You can set up a firewall between Active Roles client components, such as the Active Roles Console (also known as the MMC Interface), Web Interface, ADSI Provider or Management Shell, and the Active Roles Administration Service.
To access the Active Roles Administration Service with the Active Roles client components through a firewall, you must open port 15172 and all high ports (1024-65535) on port 15172 in the firewall. The client machines randomly select high ports to use for outgoing traffic on port 15172 to access the Active Roles Administration Service.
To give access to the Active Roles Administration Service through a firewall
-
In the firewall, open port 15172 TCP Inbound/Outbound.
NOTE: For more information about opening ports in your firewall, refer to the operating system's or the network device vendor's documentation.
-
In the firewall, open the high ports (port range 1024-65535) on port 15172.
NOTE: To check the list of high ports being used on port 15172, in the Active Roles Console of a client machine, use the netstat -an command.
If you want to access the Active Roles Web Interface through a firewall, then you need to open the following ports:
- Port 80 (Default HTTP) TCP Inbound/Outbound
- Port 443 (Default HTTPS) TCP Inbound/Outbound
The Web Interface normally runs over port 80, or over port 443 if SSL is enabled (off by default).
Active Roles supports 3 different Azure environment configurations: Non-federated, Synchronized identity, and Federated.
Non-federated
In a non-federated environment, the on-premises domains are not registered in Azure AD, and neither Azure AD Connect nor any third-party synchronization tools are configured in the domain for synchronization. In non-federated environments, the changes made in Active Roles are immediately replicated to Azure or Office 365 using Graph API Calls or Command-let calls. Users or Guest Users are typically created in Azure with the onmicrosoft.com UPN suffix.
Example: Non-federated environment configuration
A non-federated environment may have the following settings:
-
On-premises domain: test.local
-
Azure AD Domain: ARSAzure.onmicrosoft.com
-
Azure AD Connect is not configured for synchronization.
The on-premises domain is not registered in Azure. The user or guest user is created in Active Roles with the ID of user001@test.local and in Azure as user001@ARSAzure.onmicrosoft.com. The user is created in Azure simultaneously when it is created in Active Roles using a GRAPH API call.
NOTE: One Identity recommends using non-federated environments for testing purposes only, and does not recommend setting them up as a live production environment.
Synchronized identity
In a Synchronized identity environment, the on-premises domain is optionally registered in Azure AD, while Azure AD Connect is configured to synchronize the local AD objects to Azure. Azure Users or Guest Users are typically created either with the selected on-premises domain or with the onmicrosoft.com UPN suffix.
Figure 148: Synchronized identity configuration
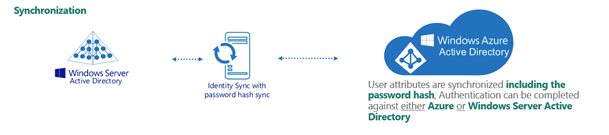
Example: Synchronized identity configuration
A synchronized identity environment may have the following settings:
-
On-premises domain: test.local
-
Azure AD Domain: rd4.qsftdemo.com
-
Azure AD Connect is configured for synchronization.
The on-premises domain is optionally registered in Azure. The user is created in Active Roles with the ID of user001@test.local and in Azure as user001@rd4.qsftdemo.com.
Federated
In a federated environment, the on-premises domain is always registered in Azure AD, while Azure AD Connect and Active Directory Federation Services (ADFS) are configured to facilitate synchronization. Users and Guest Users are typically created with the UPN suffix of the selected on-premises domain.
Figure 149: Federated configuration
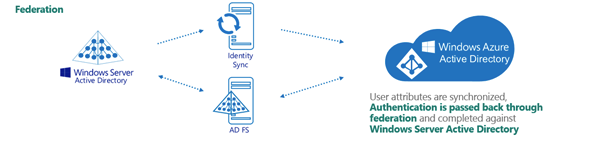
Example: Federated configuration
A federated configuration may have the following settings:
-
On-premises domain: rd4.qsftdemo.com
-
Azure AD Domain: rd4.qsftdemo.com
-
Azure AD Connect and ADFS are configured for synchronization.
The on-premises domain is registered and verified in Azure. The User is created in Active Roles and Azure AD with the same ID of user001@rd4.qsftdemo.com.
This section provides information about the supported operations and methods for performing the operations for Azure objects in various Azure environments using Active Roles Web interface, such as Federated, Synchronized Identity, and Non-Federated environments.
In Active Roles Web interface, the required Azure environment configuration can be selected during the Azure tenant creation. The specified configuration can be modified later if needed by changing the Azure properties of the tenant.
Active Roles identifies the environment based on the Azure Tenant type and applies the changes to the Web interface.


