Active Roles provides support to connect to Starling Connect to manage the user provisioning and deprovisioning activities for the registered connectors. This is achieved through the internal attribute mapping mechanism. The AD attributes are mapped to SCIM attributes to perform each operation.
Table 57: SCIM attribute mapping with Active Directory for Users
| SCIM |
Active Directory |
|
displayName |
displayName |
|
givenName |
givenName |
|
familyName |
sn |
|
middleName |
middleName |
|
title |
title |
|
password |
edsaPassword |
|
streetAddress |
streetAddress |
|
locality |
city |
|
postalCode |
postalCode |
|
region |
state |
|
country |
c |
|
active |
edsaAccountIsDisabled |
|
userName |
edsvauserName |
|
honorificPrefix |
initials |
|
formattedName |
cn |
|
emails |
proxyAddresses,mail |
|
preferredLanguage |
preferredLanguage |
|
description |
description |
|
emailEncoding |
edsvaemailEncoding |
|
alias |
edsvaalias |
|
division |
division |
|
company |
company |
|
department |
department |
|
homePage |
wWWHomePage |
|
lastLogon |
lastLogon |
|
accountExpires |
accountExpires |
|
timezone |
edsvatimezone |
|
entitlements |
edsvaentitlements |
|
employeeNumber |
employeeNumber |
|
cn |
cn |
|
userPermissionsMarketingUser |
edsvauserPermissionsMarketingUser |
|
userPermissionsOfflineUser |
edsvauserPermissionsOfflineUser |
|
userPermissionsAvantgoUser |
edsvauserPermissionsAvantgoUser |
|
userPermissionsCallCenterAutoLogin |
edsvauserPermissionsCallCenterAutoLogin |
|
userPermissionsMobileUser |
edsvauserPermissionsMobileUser |
|
userPermissionsSFContentUser |
edsvauserPermissionsSFContentUser |
|
userPermissionsKnowledgeUser |
edsvauserPermissionsKnowledgeUser |
|
userPermissionsInteractionUser |
edsvauserPermissionsInteractionUser |
|
userPermissionsSupportUser |
edsvauserPermissionsSupportUser |
|
userPermissionsLiveAgentUser |
edsvauserPermissionsLiveAgentUser |
|
locale |
localeID |
|
phoneNumbers |
telephoneNumber,mobile,homePhone |
|
manager |
manager |
|
desiredDeliveryMediums |
edsvadesiredDeliveryMediums |
|
nickname |
edsvanickname |
Table 58: SCIM attribute mapping with Active Directory for Groups
|
SCIM |
Active Directory |
|
displayName |
cn |
|
members |
member |
|
email |
mail |
|
manager |
managedBy |
Configuring linked mailboxes with Exchange Resource Forest Management
The Exchange Resource Forest Management (ERFM) feature of Active Roles allows you to automate mailbox provisioning for on-premises users in environments where the mailboxes and the user accounts are managed in different Active Directory (AD) forests. Such multi-forest environments are based on the resource forest model, and mailboxes provisioned in such environments are called linked mailboxes.
Multi-forest AD deployments have higher administrative and support costs. However, they offer the highest level of security isolation between AD objects and the Exchange service. As such, One Identity recommends configuring the resource forest model for use with Active Roles in organizations that:
-
Aim for an extra layer of data security.
-
Frequently experience organizational changes (for example, buying companies, or consolidating and breaking off branch companies, departments and other business units).
-
Abide by certain legal or regulatory requirements.
AD deployments following the resource forest model use two types of AD forests:
-
Account forests: These AD forests store the user objects. Organizations can use one or more account forests in the resource forest model.
-
Resource forest: This AD forest contains the Exchange server and stores the mailboxes of the user objects.
For more details on ERFM, see Exchange Resource Forest Management in the Active Roles Feature Guide.
To use linked mailboxes with Exchange Resource Forest Management (ERFM) in Active Roles for your organization, your deployment must meet the following requirements.
Multi-forest deployment
Your organization must have at least two Active Directory (AD) forests:
-
Account forest: One or more forests that contain the user accounts.
-
Resource forest: A forest that contains the Exchange server and will store the mailboxes and the shadow accounts connecting the linked mailboxes to the user objects. ERFM requires a supported version of Exchange Server installed in the resource forest. For more information on the Microsoft Exchange Server versions supported by Active Roles, see System requirements in the Active Roles Release Notes.
For more information on planning and configuring multi-forest AD deployments, see Setting up a forest trust to support linked mailboxes and Plan a multi-forest deployment in the Microsoft documentation.
For more information on the Microsoft Exchange Server versions Active Roles supports, see Supported platforms in the Active Roles Release Notes.
Two-way trust relation
The resource and account forests must identify each other as trusted domains (that is, they must be in a two-way trust relation).
Applying the ERFM - Mailbox Management built-in policy
You must apply the ERFM - Mailbox Management built-in policy (or a copy of it) on the Organizational Unit (OU) whose users will use linked mailboxes. For more information, see Applying the ERFM Mailbox Management policy to an OU.
(Optional) Modifying the ERFM scheduled task
Once the ERFM - Mailbox Management built-in policy is configured for an OU, Active Roles synchronizes the properties of every managed master user account to the corresponding shadow account with the ERFM - Mailbox Management built-in scheduled task.
By default, the scheduled task runs on a daily basis, and normally, you do not need to modify its settings. To change the default ERFM scheduling (for example, because of organizational reasons), or run it manually so that you can immediately identify master accounts in your OU, see Configuring the ERFM Mailbox Management scheduled task.
(Optional) Changing the default location of the shadow accounts
By default, the ERFM - Mailbox Management built-in policy saves shadow accounts in the Users container of the resource forest. If your organization stores other users as well in the Users container, then One Identity recommends changing the container for storing the shadow accounts for clarity.
For more information, see Changing the location of the shadow accounts.
(Optional) Modifying the synchronized properties of the master account
By default, ERFM synchronizes a pre-defined set of user and mailbox properties between the master accounts and shadow accounts. If you need to modify and/or expand the default set of synchronized properties (for example, because of organizational reasons), open and update the applicable ERFM - Mailbox Management policy settings.
For the list of default synchronized properties and more information on changing them, see Configuring the synchronized, back synchronized or substituted properties of linked mailboxes.
(Optional) Delegating Exchange Access Templates
If you want to manage linked mailboxes with non-administrator users, you must assign one or more of the following Exchange Access Templates (ATs) to them in the Active Roles Console:
-
Exchange - Manage Resource, Linked and Shared Mailboxes
-
Exchange - Convert Linked Mailbox to User Mailbox
-
Exchange - Convert User Mailbox to Linked Mailbox
-
Exchange - Create Linked Mailboxes
-
Exchange - Read ERFM Attributes
-
Exchange - Recipients Full Control
TIP: To provide full control for a user to create, view, or change linked mailboxes in the Exchange forest, assign the Exchange - Recipients Full Control AT to them.
For more information on how to apply ATs, see Applying Access Templates.
To provision linked mailboxes in the resource forest model with Exchange Resource Forest Management (ERFM), you must register the resource forest and the account forest(s) of your organization in Active Roles as managed domains.
Prerequisites
To register the forests, you must have access to administrator accounts with sufficient rights in the account forest(s) and the resource forest.
-
To register the account forest(s), you must use the Active Roles Administration Service account.
-
To register the resource forest, you must use a Microsoft Exchange administrator account of the resource forest. Specifically, this Exchange administrator account must have the following rights and permissions:
-
It must be a member of the Account Operators domain security group.
-
It must have read access to Exchange configuration data in the resource forest. For more information on how to configure read access, see Permission to read Exchange configuration data in the Active Roles Installation Guide.
To register the account forest(s) in Active Roles
-
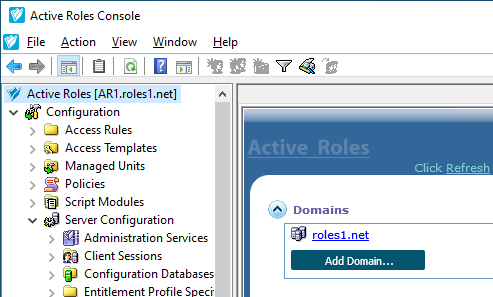
In the Active Roles Console, open the Add Managed Domain Wizard. To do so, open the Active Roles main page by clicking the top Active Roles node, then click Domains > Add Domain.
Figure 119: Active Roles Console – Add Domain setting in the main node
-
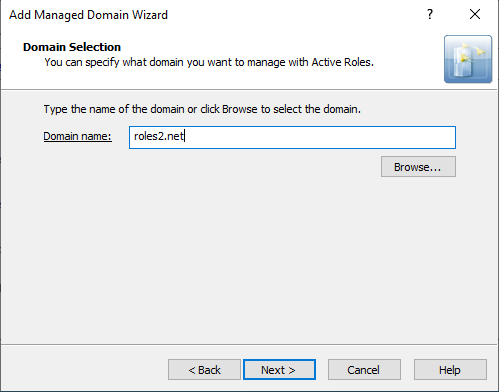
In the Domain Selection step, either enter the domain name of the forest, or click Browse to select it.
Figure 120: Add Managed Domain Wizard > Domain Selection – Specifying an account forest
-
In the Active Roles Credentials step, under Access the domain using, select The service account information the Administration Service uses to log on.
-
To apply your changes, click Finish.
Active Roles then establishes the connection to the configured forest, indicated with the Domain information is being loaded message on the main page. Once Active Roles connected to the domain, the Active Roles Console will indicate it with the Available for management message.
TIP: To check the current domain connection status, use the click to update the display link. The link is replaced with the Available for management feedback once Active Roles finishes connecting to the forest.
To register the resource forest (Exchange forest) in Active Roles
-
In the Active Roles Console, open the Add Managed Domain Wizard. To do so, open the Active Roles main page by clicking the top Active Roles node, then click Domains > Add Domain.
Figure 121: Active Roles Console – Add Domain setting in the main node

-
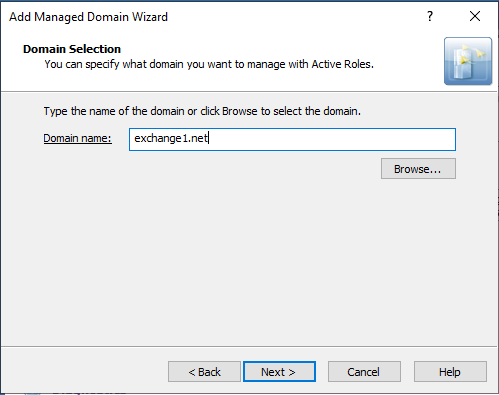
In the Domain Selection step, either enter the domain name of the forest, or click Browse to select it.
Figure 122: Add Managed Domain Wizard > Domain Selection – Specifying the resource forest
-
In the Active Roles Credentials step, under Access the domain using, select The Windows user account information specified below, and provide the User name, Password and User domain of the resource forest administrator account.
NOTE: Make sure that you specify a valid resource forest administrator user in this step, instead of the Active Roles service account used for registering the account forest(s).
Using your Active Roles administrator account in this step can result in Active Roles being unable to create the shadow accounts later in the resource forest.
-
To apply your changes, click Finish.
Active Roles then establishes the connection to the configured forest, indicated with the Domain information is being loaded message on the main page. Once Active Roles connected to the domain, the Active Roles Console will indicate it with the Available for management message.
TIP: To check the current domain connection status, use the click to update the display link. The link is replaced with the Available for management feedback once Active Roles finishes connecting to the forest.



