Configuring advanced WS-Federation token settings
In most situations the WS-Federation token produced by Dell™ One Identity Cloud Access Manager, in response to an authentication request is accepted by the service provider. However, if a service provider has special requirements for the way the token is configured, then you can modify the token options on the WS-Fed Token Settings tab for the application.
Any settings changed on this page will only affect the selected application.
|
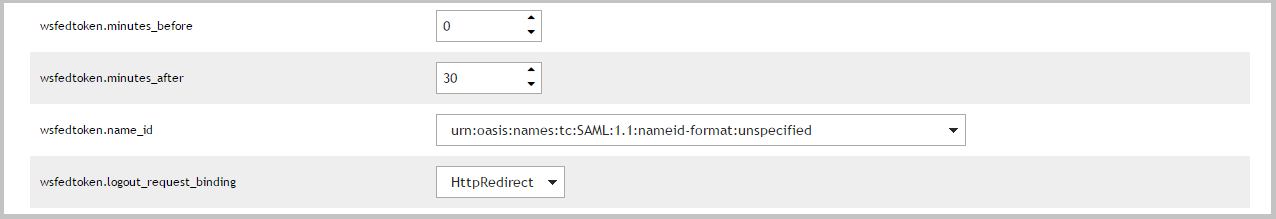
For a description of the available configuration options, please refer to Table 6.
|
The number of minutes before the token IssueInstant to set the NotBefore attribute in the Conditions element. |
||
|
The number of minutes after the token IssueInstant to set the NotOnOrAfter attribute in the Conditions element. |
||
|
The value of the Format attribute of the NameIdentifier element in the Subject. |
||
|
If HttpRedirect is selected then logout requests will be sent to the application. If Disabled is selected then logout requests will not be sent. |
OpenID Connect/OAuth 2.0
For information on how to use Dell™ One Identity Cloud Access Manager as an OAuth v2.0 or OpenID Authorization Server, please refer to the document entitled Dell™ One Identity Cloud Access Manager How To Develop OpenID Connect Apps.
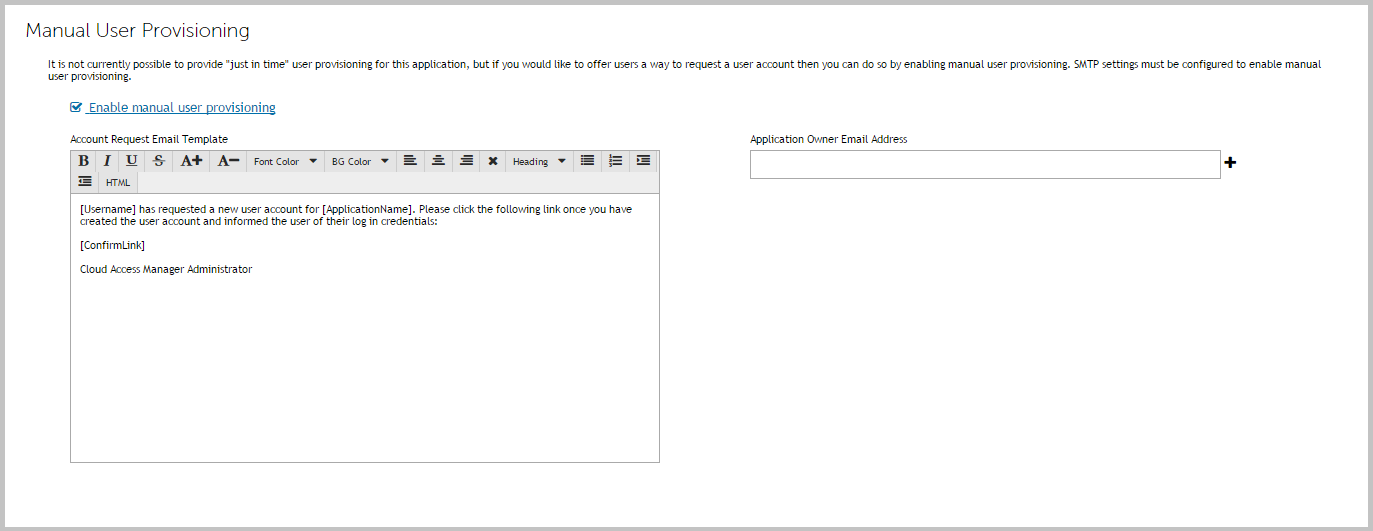
Manual user provisioning
Alternatively, a Cloud Access Manager administrator can view any outstanding manual provisioning requests. To do this, go to Cloud Access Manager Application Portal | Users |Manual Provisioning Requests and confirm that the requests have been dealt with.
HTTP basic authentication
|
1 |
Log in to the Administration Console using the desktop shortcut Cloud Access Manager Application Portal and select Add New from the Applications section on the home page. |
|
2 |
Click Configure Manually. |
|
3 |
|
6 |
You will now see the Permissions page, which enables you to control the users who can access the application. By default all Cloud Access Manager users have access to the application. You can restrict access to the application to users who belong to a specific role, but for this example, simply click Next to allow all users to access the application. |
|
8 |
If the application requires users to log in using their primary credentials, for example their domain account, select Use primary credentials to log into this application and click Next. If the application requires users to use a different username or password, leave the option clear and click Next. |
|
NOTE: Take care to ensure that the URL entered is unaltered, even down to subtle changes such as character case, in the example Active Roles Server the URL must be ARServerAdmin. The Add application to application portal home and Allow user to remove application from application portal options allow you to specify whether the application should appear automatically on each user’s portal page, and how the user can manage the application from the application portal. The options are shown in Table 7. |