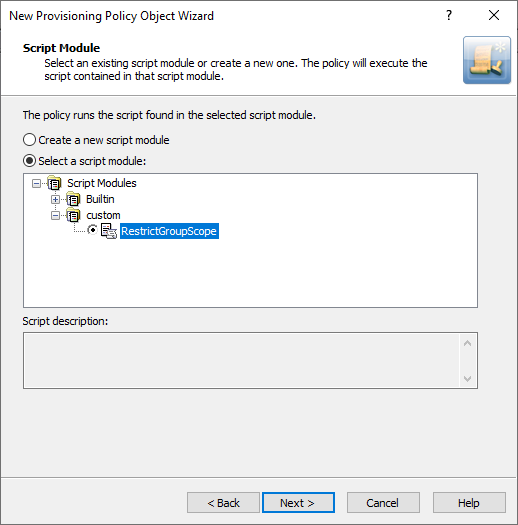
-
(Optional) On the Policy Parameters page, edit the policy parameters:
-
In the Function to declare parameters drop-down, choose the function that defines the parameters for the policy.
The list contains the names of all script functions found in the selected script module.
-
To view and change the values of policy parameters, under Parameter values, select the name of the parameter and click Edit.
-
On the Edit Parameter page, modify the value of the parameter.
NOTE: The selected parameter might have a predefined list of possible values. In such cases, you can only select values from that list.
-
Click Next, then follow the instructions in the wizard to create (and optionally, immediately apply) the Policy Object.
-
To apply the Policy Object:
-
Use the Enforce Policy page in the New Policy Object Wizard.
-
Alternatively, complete the New Policy Object Wizard, then use the Enforce Policy command on the domain, OU, or Managed Unit where you want to apply the policy.
For more information on how to apply a Policy Object, see Linking Policy Objects to directory objects.

