This section provides introductory information about One Identity Active Roles.
Topics:
Active Roles simplifies creating and managing user accounts and groups in Windows Active Directory (AD) environments by automating the following:
-
User and group account creation in AD and Azure AD
-
Mailbox creation in Exchange and Exchange Online
-
Group population, and resource assignment in Windows.
Active Roles enforces security, automates directory management tasks, and provides change approval and a Web Interface.
To help you deploy Active Roles in your organization, this document provides instructions for preparing the environment and installing Active Roles components.
Active Roles delivers a reliable, policy-based administration and provisioning solution, allowing enterprises to fully benefit from Active Directory and Microsoft Exchange deployment.
One of the most valuable features of the product is the ability to automate provisioning tasks on directory objects in compliance with corporate administrative policies in corporate Active Directory and Exchange environments.
Active Roles provides consistent enforcement of corporate policies, a role-based administrative model, and flexible, rule-based administrative views, creating a reliable and secure environment for distributed administration and account provisioning.
NOTE: For information on the Active Roles features, see the latest Active Roles Release Notes.
Before proceeding with the upgrade ensure to perform a database backup.
Active Roles provides out-of-the-box user and group account management, strictly enforced administrator-based role security, day-to-day identity administration and built-in auditing and reporting for Active Directory and Azure Active Directory (AD) environments. The following features and capabilities make Active Roles a practical solution for secure management of objects in AD and AD-joined systems:
-
Secure access: Acts as a virtual firewall around AD, enabling you to control access through delegation using a least privilege model. Based on defined administrative policies and associated permissions generates and strictly enforces access rules, eliminating the errors and inconsistencies common with native approaches to AD management. Plus, robust and personalized approval procedures establish an IT process and oversight consistent with business requirements, with responsibility chains that complement the automated management of directory data.
-
Automate object creation: Automates a wide variety of tasks, including:
-
Creating user, groups, and contacts in AD and Azure AD.
-
Creating mailboxes on Exchange Server and assigning licenses in Microsoft 365.
-
Managing on-premises Exchange and Exchange Online properties.
Active Roles also automates the process of reassigning and removing user access rights in AD and AD-joined systems (including user and group deprovisioning) to ensure an efficient and secure administrative process over the user and group lifetimes. When user accesses must be changed or removed, updates are made automatically in Active Directory, Azure AD, Exchange, Exchange Online, SharePoint, Skype for Business, and Windows, as well as any AD-joined systems such as Unix, Linux, and Mac OS X.
-
Day-to-day directory management: Simplifies management of:
-
Exchange recipients, including mailbox assignment, creation, movement, deletion, permissions, and distribution list management.
-
Groups
-
IT resources, including computers, shared folders, printers, local users and groups.
-
AD, Azure AD, Exchange Online and AD LDS resources.
Active Roles also includes intuitive interfaces for improving day-to-day administration and help desk operations via an MMC snap-in known as the Active Roles Console and a Web Interface.
-
Manage users, groups, and contacts in a hosted environment: Provides to operate in hosted environments where accounts from client AD domains are synchronized with host domains. Active Roles enables user, group, and contact management from the client domain to the hosted domain, while also synchronizing attributes and passwords.
-
Consolidate management points through integration: Complements your existing technology and identity and access management strategy. Simplifies and consolidates management points by ensuring easy integration with many One Identity products and Quest products, including One Identity Manager, Safeguard Authentication Services, Defender, ChangeAuditor, and GPO Admin. Active Roles also automates and extends the capabilities of PowerShell, ADSI Provider, and the customizable Web Interface.
Active Roles divides the workload of directory administration and provisioning into three functional layers—presentation components, service components, and network data sources.
Figure 1: Active Roles Components
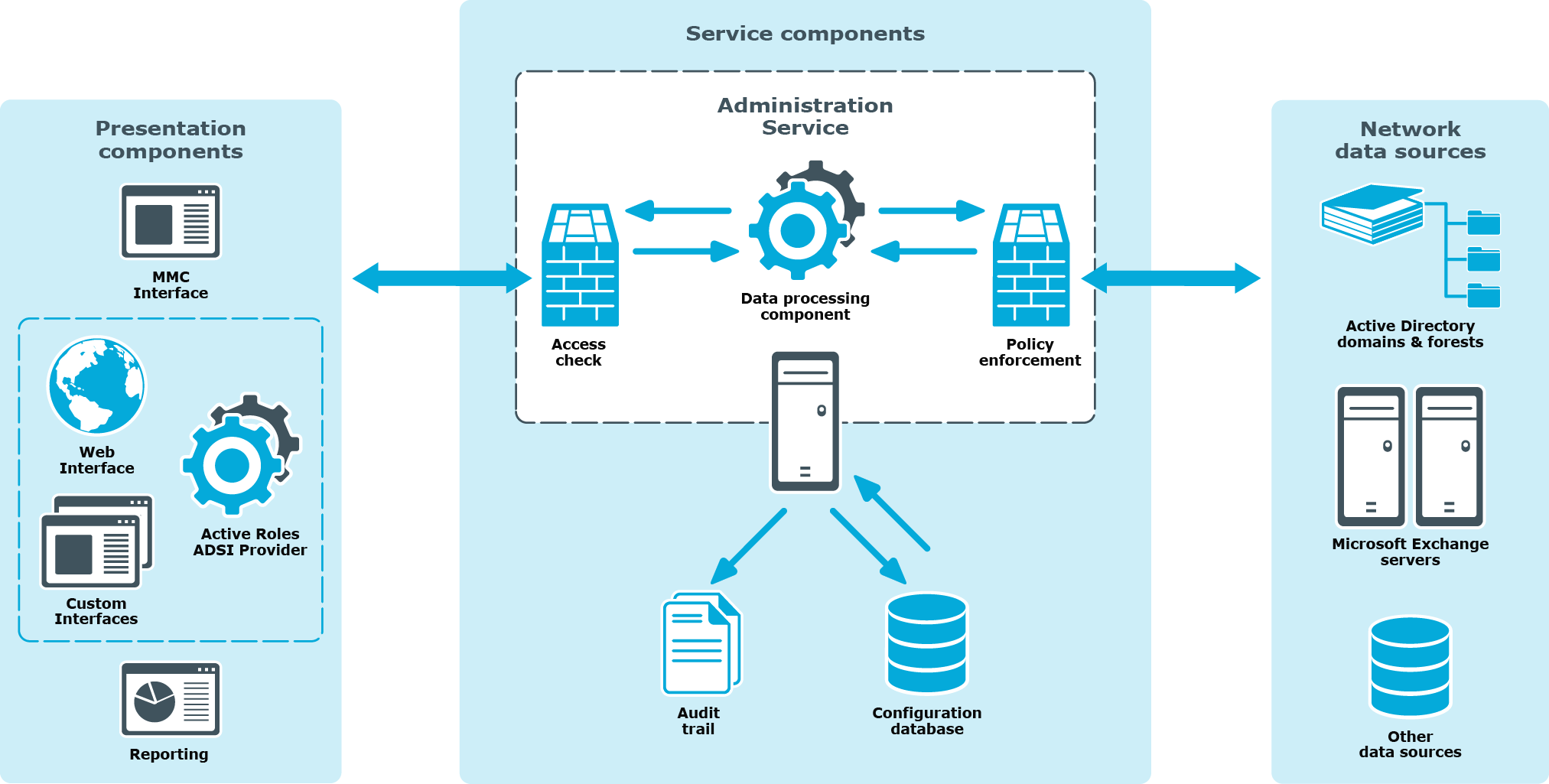
The presentation components include client interfaces for the Windows platform and the web, which allow regular users to perform a precisely defined set of administrative activities. The reporting solution facilitates automated generation of reports on management activities.
The service components constitute a secure layer between administrators and managed data sources. This layer ensures consistent policy enforcement, provides advanced automation capabilities, and enables the integration of business processes for administration of Active Directory, Microsoft Exchange, and other corporate data sources.
The Administration Database stores information about all permission and policy settings, and other data related to the Active Roles configuration.
On a very high level, the Active Roles components work together as follows to manipulate directory data:
-
An administrator uses the Active Roles Console or Web Interface to access Active Roles.
-
The administrator submits an operation request, such as a query or data change to the Administration Service.
-
On receipt of the operation request, the Administration Service checks whether the administrator has sufficient permissions to perform the requested operation (access check).
-
The Administration Service ensures that the requested operation does not violate the corporate policies (policy enforcement).
-
The Administration Service performs all actions required by the corporate policies, before committing the request (policy enforcement).
-
The Administration Service issues operating system function calls to perform the requested operation on network data sources.
-
The Administration Service performs all related actions required by the corporate policies, after the request is processed by the operating system (policy enforcement).
-
The Administration Service generates an audit trail that includes records about all operations performed or attempted with Active Roles. Directory-change tracking reports are based on the audit trail.
The following section describe the three component layers in more detail.

